The SOC has evolved. AI is now a key driver for alert triage and more effective threat mitigation. Research shows that 63% of analysts report AI is improving investigation accuracy, while 60% say it has enabled them to focus more on strategic decision-making.
The ultimate guide to SOC maturity whitepaper outlines the shift from manual threat investigations to DIY AI models and fully autonomous Artificial General Intelligence (AGI) with human-level reasoning.
While the advancement of AI has been a catalyst for SOC progression, it’s not the only factor that determines success.
This summary explores the various challenges SOC teams face, along with AI considerations as you progress your SOC maturity. Here’s what you need to know.
SOC maturity model – Linear growth progression
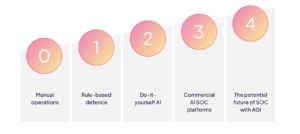
| Level 0 | Level 1 | Level 2 | Level 3 | Level 4 |
| Manual operations | Rule-based defence | Do-it-yourself AI | Commercial AI SOC platforms | The potential future of SOC with AGI |
| Analysts manually triage alerts, investigate threats manually, and coordinate responses without the support of modern security solutions, such as a SIEM, SOAR, or XDR. | SOCs begin to implement rule-based solutions, such as UEBA, to prioritize threats through risk scoring and assist with triage. | AI is integrated into SOC workflows to enhance threat hunting, log correlation, and incident summary, freeing up analyst time to focus on business-critical initiatives. | Advanced SOCs leverage commercial AI platforms to automate triage, accelerate response time, and reduce analyst workload. However, pre-trained models are limited and can only triage what they have been taught to recognize. | The next level in the SOC maturity evolution may lie with Artificial General Intelligence (AGI), where the SOC can autonomously identify advanced attack techniques and patterns, ingest vast amounts of historical threat data, and reason through complex scenarios without human intervention. |
Challenges SOC teams face
SOCs are coupled with a myriad of challenges, which include alert fatigue, a lack of context for threat mitigation, and budget constraints. Here’s what else we discovered:
- Over half of security leaders (55%) feel satisfied with the cost aspect of their SOC, indicating room for improvement – Gartner Peer Community
- SOC teams receive an average of 4,484 alerts per day and spend up to 3 hours manually triaging them – Security Magazine
- Up to 30% of a SOC analyst’s time is lost chasing false positives due to a lack of context – The Hacker News
- Security analysts are unable to deal with 67% of the daily alerts received, with 83% reporting that alerts are false positives and not worth their time – Security Magazine
- 60% of SOC practitioners say vendors are selling threat detection tools that create too much noise and too many alerts – Help Net Security
- 84% of organizations report that SOC analysts unknowingly investigate the same incidents several times a month or more – GlobeNewswire
- 71% of SOC practitioners worry they will miss a real attack buried in a flood of alerts – Help Net Security
- SOC analysts are only able to handle 14% of alerts generated by security tools – Palo Alto Networks
- Only 8% of security leaders rate their detection quality as excellent – Splunk’s State of Security 2025
- 57% of security leaders report that they lose valuable time during investigations due to gaps in their data management strategies in the SOC – Splunk’s State of Security 2025
This is where AI comes into the SOC picture, to automate repetitive tasks and free up analysts to focus on higher-value investigations and strategic threat hunting.
AI considerations for SOCs
AI plays a pivotal role in SOCs. However, DIY AI models and commercial AI SOC platforms have their limitations, particularly with the quality of their pre-existing training data. But that’s not all.
Security is a major concern for LLMs and other AI models, as they can inadvertently expose sensitive or proprietary information, remain vulnerable to adversarial attacks, or produce hallucinations without a human analyst fact-checking the output. Here are a few considerations we found with AI in SOC:
- “Regardless of AI maturity, data availability and quality are among the top challenges in AI implementation, as identified by 34% of leaders from low-maturity and 29% from high-maturity organizations.” – Gartner
- “For high-maturity organizations, 48% of leaders identified security threats as one of their top three implementation barriers, while 37% of leaders in low-maturity organizations said finding the right use case was a top barrier.” – Gartner
- LLMs hallucinate between 2.5% and 8.5% of the time – GitHub
- 38% of employees who use AI said they have submitted sensitive work-related information to AI tools without their employer knowing – SC Media
- 55% of Gen AI inputs contain personally identifiable information (PII) – Menlo Security
- Only 42% of security professionals are confident that they fully understand all the types of AI in their organization’s security stack – Darktrace
- 61% of security leaders say that they somewhat trust AI for mission-critical activities – Splunk’s State of Security 2025
- 88% of CISOs report they are concerned about deploying AI securely and managing the risks – Evanta
- 67% of CISOs are unsure if they can govern the use of AI internally – Evanta
Although commercial AI SOC platforms have their distinctive advantages, they struggle to adapt to new use cases and often carry a high total cost of ownership (TCO) that becomes part of the risk equation, transferred to analysts as “noise” and exacerbating alert fatigue.
Factor in LLMs’ preexisting training data, and you introduce another layer of complexity in terms of limited context, outdated threat intelligence, and the potential for inaccurate outputs that require constant human oversight.
What is an adaptive AI SOC?
An adaptive AI SOC platform addresses the critical challenges faced by cybersecurity teams through context-based alert investigation and automated triage.

Radiant Security automatically triages, investigates, and remediates 100% of all alert types from any data source or vendor. Analysts can ingest unlimited data from any log source without additional costs, while remediating threats in minutes with a 1-click response.
The SOC continues to evolve – are you prepared?
The ultimate guide to SOC maturity provides the actionable steps and requirements needed to advance your SOC journey.
Curious how to level up your SOC maturity?





