Security operations teams are overwhelmed. They have too much work, of complexity, and a myriad of tools to manage. Autonomous SecOps platforms and SOARs offer two drastically different, yet similar sounding, automation solutions to alleviate these challenges. Both solutions automate security operations, augment staff, and improve productivity, yet they fundamentally differ in approach, capability, and use cases. This post, we’ll examine these solutions and compare them to determine which is best for your organization.
What is a SOAR?
SOAR stands for security orchestration automation and response, and it is a security software that automates and streamlines portions of security operations workflows by integrating various tools and technologies. It includes incident response, threat intelligence, automation, and other security integrations. SOARs use user-defined playbooks, which are customized logic trees, to enable analysts to quickly respond to security incidents. This reduces their workload and incorporates human decision-making. However, SOAR playbooks require extensive customization and constant tuning to work in specific environments. Additionally, most SOARs are used to gather data, enrich tickets, and automate steps that facilitate a human analyst making the final decision. After that decision is made, the analyst may select to run additional actions and playbooks to further progress response efforts.
A good analogy for SOAR might be a human being aided by the robotic arms and legs of an exoskeleton. The human is running the show and deciding what needs to be done but the exoskeleton (i.e. SOAR) is helping do things more efficiently.

What is an Autonomous SecOps?
An autonomous SecOps platform is software that uses artificial intelligence (AI) and machine learning (ML) to perform security operations without intervention. Autonomous SecOps solutions analyze security data to understand the behavior and context of IT environments, enabling them to make decisions without human analyst intervention. This can help to automate many of the tasks that analysts currently perform, such as triaging and investigating security incidents, as well generating customized incident response action plans and containing and remediating threats. This automation drives down security risk with timely, accurate, thorough results, and complete coverage (e.g. what percentage of the total amount of security alerts received are actually triaged), while also reducing the workload on analysts. While autonomous SecOps solutions may also include SOAR-like automation capabilities, the core of the idea is that they are automating the decision making process and the thinking involved in security operations tasks like triage and investigation.
An analogy for this type of solution would be more like an automated brain or an android. Depending on the vendor, it may or may not also include “robotic arms and legs” (i.e. SOAR-like capabilities).

A Tale of Two Approaches to Automation
SOAR products rely on playbooks designed to replicate the processes of a security operations center (SOC) in response to specific threats such as malware or phishing. These playbooks use if-then logic and decision trees to run security operations processes and can even trigger other playbooks. However, they are usually static and pre-planned, requiring a significant degree of customization to suit an organization’s environment. Creating the playbooks required to effectively automate security operations tasks can often take months or even years to complete. Since the threat and vendor landscape are constantly evolving, the playbooks may need to be repaired and updated frequently – adding further workload for the security team.
Once in use, playbooks can perform tasks such as consolidating alerts from various sources, enhancing ticket data, analyzing threat intelligence data, performing vulnerability scanning and patching, among others. The productivity gains of a functional SOAR can significantly benefit the security operations team. However, several organizations have realized that creating playbooks for automation to support security teams, maintaining operational SOAR playbooks, and providing general support for SOAR requires a considerable amount of effort. In many cases, organizations may need dedicated automation staff or automation teams to accomplish these tasks on a full-time basis. Replacing a team of security analysts with a team of automation engineers greatly reduces the ROI available from automation.
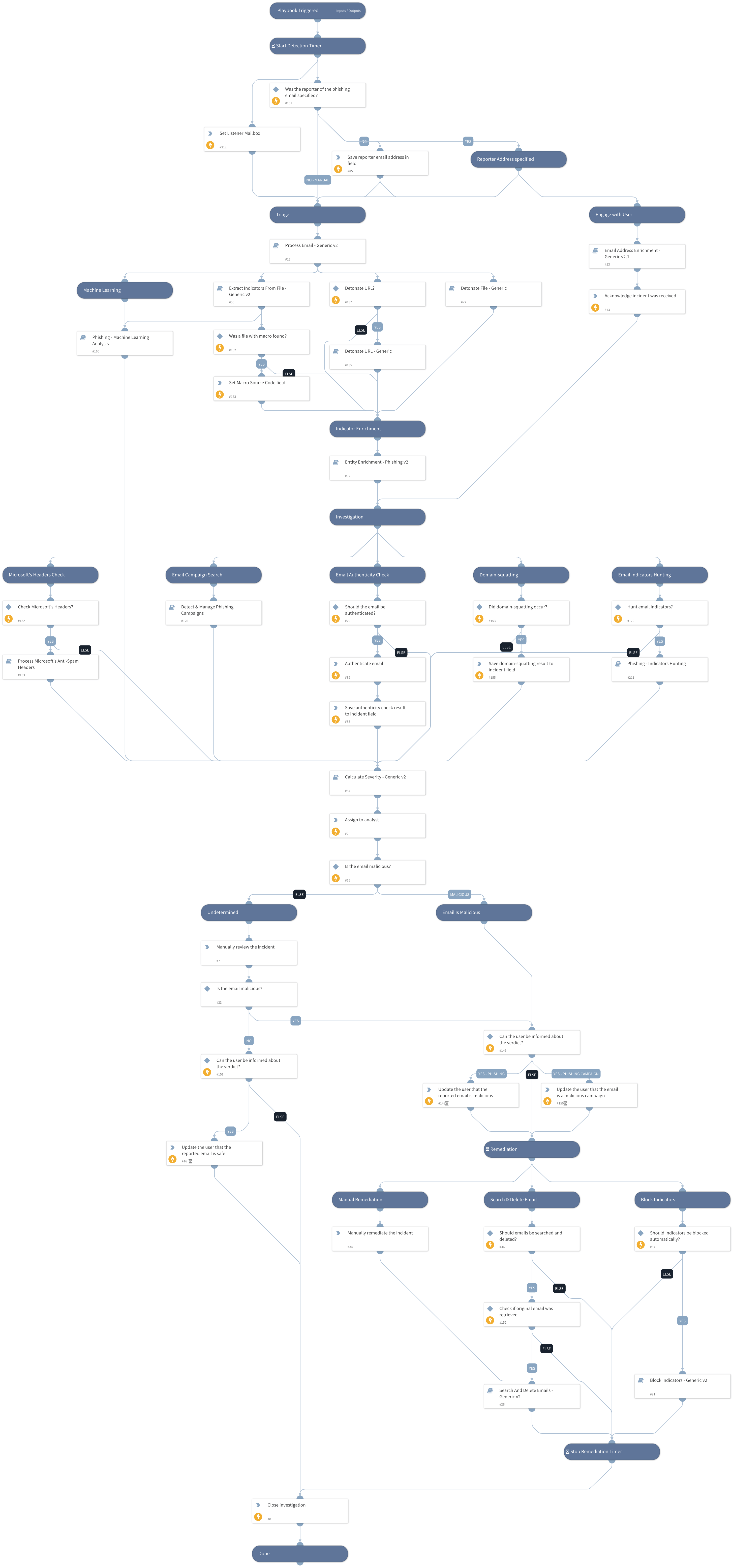
Autonomous SecOps solutions operate differently from SOAR systems in that they perform truly autonomous security operations. Unlike SOAR, which relies on human analysts as the brain, an autonomous SecOps solution seeks to replicate the skills and knowledge of an organization’s best security analyst through deep, continuous learning of its environment, tools, and business. This requires a profound understanding of the problem space and institutional knowledge, which the autonomous SecOps solution acquires by ingesting security data and telemetry from the organization’s IT and security tools. The system then uses this data to continuously learn and establish what is considered normal for the organization. Autonomous SecOps solutions ship with ample pre-trained machine learning models, but also expand their knowledge base by training on data from various industry knowledge-bases such as threat intelligence feeds, MITRE ATT&CK, past incidents and alerts, previously observed threat patterns, closed cases, and more.
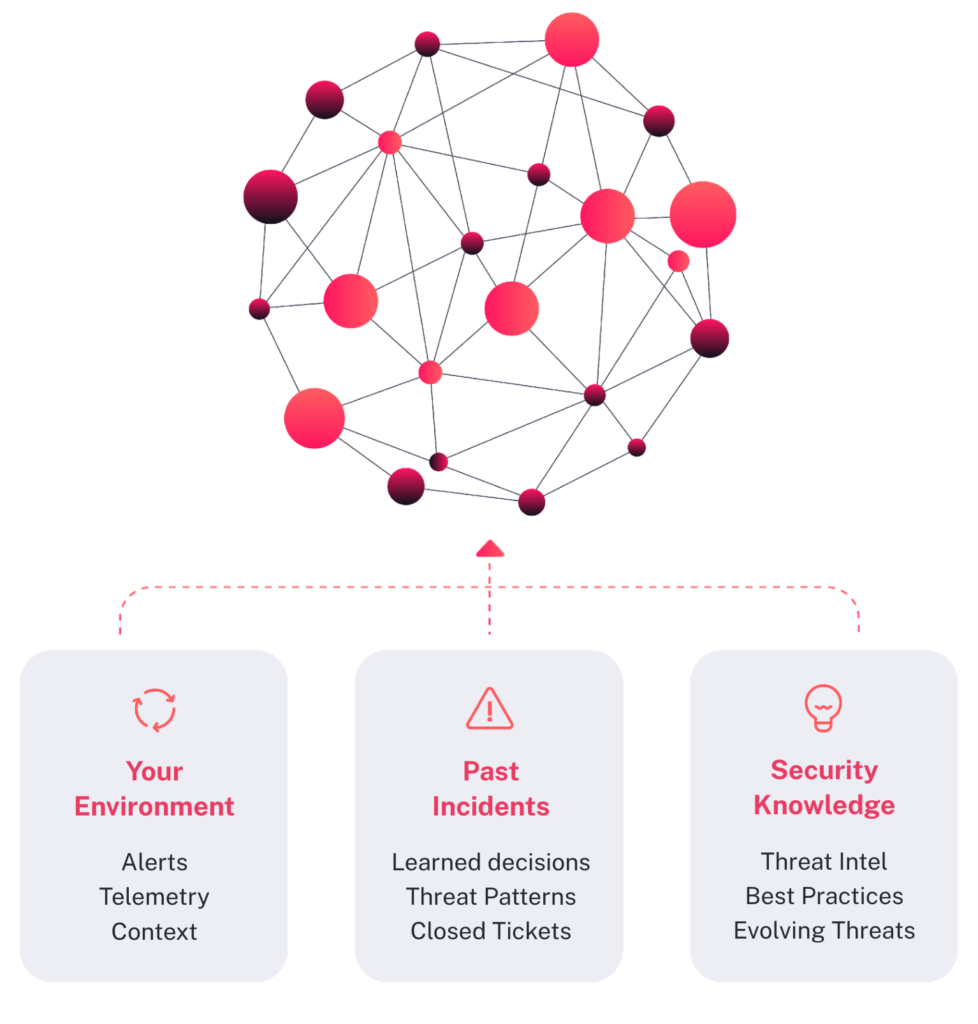
The next step involves using the gathered information for security automation. An autonomous SecOps solution performs a dynamic question and answer process, similar to that of human analysts, for triage and investigation. Rather than performing the same static steps regardless of the threat, the system examines the available information and decides on the best question to ask to advance the investigation. The system then retrieves an answer from either its knowledge store or from external industry-leading intelligence feeds, and then reexamines the new information to select the next most crucial question. This process continues until each alert is determined to be benign or malicious, and all malicious incidents are investigated to determine the full extent of affected entities and establish the root cause. Finally, the system generates a custom response plan that outlines containment and remediation steps, explaining precisely how to use your tools to address the uncovered issue. These steps can be performed manually by an analyst or automated by the system.
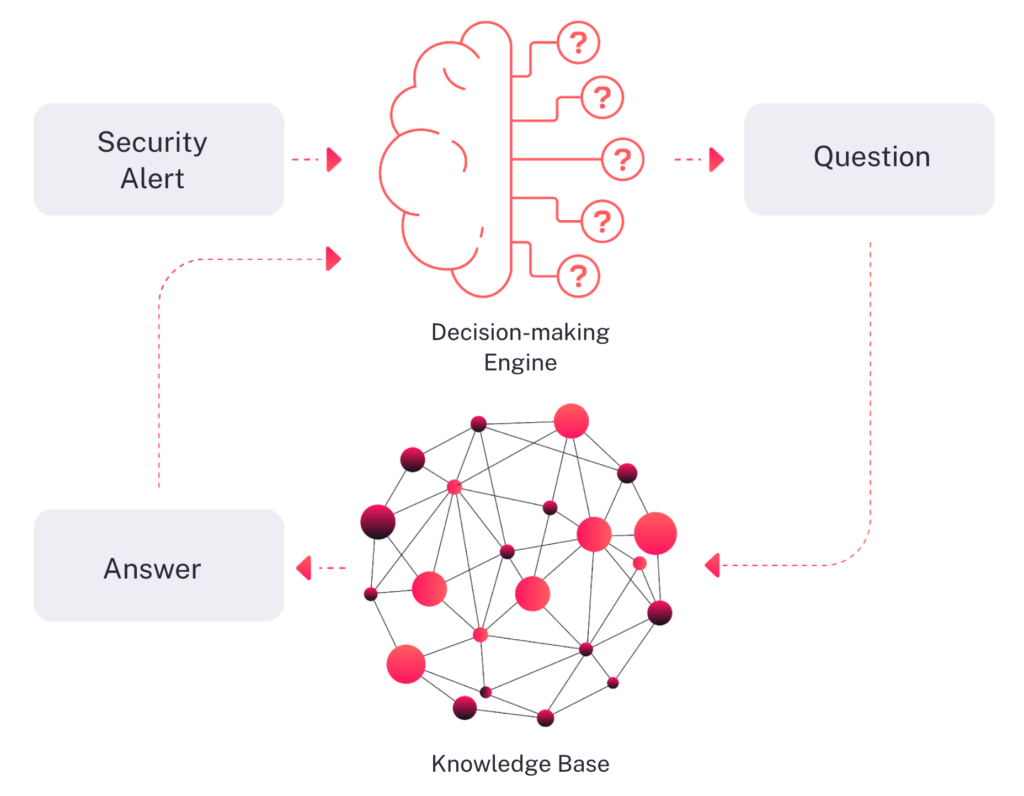
To summarize, even though both types of products share similar language and messaging and can enhance the productivity of security analysts and SOCs, there are distinct differences between the two in terms of where automation occurs, how it’s applied, and which parts of the security operations process can be improved or replaced. Another difference between the products is the type of contextual information that each system uses: autonomous SecOps solutions continuously learn and build a comprehensive knowledge base about the environment, while SOARs retrieve specific contextual information as part of a predefined playbook.
Which tool is best for your organization depends on the specific business and security requirements of your organization.
Want to learn more?
Visit us at radiantsecurity.ai to see a demo or learn how autonomous security operations can transform your SecOps program.