SOC Automation Without the Baggage
Harness the power of AI for automation. Boost the efficiency, effectiveness, and agility of your SOC operations without the hassle and maintenance inherent to prior generations of solutions.
The Next Generation of Security Automation
-
No Static Playbooks
Radiant dynamically selects & performs dozens to hundreds of tests on every alert based on what it knows about your environment and the information available in an alert.
-
No Maintenance Overhead
Radiant eliminates maintenance by automatically managing and updating itself, without your team needing to get involved.
-
No Lengthy Implementation
Implementation is performed in minutes over API integration. Radiant is ready to automate your SOC’s processes day one.
How Radiant Automates Your SOC
Powered by AI, Radiant autonomously performs triage, investigation, and response by analyzing your environment and the information available in security alerts. It dynamically selects and performs relevant tests to ascertain maliciousness of alerts, determine root cause analysis, and assess an incident’s scope. Automated responses are then initiated to address all identified security issues.
Playbook-free Automation
While previous generations of SOC automation tools relied on static, preprogrammed playbooks to replicate existing SOC processes, Radiant sets itself apart by utilizing AI to autonomously inspect security alerts, investigate incidents, and respond to detected issues.
- Turnkey Automation – Radiant‘s does not require customization to inspect security alerts, perform triage, investigation, and remediation autonomously from day one. Radiant is up and running within minutes via API integration, sparing you from the high implementation effort typically associated with automation tools.
- Dynamic Analysis – Radiant’s AI engine inspects all information available about an alert or incident and dynamically selects and performs the tests needed to determine maliciousness, root cause analysis and incident impact. As new information becomes available, Radiant will select and perform additional inspections.
- Tailored Incident Response – Based on what is uncovered during impact analysis, Radiant creates a custom response plan that uses your tooling to respond to each security issue detected. This plan can be executed manually, or performed automatically with one-click remediation actions, or in a fully automated manner.
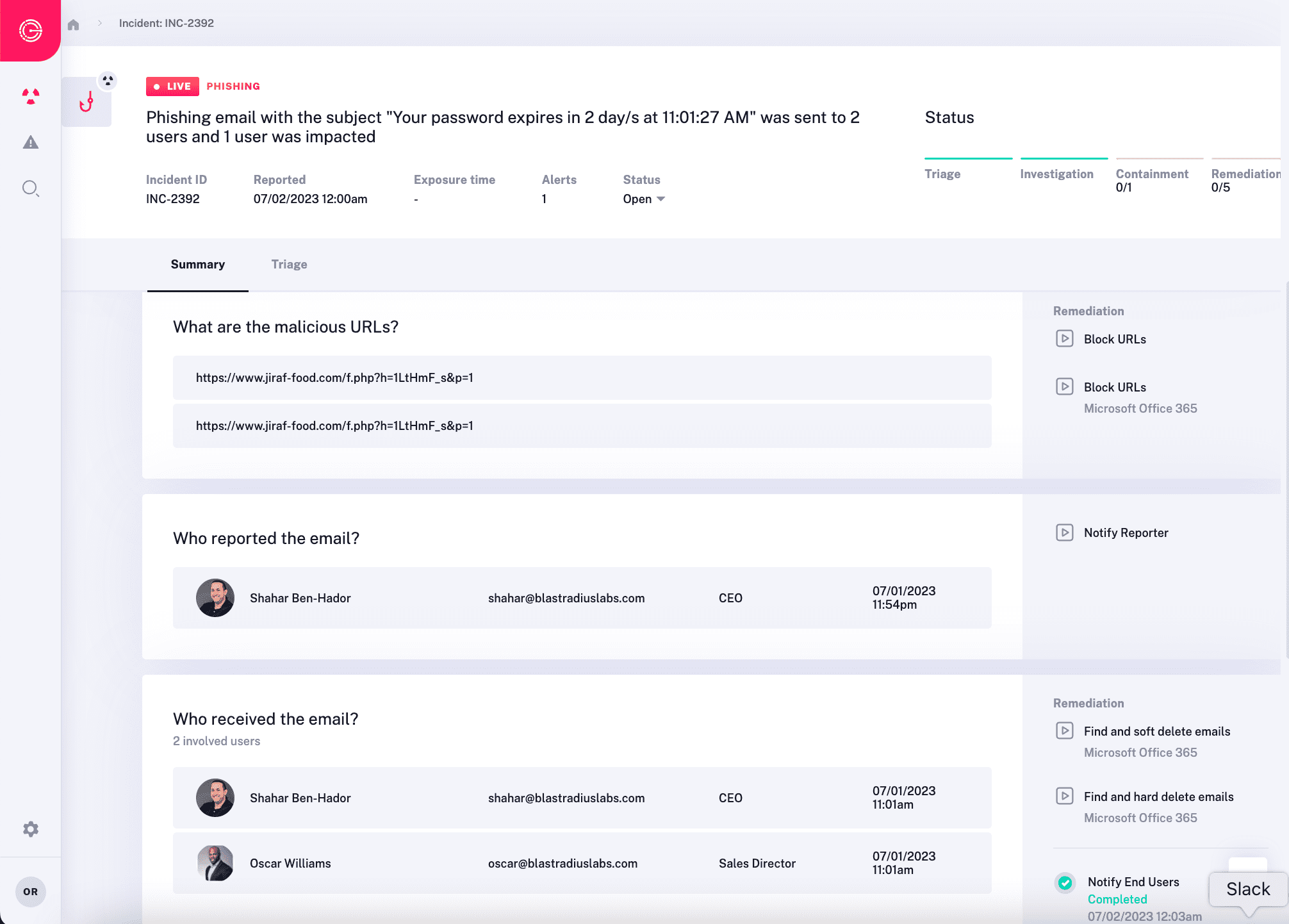
Automate the SOC’s Hardest Work
Performing in depth incident investigation and effective response are the hardest, most human reliant tasks in security operations. As a result, these tasks have still been relegated to humans, despite advances in automation. Not anymore. Radiant enables these complex tasks to be automated, thus freeing human analysts to perform other, higher value work.
- Unlimited Alert Triage – Radiant provides limitless triage capacity using its AI-based engine to automatically select and perform dozens to hundreds of additional tests in order to determine an alert’s maliciousness.
- Automated Impact Analysis – Radiant autonomously determines root cause analysis and uncovers all affected users, devices, and applications, for every incident. This ensures no parts of an attack are missed during response.
- Intelligently Respond – For malicious incidents, Radiant develops and executes a customized response plan that will contain, remediate, and improve resiliency to the specific security issues uncovered by the impact analysis.
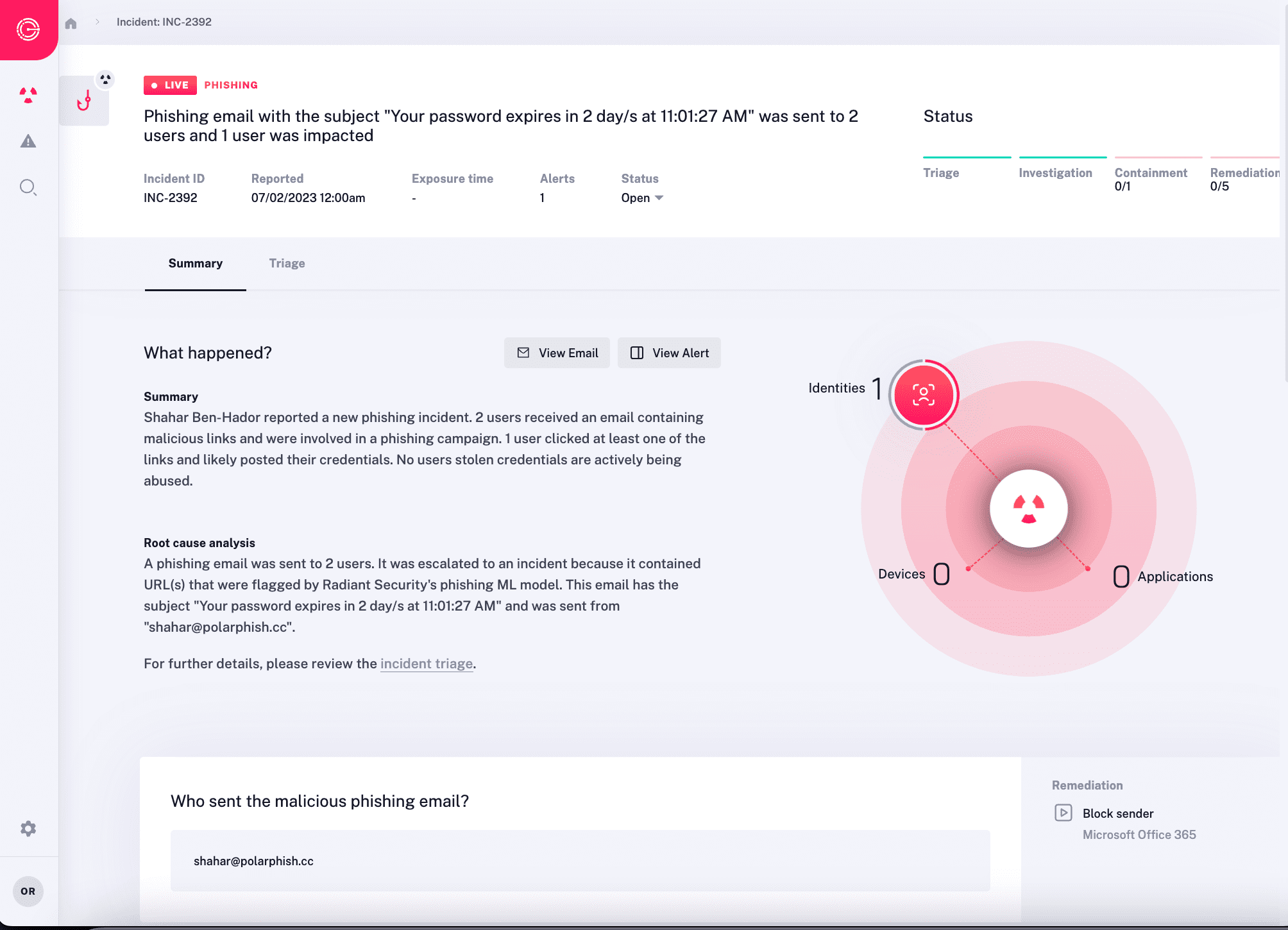
Eliminate Maintenance Overheads
Previous generations of SOC automation require complex setup and significant maintenance effort. Even modern alternatives, while easier to implement, still demand mature processes and substantial time investment from security teams to codify them into playbooks, and to keep them running.
- Effective day one – implementation is achieved in minutes via API integrations, after which Radiant is ready to go. There are no playbooks to set up and maintain.
- Continuous learning – Radiant ingests telemetry data from your organization to rapidly learn normal operating activity. This provides valuable context for evaluating results and reducing false positives. As your organization changes, Radiant automatically learns your new normal.
- Automatic Updating – Radiant is constantly adjusting to changes in the attack landscape, your organizational activity, security best practices, vendor APIs, and more. This approach eliminates maintenance by automatically managing and updating the system without your team needing to get involved.
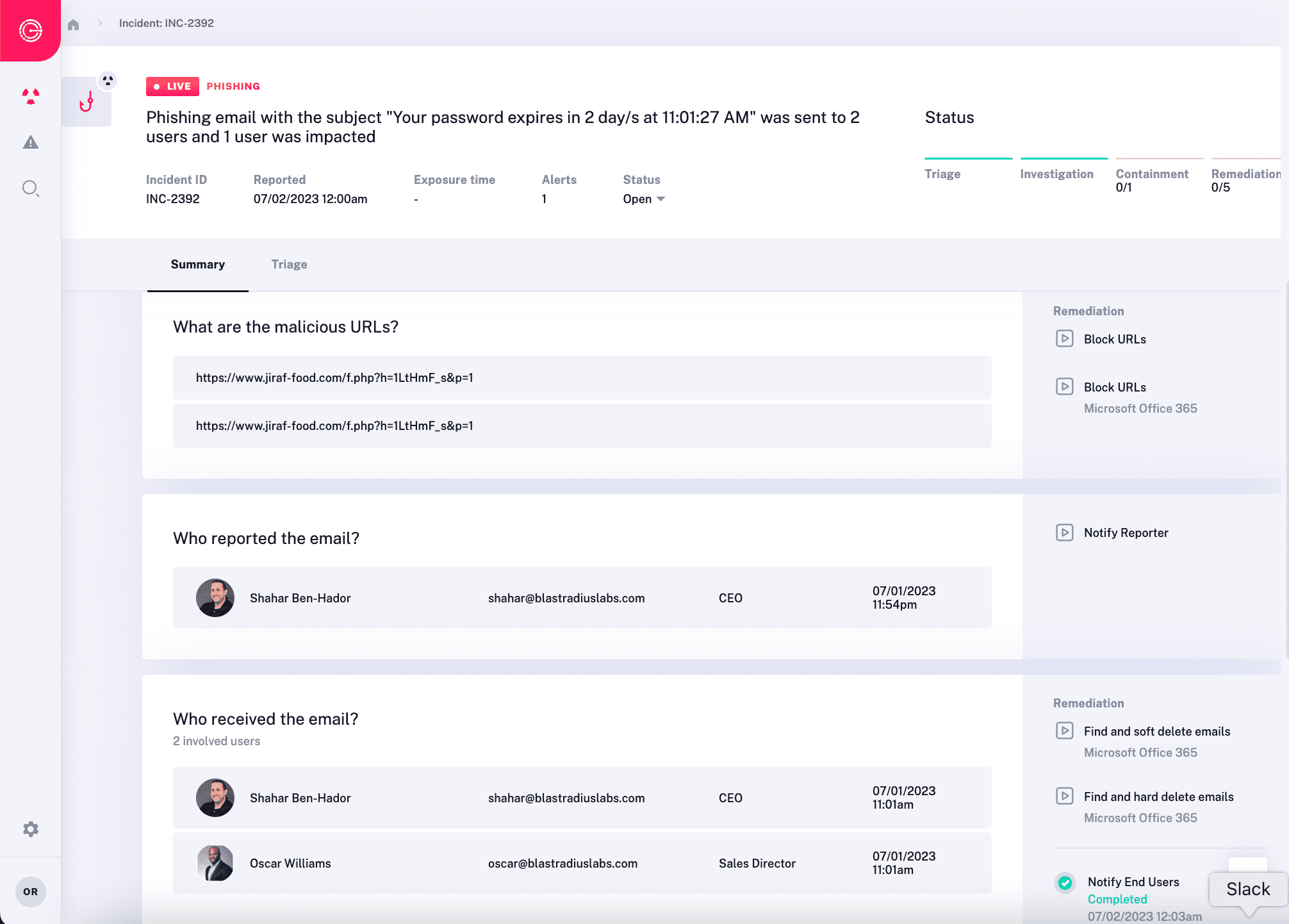
See it in action
Autonomously triage, investigate, contain and respond to every alert in an automated manner using AI and machine learning.
Request a demo