
Convincing the board to invest in any cybersecurity solution is often an uphill climb.
A study conducted by IANS showed that CISOs’ annual budget cycles have decreased by 4% YoY as of 2025, with 54% reporting flat or shrinking budgets. Adding “another SOC tool” might not be at the top of the board’s priority just yet, if in fact at all.
But there is a more effective way to get the board on your side. This blog will help you develop a winning strategy for justifying budget approval for upgrading your SOC maturity.
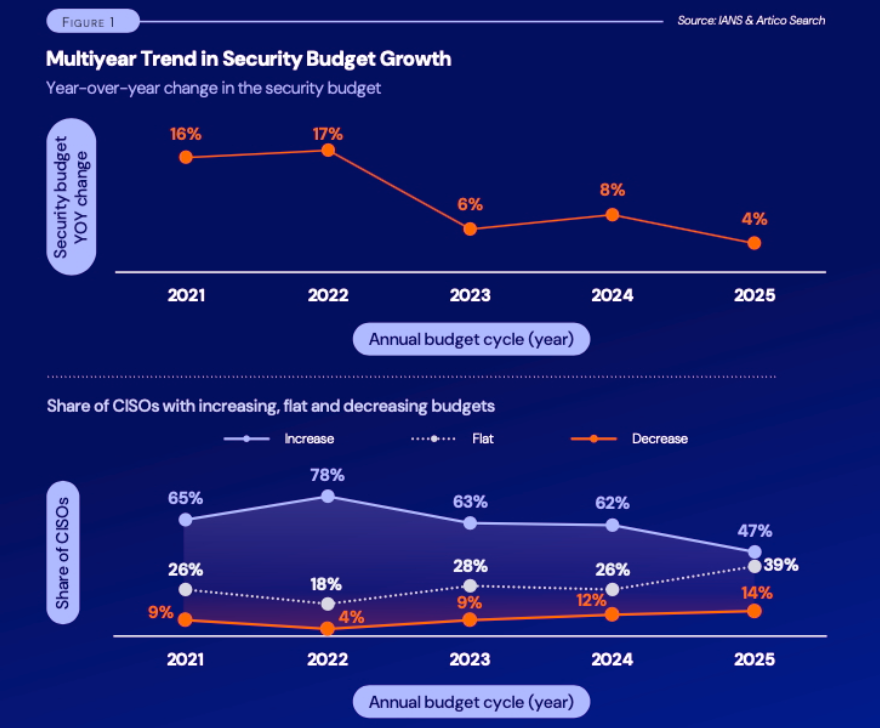
Figure 1. Multiyear Trend in Security Budget Growth by IANS
Understanding the levels of SOC maturity
Gone are the days of manual triage, when analysts spent hours and even days sifting through threat intelligence reports and chasing false positives, which fueled alert fatigue, delayed incident response, and wasted valuable mitigation efforts on low-priority threats.
Not only did these processes prove to be highly ineffective, but they also accelerated analyst burnout and left many critical threats undetected. Research showed that 71% of SOC practitioners worry they will miss a real attack buried in a flood of alerts. SOC maturity has evolved through many stages since then.
Rule-based solutions, such as User and Entity Behavior Analytics (UEBA), marked the next step in the SOC maturity ladder. They were integrated with SIEM tools to enhance threat detection capabilities by identifying unusual patterns and anomalous user behavior. UEBA provided a bit more depth for security teams, particularly with machine learning capabilities, but was limited by predefined static rules, complex deployment, and time-consuming behavioral baselining. SOAR missed the mark with its inability to interpret the “thinking tasks” or understand the context behind the risk, applying more pressure to SOC workflows.
AI has completely redefined the SOC. Gartner predicts that “by 2026, AI will increase SOC efficiency by 40% compared to 2024 efficiency, beginning a shift in SOC expertise toward AI development, maintenance, and protection.”
Analysts today leverage DIY AI to handle repetitive tasks, correlate log data, and parse through large volumes of threat intelligence for faster detection and more informed decision-making during investigations. But AI models are prone to hallucinations and carry security and compliance risks, as they may generate inaccurate outputs, expose sensitive data, or fail to meet regulatory requirements.
A recent study conducted by Splunk found that only 11% of security professionals say they trust AI completely to perform mission-critical activities in the SOC.
Not exactly the type of reassurance SOC teams need to keep threat investigations in autonomous mode.
This brings us to the next level of SOC maturity, commercial AI SOC platforms.
Commercial AI SOC platforms offer more with built-in compliance and security guardrails, along with a human in the loop for validating the severity of threats, fact-checking the accuracy of AI-generated insights based on experience, and making context-driven decisions. But most commercial AI SOC platforms can only handle a limited set of alert types, struggle to understand business context for prioritizing threat mitigation, and are constrained to specific security use cases.
However, an adaptive AI SOC can handle all alert types from any source and offers integrated and affordable logging to offset the high cost of data management. It has the capability of providing context behind every step of alert triage and response with complete reasoning. This level of maturity gives the board the type of ROI needed to justify the investment.
But what about a SOC that contextually processes threat intelligence from multiple sources, with human-level reasoning and decision-making capabilities?
Enter the next phase of the SOC evolution. Artificial General Intelligence (AGI).
Imagine an autonomous SOC capable of identifying new attack techniques, distinguishing context-driven threats, and applying human-level reasoning without any analyst input. It sounds almost too good to be true, but there are considerations centered around AI governance, data protection, accountability, and bias. But the thought of a fully autonomous SOC might be a reality someday.
Figure 2. SOC maturity model
| Level 0 Manual operations | Level 1 Rule-based defence | Level 2 Do-it-yourself AI | Level 3 Commercial AI SOC platforms | Level 4 The potential future of SOC with AGI |
| Overview Analysts manually triage alerts, investigate threats manually, and coordinate responses without the support of modern security solutions, such as a SIEM, SOAR, or XDR. | Overview SOCs begin to implement rule-based solutions, such as UEBA, to prioritize threats through risk scoring and assist with triage. | Overview AI is integrated into SOC workflows to enhance threat hunting, log correlation, and incident summary, freeing up analyst time to focus on business-critical initiatives. | Overview Advanced SOCs leverage commercial AI platforms to automate triage, accelerate response time, and reduce analyst workload. However, pre-trained models are limited and can only triage what they have been taught to recognize. | Overview The next level in the SOC maturity evolution may lie with Artificial General Intelligence (AGI), where the SOC can autonomously identify advanced attack techniques and patterns, ingest vast amounts of historical threat data, and reason through complex scenarios without human intervention. |
Framing the conversation for the board in business terminology
The board might not necessarily be interested in knowing about the technical intricacies of UEBA behavior baselining or the specifics of an AI agent summarizing incident data from past threat investigation reports. But they certainly do care about business metrics and whether that cybersecurity solution can reduce organizational risk, rather than add to it.
Business-driven SOC metrics can help justify your case for upgrading SOC maturity and bridge the barrier with the board. KPIs such as reduced Mean Time to Detect (MTTD), increased Mean Time to Resolution (MTTR), and lower False Negative Rates (FNR) all provide quantifiable proof of SOC efficiency and ROI. This enables analysts to focus on high-priority initiatives that directly impact business objectives, while the board can see actual results.
Business KPIs are the foundation for success. They demonstrate actual value while fostering stronger relationships built on trust. CISOs with good board relationships are more likely to be given the ability to pursue use cases for generative AI, such as creating threat detection rules (43% versus 31% of other CISOs) and proactive threat hunting (46% versus 28% of other CISOs).
And by extension, that level of trust translates to continued support for cybersecurity initiatives, including upgrading SOC maturity.
How to build a winning cybersecurity strategy with an adaptive AI SOC
An adaptive AI SOC platform can bring you closer to getting a “yes” during your next board review by accelerating those KPIs while keeping headcount steady. Adaptive AI leverages semantic classification to determine how closely a new alert matches previous ones, giving SOC teams the context they need to prioritize threat remediation efforts.
Radiant Security automatically triages 100% of alert types from any data source or vendor. Analysts can ingest unlimited log management data from any source without additional costs, slash MTTR from days to minutes, while delivering a 1,000% boost in productivity.

Radiant’s ultra-affordable log management enables SOC teams and CISOs to ingest all security data with unlimited retention without restrictive vendor lock-in or the high costs of traditional SIEM solutions. With an adaptive AI SOC, the investment becomes clearer and more strategic rather than a risk.
Show the board how they can support your cybersecurity initiatives. The ultimate guide to SOC maturity provides all the actionable steps needed to convince them further.
Ready to level up your SOC maturity?
Back



