What Are SOAR Tools?
Security orchestration, automation, and response (SOAR) tools are platforms that automate the workflows involved in responding to cybersecurity threats. These tools integrate security operations functions like alert management, case management, threat and vulnerability intelligence, and incident response into a unified system. By centralizing data and workflows, SOAR platforms help security teams coordinate and automate the response to incidents across diverse tools and environments, reducing the manual labor required for incident management.
SOAR solutions act as the connective tissue in a security operations center (SOC), bridging the gap between technologies such as SIEMs, ticketing systems, and endpoint detection tools. They facilitate collaboration, provide a single interface for managing incidents, and help enforce consistent response procedures. Modern SOAR platforms support integration with third-party services and often allow teams to define custom workflows tailored to their specific operational needs.
Benefits of SOAR Tools
As cyber threats grow in volume and complexity, SOAR tools offer a scalable way to manage incident response with greater efficiency and consistency. By reducing manual work and improving coordination between systems, these platforms bring several operational and strategic advantages.
- Faster incident response: Automates repetitive tasks and predefined workflows, reducing the time it takes to detect, investigate, and respond to threats.
- Improved consistency: Enforces standard operating procedures across incidents, ensuring uniform response regardless of who is handling the case.
- Reduced alert fatigue: Filters and enriches alerts using threat intelligence and contextual data, helping analysts focus only on relevant, high-priority events.
- Better collaboration: Centralizes communication and incident data, enabling team members to work from the same platform and track progress in real-time.
- Integration: Connects with SIEMs, firewalls, endpoint tools, and ticketing systems, allowing security teams to operate across tools without context switching.
- Scalability: Handles increased workloads without needing a proportional increase in human resources, making it suitable for growing environments.
- Improved reporting and metrics: Provides dashboards and analytics for tracking performance, identifying bottlenecks, and measuring response effectiveness over time.
Key Functions of SOAR Tools
Orchestration
Orchestration allows SOAR platforms to coordinate data flows and actions across security products that normally operate independently. The SOAR layer connects systems such as SIEMs, firewalls, EDR platforms, ticketing tools, and identity services, pulling information from each and triggering actions without requiring analysts to move between consoles. This consolidates operational tasks, standardizes how tools interact, and creates a unified environment where incidents can be investigated and handled with fewer manual steps.
Key capabilities:
- Integrating data and controls from SIEM, EDR, firewalls, identity services, and ticketing platforms
- Normalizing event data from multiple sources into a shared workflow
- Triggering actions across connected tools from a single interface
- Managing rules, workflows, and tool connections in one place
- Coordinating multi-step processes that span different products and environments
Automation
Automation in SOAR platforms reduces the volume of manual work by executing repeatable tasks using predefined logic. Common steps such as enrichment, correlation, evidence collection, and basic containment can be performed automatically, which helps analysts focus on decisions that require human judgment. SOAR systems use playbooks to represent conditional logic, branching paths, and automated actions, allowing routine activities to run with minimal intervention while still supporting manual overrides when needed.
Key capabilities:
- Running playbooks that automate enrichment, analysis, containment, and notification steps
- Applying decision logic to route incidents based on event context
- Collecting logs, indicators, and metadata from connected tools
- Executing standardized responses to recurring alert types
- Reducing human error in repetitive workflows through consistent automation
Response
Response functions give SOAR platforms the ability to act directly on incidents, from containment through recovery. Tools can isolate hosts, disable accounts, block network flows, or push configuration updates based on analyst actions or automated rules. Response features also include case tracking, documentation, and auditability, helping teams record and manage every stage of an incident. Combined with orchestration and automation, these capabilities support structured, consistent handling of threats from initial detection to closure.
Key capabilities:
- Containing threats by isolating endpoints, blocking IPs, or disabling user accounts
- Executing remediation steps such as malware removal or policy updates
- Managing cases, evidence, timelines, and documentation
- Supporting manual, semi-automated, or fully automated response execution
- Enabling collaboration through task assignment, notes, and real-time status updates
10 Notable SOAR Tools
1. Radiant Security
Radiant Security is an Agentic AI SOC platform that automates alert triage, investigation, and response across the security lifecycle. The platform is designed to reduce false positives by roughly 90%, enabling analysts to spend more time on verified threats rather than manual triage. Radiant also aims to shorten investigation and response times (MTTR) and lower operational costs, while helping teams avoid the fatigue that often comes with high alert volume.
Key features include:
- Agentic AI triage and investigation for all alert types, including previously unseen or low-fidelity ones.
- Transparent reasoning that shows how and why the AI reached its conclusions, helping analysts validate decisions and build trust.
- Integrated response with one-click, executable action plans that can be carried out manually or automated when appropriate.
- Log management with unlimited retention, delivered at a cost significantly lower than traditional SIEM platforms.
- AI feedback loop that allows teams to influence and adjust triage behavior using environmental context, improving accuracy over time.
Radiant provides a unified environment for handling alerts, investigations, response actions, and log data, with an emphasis on efficiency, clarity, and analyst control.
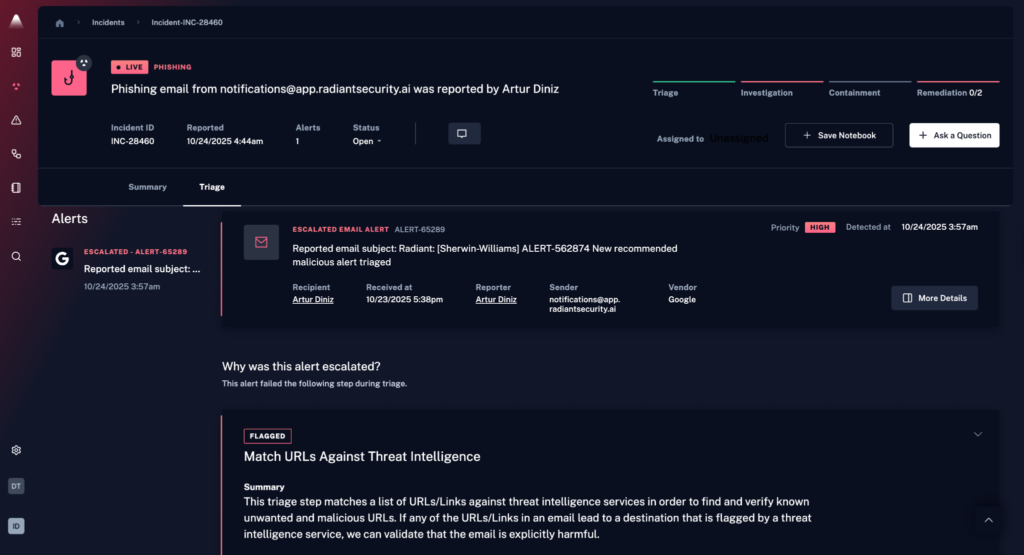
Source: Radiant Security
2. Cortex XSOAR
Cortex XSOAR is a SOAR platform that centralizes and automates incident response workflows across a security operations center (SOC). It reduces alert noise and repetitive tasks, enabling security teams to focus on high-priority incidents. XSOAR provides a unified environment where analysts can access incident data, threat intelligence, and investigation tools.
Key features include:
- Automates repetitive tasks to reduce alert fatigue and analyst workload
- Centralized interface with integrated incident data, threat intel, and ticketing
- Provides a war room for collaborative investigation and incident management
- Over 900 prebuilt integrations and thousands of automated actions
- Visual playbook editor for building and customizing workflows
Source: Palo Alto Networks
3. Splunk SOAR
Splunk SOAR is a security automation and orchestration platform that simplifies operations across the security stack. It integrates with over 300 third-party tools and supports more than 2,800 automated actions, enabling security teams to automate workflows without replacing existing infrastructure.
Key features include:
- Over 2,800 automated actions and 300 integrations for orchestrating across your existing tools
- Visual playbook editor for building and customizing workflows, no coding required
- Prebuilt playbooks aligned with MITRE ATT&CK and D3FEND frameworks
- Integrated case management with task tracking, segmentation, and documentation
- Native integration with Splunk Enterprise Security for a unified SecOps platform
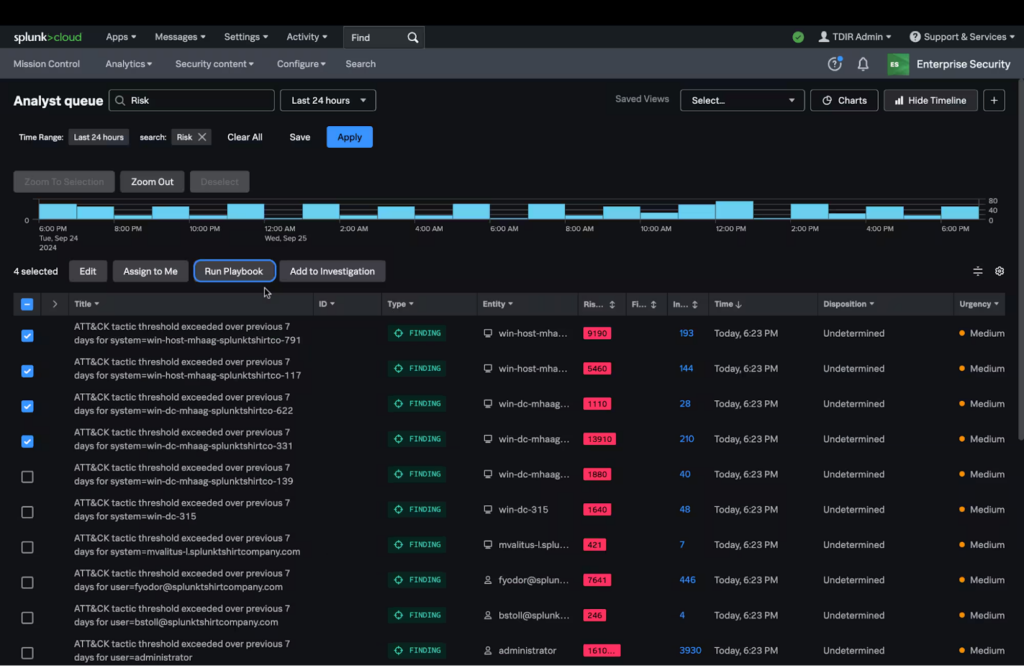
Source: Splunk
4. IBM Security QRadar SOAR
IBM QRadar SOAR is a security orchestration, automation, and response platform to help security teams manage and respond to incidents faster. It centralizes incident response through playbooks, automation, and customizable workflows that adapt as investigations evolve.
Key features include:
- Offers playbooks that adapt to incident conditions as investigations progress
- Visual playbook designer with in-app guidance for simplified automation setup
- Automated enrichment, correlation, and case prioritization to reduce response time
- Customizable case management to match existing workflows and processes
- Breach response module supports compliance with over 200 global privacy regulations
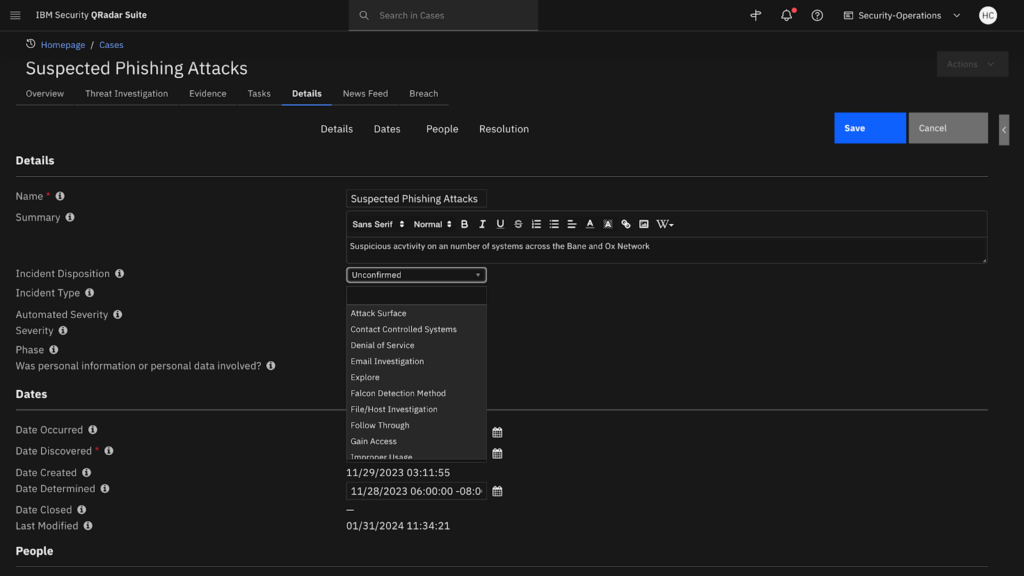
Source: IBM
5. Microsoft Sentinel
Microsoft Sentinel is a cloud-native SIEM and SOAR solution that enables automated threat detection and response across hybrid environments. Its SOAR capabilities are built on Azure Logic Apps, allowing users to create, deploy, and manage automated workflows, called playbooks, that respond to security events.
Key features include:
- Prebuilt playbook templates for automating common threat response tasks
- Built on Azure Logic Apps for low-code playbook development and management
- 100s of managed connectors for integrating with Microsoft and third-party services
- Support for custom connectors to handle non-standard integrations
- Centralized automation blade in the Sentinel portal for managing SOAR assets
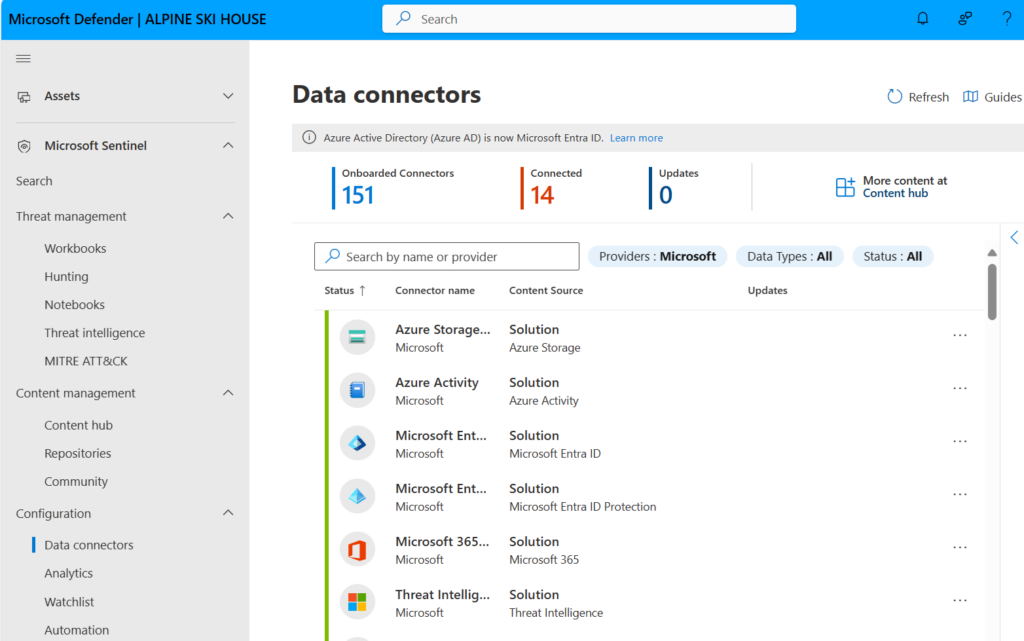
Source: Microsoft
6. Devo SOAR
Devo SOAR is a cloud-native security orchestration, automation, and response solution built to eliminate manual, repetitive security workflows and help SOC teams respond to threats at scale. It uses AI playbooks and decision automation to reduce alert volume and triage time, converting noisy alerts into more manageable number cases.
Key features include:
- AI-powered playbooks that automate investigation, triage, and response
- ThreatLink engine that reduces thousands of alerts into tens of high-quality cases
- Visual, no-code playbook builder guided by expert SOPs via Audra AI
- Integration with more than 300 security tools
- Unified case management with real-time collaboration and automated task tracking
Source: Devo
7. Swimlane
Swimlane is a security automation platform that extends beyond traditional SOAR by delivering scalable, AI-enabled automation for SOC workflows, vulnerability management, and compliance. Built on the Turbine platform, it supports the execution of up to 25 million automated actions per day while offering customization.
Key features include:
- AI automation that adapts to evolving security workflows and use cases
- Executes up to 25 million automation actions daily
- Customizable case management with over 70 configurable fields
- Swimlane Marketplace offering over 1,800 playbooks, 3,600 actions, and 490 connectors
- Plug-and-play automation solutions focused on outcomes, not vendor limitations
Source: Swimlane
8. FortiSOAR
FortiSOAR is a security orchestration, automation, and response platform to centralize and simplify security operations across IT, OT, and enterprise environments. Built for both enterprise and MSSP deployments, FortiSOAR enables teams to standardize workflows, eliminate manual processes, and accelerate incident response through playbooks and AI-based decision support.
Key features include:
- Over 800 prebuilt playbooks and 500 integrations for rapid automation at scale
- FortiAI and machine learning-based recommendation engine for guided investigation and response
- Threat intelligence from FortiGuard Labs and public sources to enrich alerts and actions
- Visual no/low-code playbook builder for easy customization of automated workflows
- Flexible deployment options: SaaS, on-prem, public cloud, or MSSP-hosted
Source: Fortinet
9. Exabeam
Exabeam SOAR, delivered through Automation Management within the New-Scale Platform, enables security teams to centralize, simplify, and automate their threat detection, investigation, and response (TDIR) workflows. It supports thousands of integrations through its Open API Standard (OAS) compatibility.
Key features include:
- Embedded directly in the Exabeam Threat Center for a seamless analyst experience
- Open API Standard (OAS) support enables thousands of third-party integrations
- Prebuilt, modular playbooks with multi-path logic to reduce duplication and effort
- Low-code/no-code automation builder with full version control and deployment tools
- Centralized rule and trigger management for all automation workflows
Source: Exabeam
10. Tines
Tines is a security automation platform intended to overcome the limitations of traditional SOAR tools. It enables teams to automate critical workflows without writing or managing code. Its no-code interface allows analysts and engineers to create automation across various environments.
Key features include:
- No-code automation for building complex workflows quickly and without technical barriers
- Universal API connectivity enables integration across internal and external systems
- Intended for scalable security operations without legacy overhead
- Simplified case management to investigate, remediate, and report from one workspace
- Designed to reduce duplicate alerts, accelerate response, and boost team efficiency
Source: Tines
Key Considerations for Choosing SOAR Tools
Selecting the right SOAR platform depends on your organization’s security maturity, team structure, existing tooling, and compliance needs. Beyond checking for basic features like playbooks and integrations, you should assess how well a platform aligns with your operational goals and existing environment.
Key considerations include:
- Integration breadth and depth: Evaluate whether the SOAR tool integrates deeply with your existing stack, including SIEM, EDR, threat intel feeds, ticketing, and cloud platforms. Broad API coverage and bi-directional integrations are critical for orchestration.
- Customization and workflow flexibility: Look for platforms that allow creation of custom workflows, playbooks, and automation logic without extensive coding. Support for dynamic branching and conditional logic helps tailor response to incident context.
- Case management capabilities: Robust case management should provide incident timelines, task tracking, audit logs, and collaboration features needed for incident handling and compliance.
- Automation at scale: Assess whether the platform can process high alert volumes and automation actions without performance issues. Review execution limits, concurrency, and historical uptime in large deployments.
- Security and access controls: Ensure the presence of fine-grained RBAC, secure credential handling, and logging of automated actions. Integration with identity systems such as LDAP and SSO is also relevant.
- Ease of use and operator experience: Analysts should be able to manage playbooks with minimal training. Visual editors, wizards, and clear error handling reduce operational friction.
- Support for compliance and reporting: Tools should streamline compliance needs through reporting, audit trails, and breach response modules aligned with regulatory requirements.
- Deployment model and vendor lock-in: Evaluate cloud, on-prem, or hybrid deployment requirements and how tightly the tool is tied to a vendor ecosystem. Consider migration and integration flexibility.
- Community and ecosystem: Active communities, integration marketplaces, and frequent updates signal a mature ecosystem that can reduce development time and improve long-term viability.
- Scalability and future readiness: The platform should scale with SOC growth in team size, infrastructure complexity, and threat landscape, supporting expansion of tools, use cases, and automation goals.
Conclusion
SOAR platforms consolidate alert intake, case handling, data enrichment, and response execution into a coordinated system that reduces manual steps and removes fragmentation across security tools. By integrating SIEM, EDR, identity, ticketing, and threat intelligence sources, they create a consistent workflow for investigating and resolving incidents.
With orchestration, automation, and response capabilities in one environment, SOAR tools give security teams a structured way to manage high alert volumes, standardize procedures, and scale operations as environments grow more complex.

