Company Profile
Kyowa Kirin is a global specialty pharmaceutical company headquartered in Tokyo, Japan, with over 7,000 employees worldwide. They emphasize cutting-edge research and patient-centric solutions to improve quality of life with innovative oncology, nephrology, immunology, and neurology therapies. The company is part of the Kyowa Hakko Kirin Group.
The Challenges: Detecting true incidents in a sea of 1000s of alerts with limited SOC resources
As a large global enterprise, Kyowa Kirin’s challenge was dealing with a constantly growing, comprehensive, and challenging attack surface.
Managing and protecting tens of thousands of digital assets from malicious attacks was highly challenging and inefficient due to the large number of attack vectors that can be exploited and the number of security tools needed for security operations.
The Threat Detection systems in place to protect the ever-growing attack surface generated an overwhelmingly high number of alerts. This never-ending onslaught of alerts created a natural bottleneck within the SOC due to manual, time-consuming investigation and response processes.
The combination of limited resources, handling too many tools with too many alerts resulted in slow response times, which created an unnecessary security risk that didn’t reflect the high standard they were striving for.
Increasing SOC headcount to solve their resources challenge was not a feasible solution due to:
- Talent shortage – It’s extremely challenging to find, train, and retain experienced security professionals to staff the SOC.
- Exorbitant costs – Expanding an in-house SOC is costly and not scalable.
- Inconsistent quality – Incident triage, investigation, and response results vary dramatically depending on which analyst handles an incident and their skill, knowledge, and experience level.
Eric Sanchez, Global CISO at Kyowa Kirin, sought a technological solution to handle the large number of alerts faster, more efficiently, and with the highest quality.
“As our attack surface exponentially grew with the company’s scale, hiring more security professionals to investigate and resolve more false positive alerts was not the ideal solution I was looking after.”
Radian’t Solution: AI SOC Analysts that autonomously triage, investigate and resolve any number of Tier I security alerts
After exploring several competing solutions that didn’t provide the value and standard they were thriving for, and following a successful POC (proof of concept), Eric chose Radiant Security to help Kyowa Kirin’s SOC team swiftly and automatically triage, investigate, and resolve their high number of tier I alerts without increasing headcount.
About Radiant Security
Radiant Security is an AI-powered platform that autonomously triages, investigates, and responds to security alerts, empowering security teams to address all received alerts. With complete impact and root cause analysis, Radiant provides effective, automated remediation that can be setup in minutes via APIs and reduces workloads by up to 95%.
The onboarding process of integrating with existing systems was a smooth, short, and effortless sail. Within 30 minutes of the onboarding, Radiant was already providing value by detecting a true positive incident by a threat actor they didn’t even realize was targeting them.
Radiant Security’s AI SOC analysts immediately minimized the “noise” level by reducing the number of alerts the SOC team has to handle.
The platform’s triage and investigation capability helps Kyowa Kirin automatically resolve alerts at any scale, faster, with the quality of their best analyst.
“Within 30 minutes of onboarding, Radiant was already able to detect a true positive threat. We had not ever seen anything happen that fast, and that showed us how effective the platform truly was.”
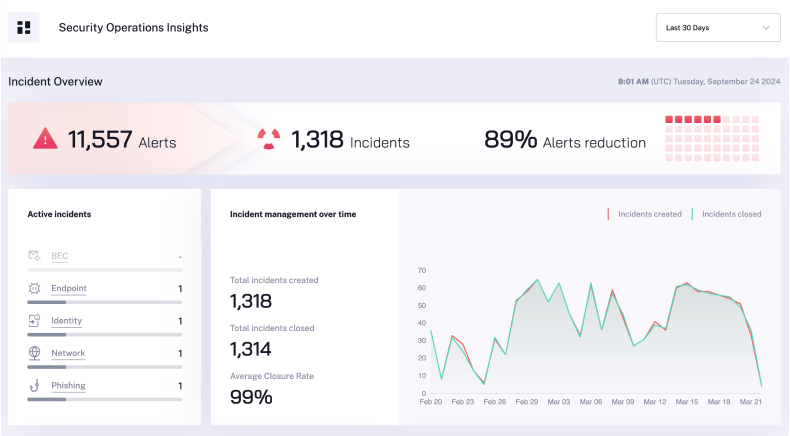
The Results: Enhanced security posture and minimized the attack surface without increasing SOC headcount
Radiant Security’s AI SOC Analysts removed the SOC resource bottleneck, freed up analysts, and enabled Kyowa Kirin to:
- Reduce MTTR from days to hours, despite an ever-growing attack surface.
- Improved their threat detection by automatically finding true attacks in a sea of false positives
- Resolve alerts faster without increasing headcount.
- Focus their time and resources on the real threats so incidents won’t become breaches.
- Have peace of mind, knowing that every alert is always being handled correctly.
“From a personal standpoint, they’ve created a partnership Kyowa Kirin can be proud of. Talking directly to the founders gives me the assurance I need because they are putting themselves on the line, and that’s the kind of partner I can trust”
