In a recent multi-company phishing campaign, threat actors targeted high-level executives, CEOs, SVPs and finance managers, across several Radiant customers. The attacks bypassed many leading tools that were deployed at these customers, including CrowdStrike, Darktrace, Google Workspace, Microsoft O365, Proofpoint, SentinelOne, Microsoft Defender, and ZScaler.
Despite the threats going unblocked, the experienced SOC teams at each of those companies were able to immediately find the malicious activities and fully remediate the attacks.
While this story had a positive outcome, it serves as a powerful reminder of several key lessons. First, even with comprehensive security training and sophisticated protective measures in place, employees can remain a vulnerable entry point in any organization’s cybersecurity defenses. Human error or oversight continues to be a major risk factor.
Second, it’s important to acknowledge that cyberattacks can still evade even the most advanced detection tools available today. No solution is infallible, and relying solely on technology can leave dangerous gaps.
Finally, the human SOC team remains the cornerstone of any effective security strategy. Their ability to provide thoughtful analysis and respond creatively to real threats is invaluable. As such, they should be supported and empowered to concentrate their efforts on meaningful, high-impact work.
Now for the story.
The threat that almost slipped through
The phishing email in question was sent from noreply@increasinghope.org which does appear to be the domain of a legitimate organization and the domain hadn’t previously raised red flags in any major threat intelligence feeds. It is likely they themselves were hacked and their domain hijacked for these email attacks.
The content of the email was not some sophisticated phishing attack. In fact, there were many red flags such as a fake looking Microsoft heading and the email clearly not being from Microsoft, grammatical errors, a voice message from a blocked phone number and more.
Yet, it made its way directly into the inboxes of C-level executives and finance professionals at several companies without being blocked by any of the above mentioned tools.
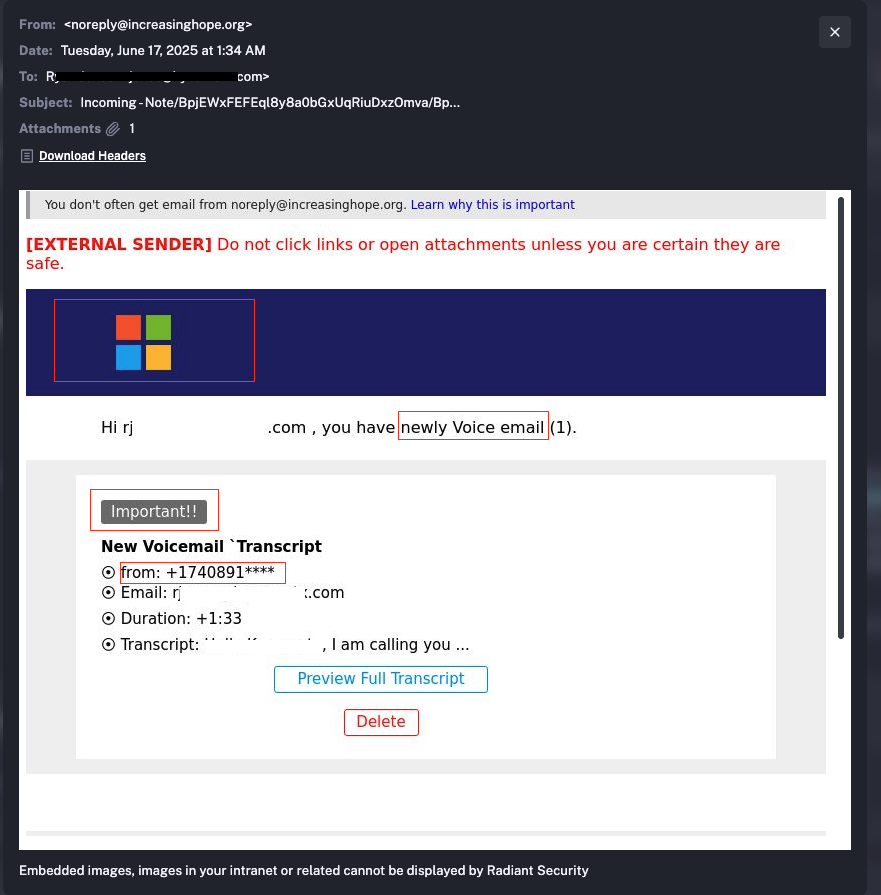
Fortunately, multiple executives and other employees did notice the various oddities about the email and reported them in Radiant.
Our adaptive AI, leveraging contextual enrichment and sentiment analysis, flagged the email alerts as true positives, checked organizational impact including who else received or clicked on the email and escalated them to the respective SOC teams who were able to review the triage and investigation.
Radiant also provided the SOC analysts with integrated response capabilities, such as blocking the sender domain, hard-deleting malicious email from all inboxes and more with just a single click per action.
Credential use unmasks compromised IP
But it didn’t end there. Credentials entered on the attacker’s site were detected by Microsoft as they were being used in a login attempt from the IP address 2a05:541:116:25::1 which is a datacenter IP located in Arizona. Radiant’s adaptive AI flagged the identity alert as malicious based on its anomalous geolocation and timing, and escalated the alert with full context. Although the credentials were valid, the login was blocked by MFA, preventing account access. From there, Radiant’s platform automatically correlated the event with the broader phishing campaign and surfaced recommended remediation actions thus enabling the affected customer to contain the threat.
Multi-layer defense is the name of the game
We believe the main takeaways from this story are as follows:
- While completely essential for blocking the vast majority of attacks, even the best security tools are not foolproof.
- Even though employees can unwittingly contribute to organizational risk, if well-trained in security precautions, they may play an important role in a company’s defense.
- Last but not least, human SOC analysts are the most critical asset in any company’s arsenal against cyber attacks as only they can provide the highest quality analysis and resolution of any event. As such they should be equipped with tools that boost their effectiveness and allow them to fully focus on identifying and resolving real threats.
Furthermore, we recommend that all organizations take the following steps to protect themselves from this potential phishing attack:
- Review email logs: Look for emails from the domain mentioned above, particularly those sent to your C-suite or finance team. Thus far, targets were exclusively senior executives and finance leaders.
- Search sign-in logs thoroughly: Use your identity provider’s logs to identify both successful and failed login attempts from the IP
2a05:541:116:25::1or other suspicious locations. Don’t rely solely on blocked logins from Conditional Access or MFA—check for cases where credentials were successfully validated, even if the session was ultimately denied. This is a strong indicator that credentials have been compromised and immediate action (e.g. forced password reset, session termination) may be required. - Review email and proxy logs: Search email security logs for messages sent from the domain increasinghope.org, as this domain was abused during the phishing campaign.
- Review proxy or firewall logs for any access to malicious URLs contained within those emails, as they may have redirected victims to malicious credential-harvesting sites. Users who interacted with these emails or sites should be considered at risk, and credentials should be reset accordingly.
- These are the malicious URLs observed by Radiant and should be blocked:
- a.dorotheabernique.com
- s7i4h.mjt.lu
- These are the malicious URLs observed by Radiant and should be blocked:
- In the event the above email landed in employee inboxes, take proactive steps:
- Block the sender domain.
- Hard-delete any phishing emails.
- Reset credentials for affected users.
- Enable conditional access policies and MFA for all executives.
More about Radiant
Radiant’s AI SOC platform is built on adaptive AI—not brittle, pre-trained models—enabling it to triage any alert type out of the box, no setup, tuning, or use-case-specific training required. While legacy vendors struggle to keep up with evolving threats, Radiant dynamically investigates novel alerts in real time, using a system of collaborating AI agents and multiple LLMs to deliver deep, accurate triage at scale.
Once a threat is identified, Radiant offers one-click—or fully automated—remediation with no playbook configuration or maintenance required. And with integrated, ultra-affordable logging built on your cloud archive, analysts can instantly pivot from alert to root cause without SIEM complexity or cost. The result: faster detection and response with complete visibility!
See a demo to learn how Radiant can protect your team today!





