Blog
Insights for the modern SOC
Actionable thinking for teams that want more from their security stack.

All
AI
All Categories
Amazon S3
API Security
Business Apps
CDN & Edge
CISO
Cloud
Company News
CSPM
Database Security
Detection tools
DevSecOps
DLP & Data Security
EDR
EDR
Email & Training
Firewalls & Network
IAM
IDS/IPS
Logging & Data Pipeline
MDR
NAC
NDR
OT/ ICS
Phishing
SASE
Security Automation
Security Operations
SIEM
SOAR
SOC Operations
SWG & Proxy
Threat Intelligence
VPN & ZTNA
Vulnerability Management
WAF
Continuous feedback loops: Why training your AI-SOC doesn’t stop at deployment
A pre-trained AI-SOC can perform on day one and fail by day ninety. Static models can’t keep up with changing behavior or new threats. A continuously learning AI-SOC can. This article shows how feedback loops turn AI into a true member of the team.

What Happens to MSSPs and MDRs in the Age of the Al-SOC?
MSSPs and MDRs filled a gap, but AI-SOC platforms now let security teams bring more capability in-house. This article explores how AI-driven triage and correlation change cost, visibility, and response for organizations reconsidering managed security.

The buyer’s guide to evaluating an AI-SOC platform
Not all AI-SOC providers are created equal. This guide shows you how to choose the right vendor for your organization and what you need to consider when it comes to architectures, adoption models, risks, and the questions leaders should ask.

AI in the SOC: The trade-offs of training on customer data
The pros and cons of training Agentic AI SOC on customer data.

Implementing a modern SOC: Overcoming the challenges
Facing SOC challenges head-on: Tools, talent, AI, and tactics that actually work.

SOC for all: why every company can now afford one
SOC capabilities aren’t just for the Fortune 500 anymore. Here’s how AI and new models are making them accessible to everyone.

AGI and the future of SOC
Will AGI deliver on its promise or cause more challenges?
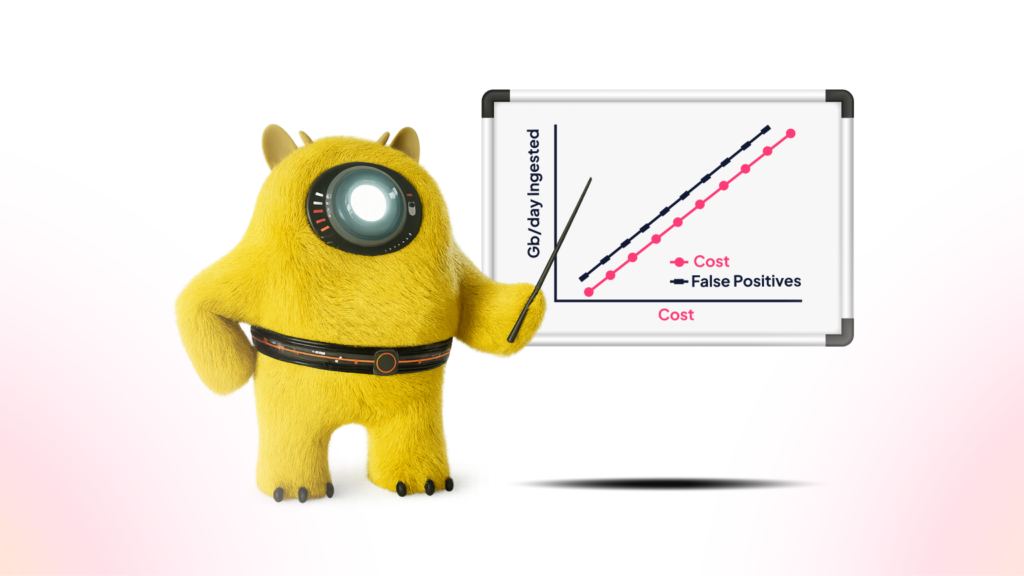
The toll of useless alerts: Why SIEMS no longer make sense
SIEMs flood SOC teams with noise and cost. Here's how to take back control, and focus on what really matters.

SOC burnout and how AI can flip the script
Stay updated on current burnout trends for SOC teams and how AI can eliminate this challenge.