Adaptive AI SOC Platform
Automated triage and response for the broadest range of security alert types and use cases.
Zero pre-training required.
How it Works
Radiant’s AI SOC platform ingests all alert types and telemetry data from any source, autonomously triaging every alert and investigating the potential impact across your entire environment. Only real threats are escalated to incidents with transparent response recommendations generated for your human analyst to review and execute in one click.
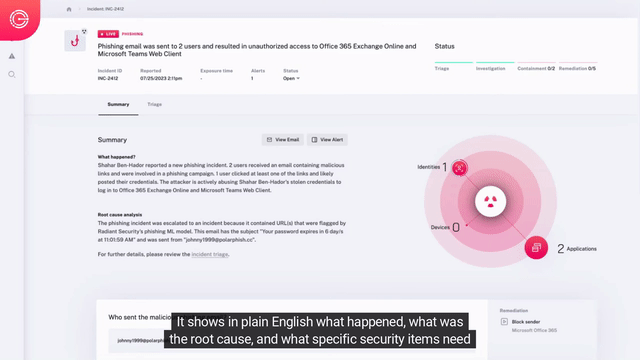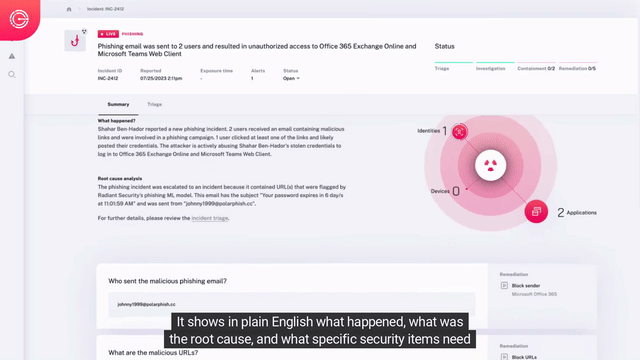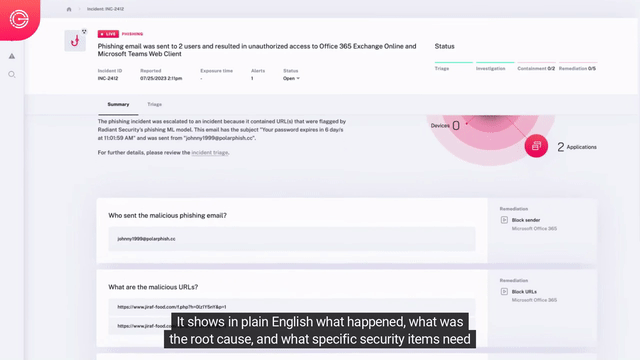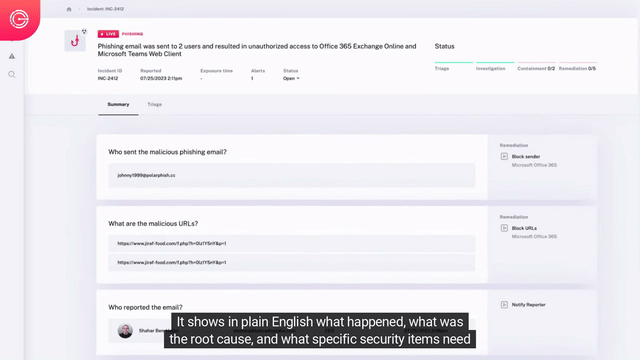
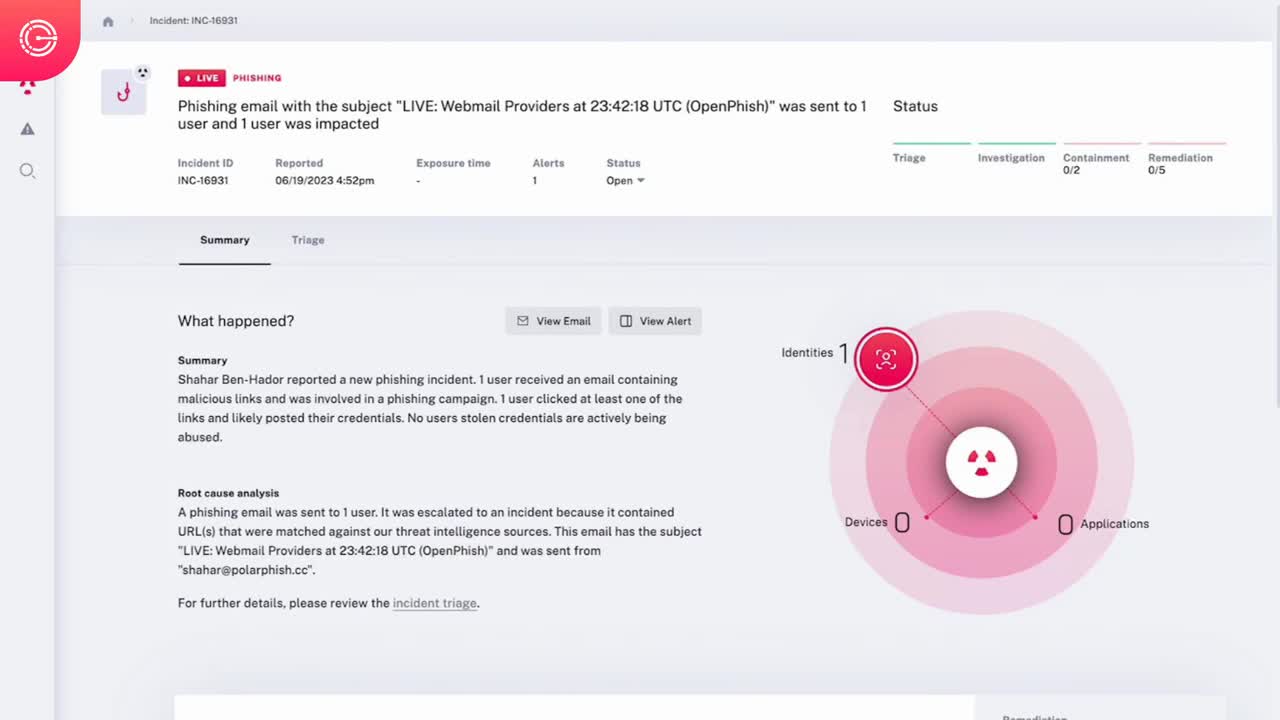
Every Alert. Complete Context. Zero Noise.
Automated Detection, Triage, & Investigation
- Automated Triage – Inspection of all alerts, with up to hundreds of tests dynamically performed to determine if an alert is malicious.
- Impact Analysis – Analysis of alerts deemed malicious to understand detected issues’ root cause and complete incident scope with all affected users, machines, applications, and more.
- Data Stitching – Ingestion and correlation of all alert types and telemetry data from any source ensures comprehensive investigation of attack path, so nothing is missed.
Rapid Containment & Remediation
- Incident specific response – Dynamic generation of transparent remediation response based on the specific needs of the security issues uncovered during incident impact analysis.
- Response automation – Human analysts can review the recommended actions and choose whether to fully automate or manually perform them for rapid, effective remediation and containment.
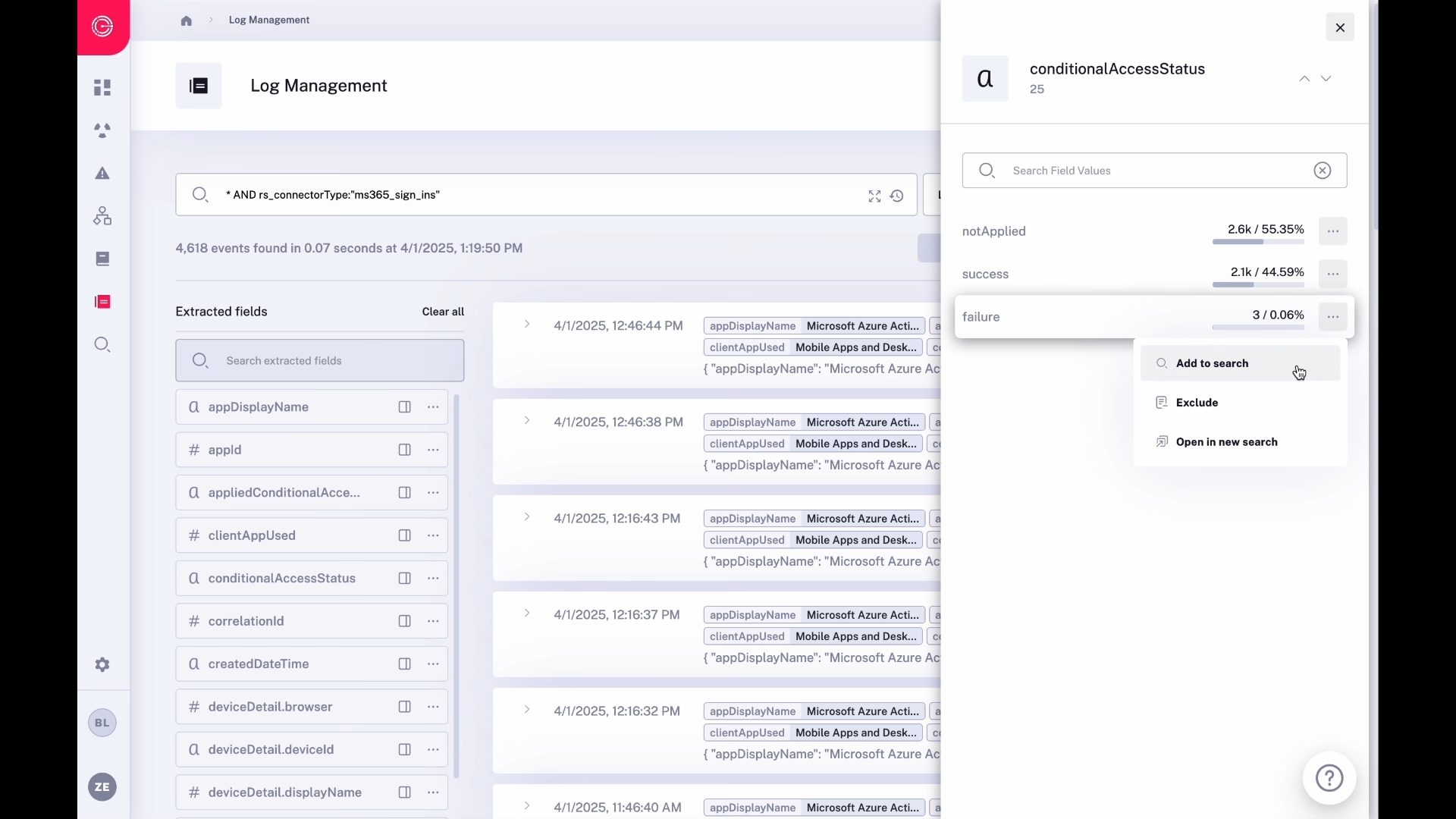
Integrated Data Lake
- Ingest all your security data with unlimited retention for compliance and forensic investigations.
- Deep-dive directly from incident summaries into the relevant logs with lightning fast querying and visualizations.
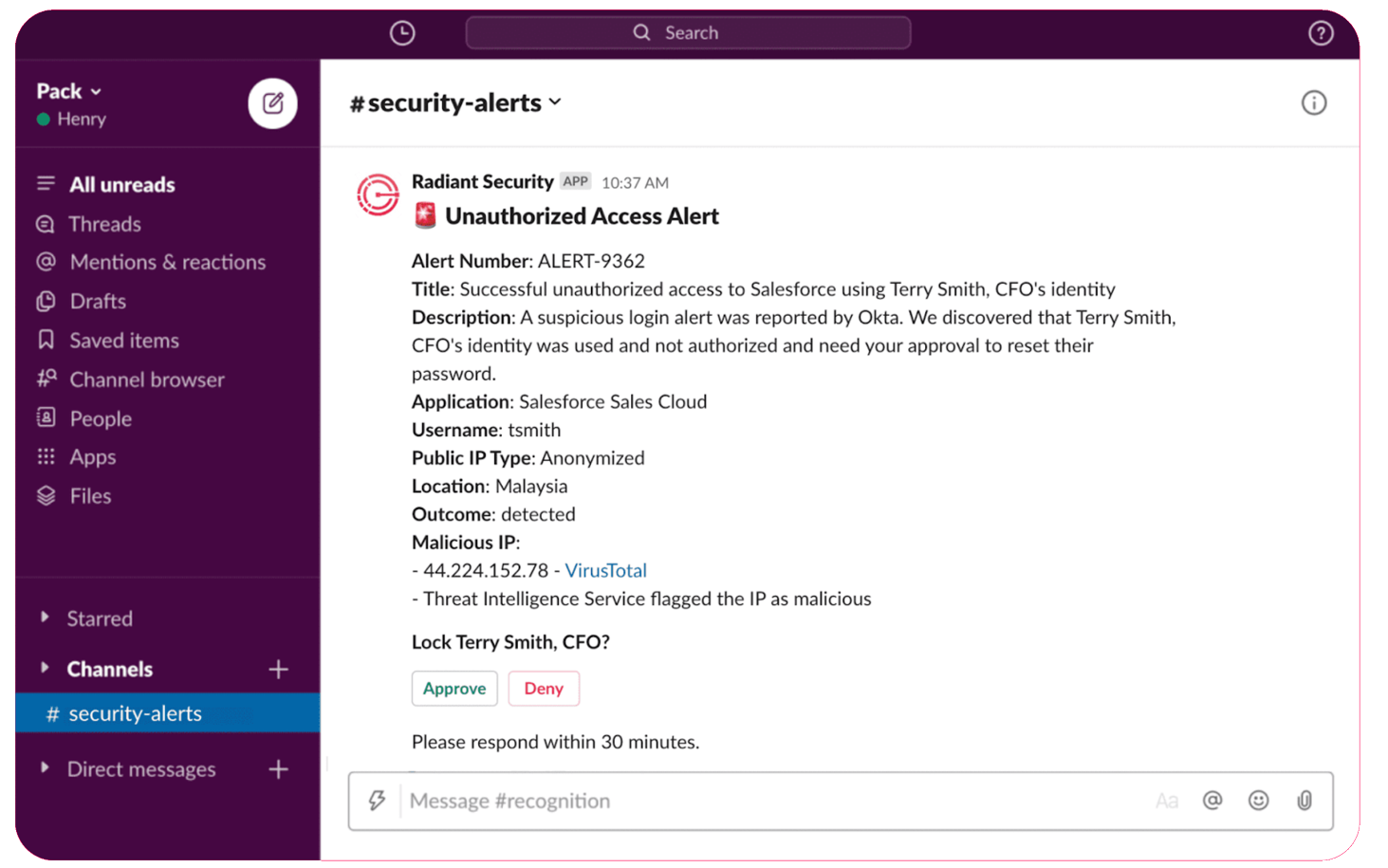
Escalations & Approvals
Taking corrective actions to address an incident often involves tasks which require approval, such as disabling an account or isolating a device from the corporate network. Radiant can automate your existing escalation chains and approval processes to efficiently obtain permission to perform corrective actions.
Communication Workflows
Automatically keep affected users, and stakeholders informed by leveraging your existing productivity tools (e.g., Slack, Teams, Email, etc.) for seamless communication. This ensures rapid response and uninterrupted workflows, to keep your team moving and your response times low.

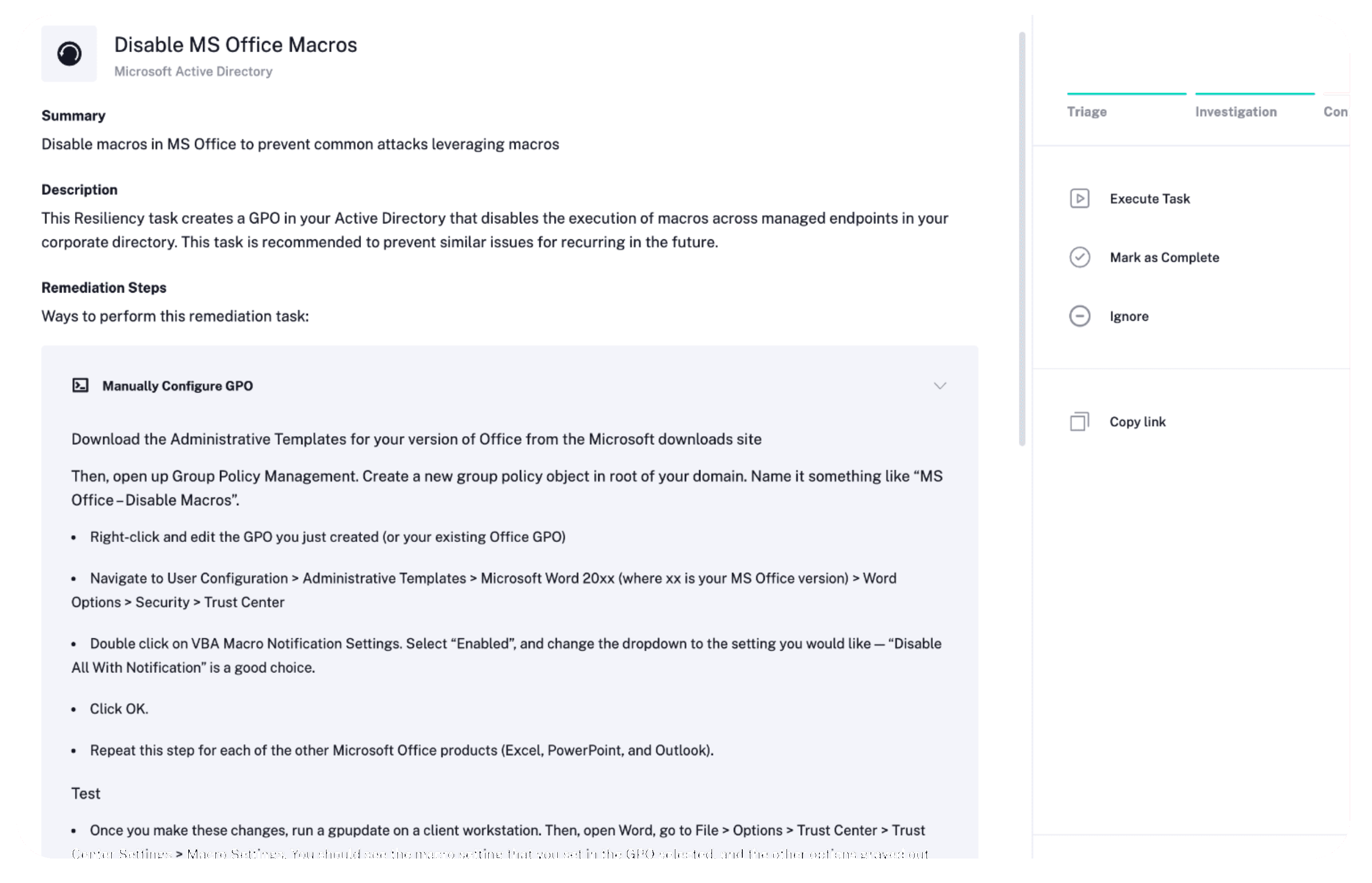
Resiliency Improvement
After an incident has been handled, it’s important to improve your security posture. As part of each incident’s custom response plan, Radiant automatically recommends actions that can be taken to enhance your environment’s resiliency against similar threats, reducing the likelihood of future incidents of the same nature.
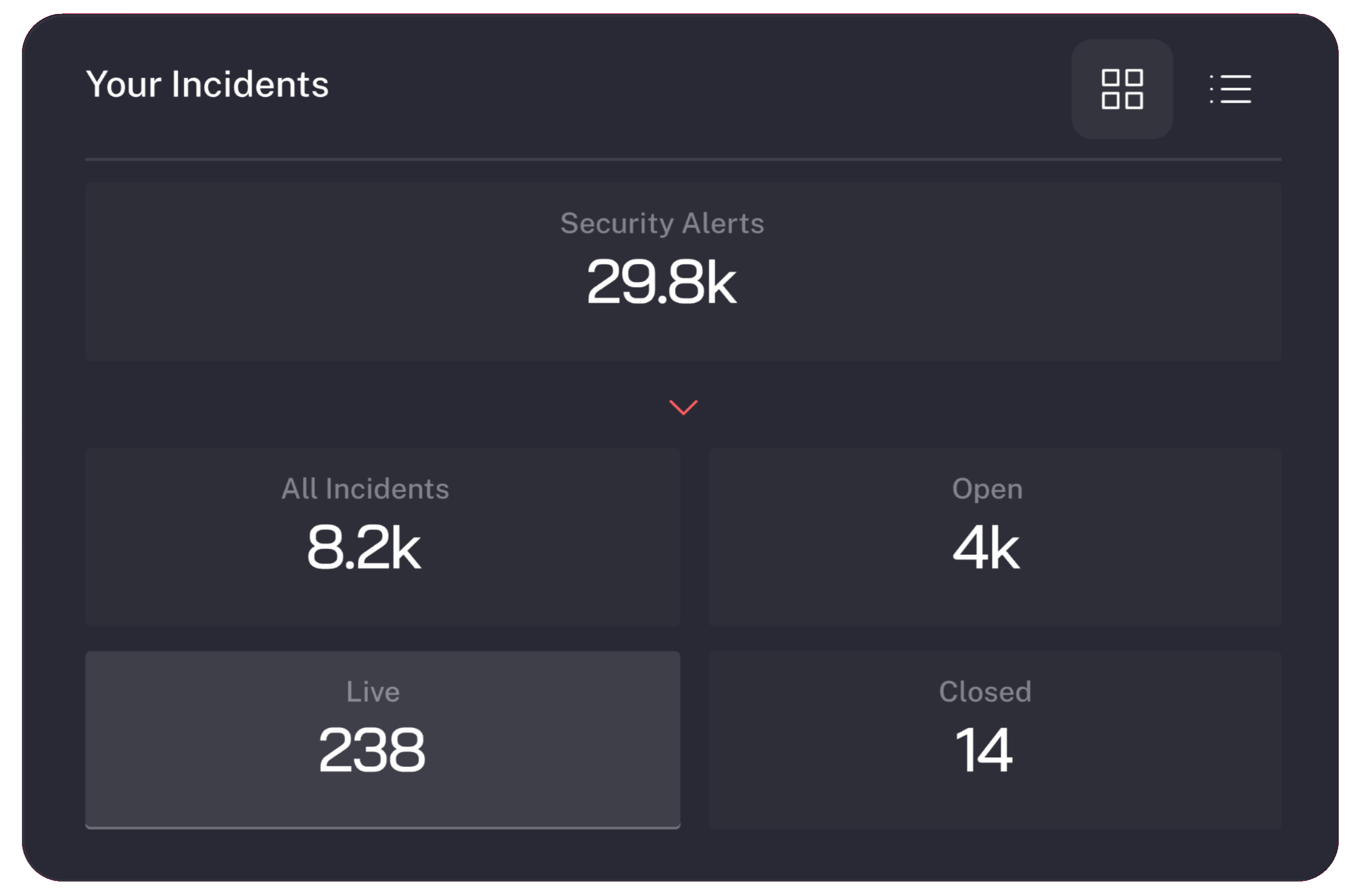
What You Get
-
Quick time-to-value
Deployment takes minutes with the AI SOC platform immediately yielding results similar to a seasoned analyst familiar with your environment.
-
Deep Security Expertise
Our system automatically adapts to evolving threats so that incidents are always handled with current best practices.
-
Reduced Workloads
Automating triage and investigation reduces analysts workloads by as much as 95%.
-
Peace of Mind
Every single alert is triaged until it’s found to be malicious or benign. Nothing slips through the cracks.
-
Higher Quality Results
Every incident is triaged and investigated consistently, in a data driven way, equal to the work of your best analyst.
-
Log Management. No Extra Cost.
Radiant’s modern architecture delivers the log management capabilities that SOC teams need. Without the prohibitive cost of traditional SIEMs.