Who Are Arctic Wolf’s Competitors? Quick Comparison
Arctic Wolf is a cybersecurity company specializing in managed detection and response (MDR), security operations, and risk management services. The platform delivers a cloud-native solution that helps organizations prevent, detect, and respond to cyber threats.
Arctic Wolf’s main competitors in the cybersecurity market include automated SOC platforms like Radiant, and MDR services from providers like CrowdStrike, Rapid7, and SentinelOne.
The following table summarizes the key features of Arctic Wolf compared to its competitors. We review each of the competitors in more detail later in this article.
| Solution Type | Name | Key Features |
| SOC Automation Platform | Radiant Security | AI-driven SOC automation, autonomous alert triage, threat investigation, and remediation; integrates with SIEM and XDR tools; learns from analyst feedback |
| SOC Automation Platform | DropZone AI | Autonomous investigations, adaptive to org context, orchestrates responses, integrates with 60+ tools, and provides transparent reporting |
| SOC Automation Platform | Prophet Security | Agentic AI platform, dynamic investigation plans, autonomous triage, adapts to feedback, integrates with workflows |
| MDR | Arctic Wolf | Cloud-native MDR, concierge security team, 24/7 monitoring, tailored guidance, and vulnerability management |
| MDR | Rapid7 MDR | 24/7 SOC, threat hunting, integrated SIEM/XDR visibility, active containment, and dedicated advisor |
| MDR | CrowdStrike Falcon Complete | AI-driven detection, 24/7 SOC, cross-domain protection, full-cycle remediation, and threat hunting |
| MDR | Qualys VMDR | Real-time threat intel, unified visibility, automated patching, risk-based CVE prioritization, compliance checks |
| MDR | Sophos MDR | AI-native SOC, 24/7 coverage, full-scale incident response, 350+ integrations, and proactive hunting |
| MDR | SentinelOne Vigilance MDR | Machine-speed triage, 24/7 expert analysts, Storyline alert enrichment, and MTTR under 30 mins |
| MDR | Bitdefender MDR | Full alert lifecycle, dark web monitoring, pre-approved responses, 24/7 SOC, root cause analysis |
| MDR | Heimdal MXDR | Unified platform, AI/ML threat detection, 24/7 global SOC, automated response, full-spectrum protection |
Key Arctic Wolf Limitations
While Arctic Wolf offers an extensive managed security platform with valuable hands-on support, users have pointed out several limitations that may impact the overall experience. These limitations were reported by users on the G2 platform:
-
- Alert fatigue and noise: Arctic Wolf can generate a high volume of alerts, which may overwhelm teams and make it difficult to prioritize real threats. While tuning is available and support can help suppress benign alerts, the initial noise level can still be a challenge.
-
- Dashboard navigation and usability: The portal interface can be confusing, especially for new users. Key information is sometimes hard to locate, and the risk dashboard has limited sorting options, which can slow down workflows.
-
- Manual deployment for macOS: Installing the Arctic Wolf agent on Mac devices requires manual intervention, adding overhead for organizations with large macOS deployments. Windows deployment is smoother due to integration with Intune.
-
- Limited reporting customization: Built-in reporting features are restrictive, especially for vulnerability assessments. Users often need to request help from Arctic Wolf analysts to generate custom reports that meet specific needs.
-
- Onboarding and learning curve: Fully understanding the dashboards and interpreting data takes time. The onboarding process includes guidance, but it still requires patience as users learn to navigate the platform and adjust to the volume of information.
-
- Ticketing system usability: The built-in ticketing system is functional but not intuitive. Navigating it can be cumbersome, which may slow down response times or task tracking.
-
- Delayed security maturity: Achieving a meaningful improvement in security posture is a gradual process. Users should not expect immediate results, as progress depends on sustained effort across different layers of their infrastructure.
-
- Concierge follow-up gaps: While the Concierge Security teams provide helpful reminders, some users feel the follow-up on unresolved tasks could be more assertive to drive timely completion.
Should You Choose an MDR Service or SOC Automation Platform? Key Considerations
Choosing between an MDR service and a SOC automation platform depends on your organization’s size, internal capabilities, and desired level of control.
MDR services are suitable for organizations that lack in-house security expertise or want a fully managed solution. These services provide 24/7 monitoring, human-led threat response, and hands-on support, making them suitable for companies that need external help to manage security operations. However, they may offer limited customization and slower iteration cycles due to reliance on external teams.
SOC automation platforms are intended for teams that want to scale their existing SOC operations without significantly growing headcount. These platforms use AI to automate alert triage, investigation, and even response, reducing the burden on analysts and accelerating time to action. Unlike MDRs, they give teams more control and transparency, and they integrate with existing tools and workflows. This makes them attractive to mature organizations seeking efficiency, speed, and a higher degree of operational ownership.
Notable Arctic Wolf Competitors and Alternatives
Let’s go into more detail on Arctic Wolf’s primary competitors.
SOC Automation Platforms
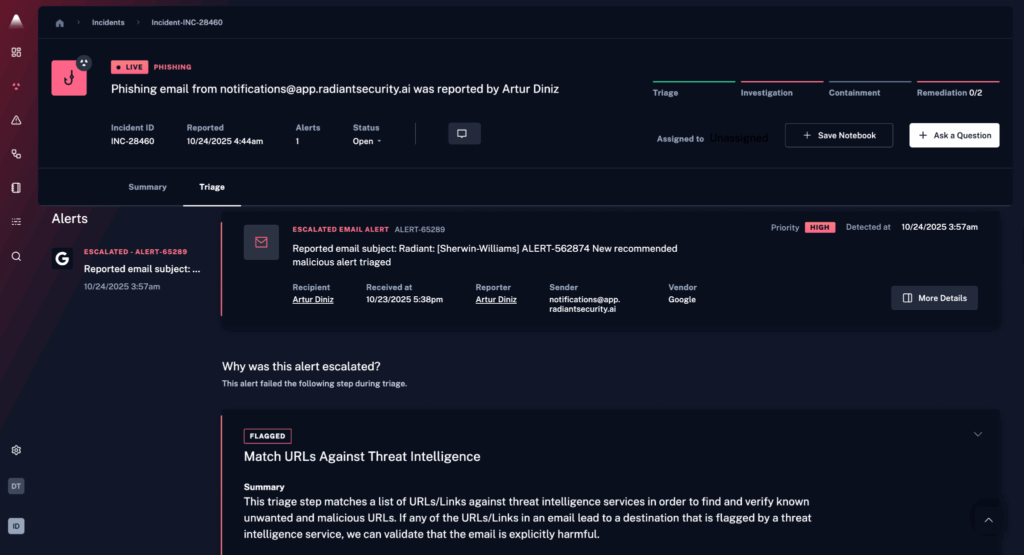
1. Radiant Security
Radiant Security is an Agentic AI SOC platform that automates alert triage, investigation, and response across the security lifecycle. The platform is designed to reduce false positives by roughly 90%, enabling analysts to spend more time on verified threats rather than manual triage. Radiant also aims to shorten investigation and response times (MTTR) and lower operational costs, while helping teams avoid the fatigue that often comes with high alert volume.
Key capabilities include:
-
- Agentic AI triage and investigation for all alert types, including previously unseen or low-fidelity ones.
-
- Transparent reasoning that shows how and why the AI reached its conclusions, helping analysts validate decisions and build trust.
-
- Integrated response with one-click, executable action plans that can be carried out manually or automated when appropriate.
-
- Log management with unlimited retention, delivered at a cost significantly lower than traditional SIEM platforms.
-
- AI feedback loop that allows teams to influence and adjust triage behavior using environmental context, improving accuracy over time.
Radiant provides a unified environment for handling alerts, investigations, response actions, and log data, with an emphasis on efficiency, clarity, and analyst control.
2. DropZone AI
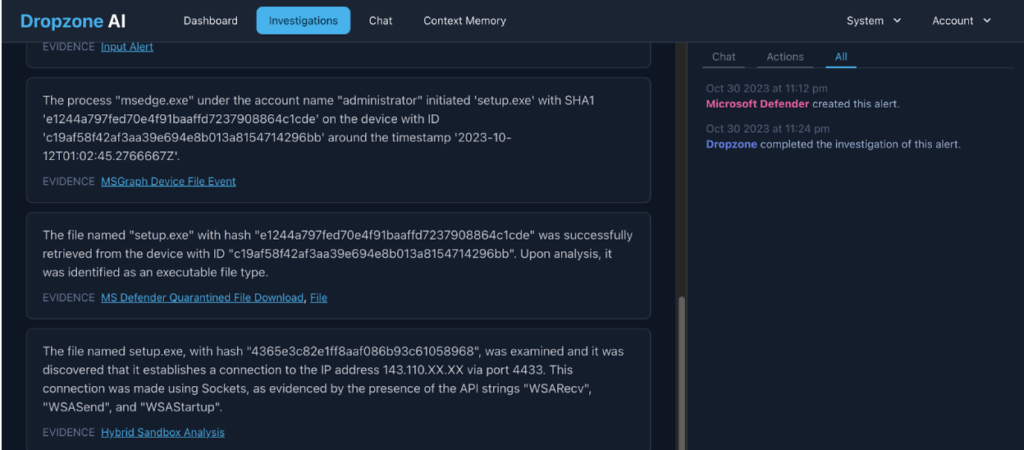
DropZone AI is an autonomous AI SOC analyst that investigates alerts using multiple tools and environment context. It adapts to organizational policies and workflows, integrates with existing security systems, and concludes investigations with documented actions such as dismissal, escalation, or containment.
Key features include:
-
- Autonomous investigations: Replicates expert analyst techniques to investigate alerts, gathering evidence across tools and data sources, and, when necessary, interviewing affected users to clarify intent.
-
- Adaptive behavior: Learns the environment through continuous investigations and feedback, understanding policies, risk tolerance, and workflows, and allowing teams to guide actions to match SOC procedures.
-
- Response orchestration: Decides appropriate next steps after investigations, including dismissing false positives, notifying teams, escalating credible threats, or containing incidents, with decisions informed by investigation context.
-
- Integrations and context: Integrates with SIEM, EDR, firewall, cloud, email, and identity tools via 60 integrations, and automatically builds a context knowledge base to support investigations and chats.
-
- Reporting and trust: Generates reports with severity conclusions, executive summaries, and key insights, supported by single-tenant architecture, SOC 2 Type 2 certification, and transparent investigation evidence.
3. Prophet Security
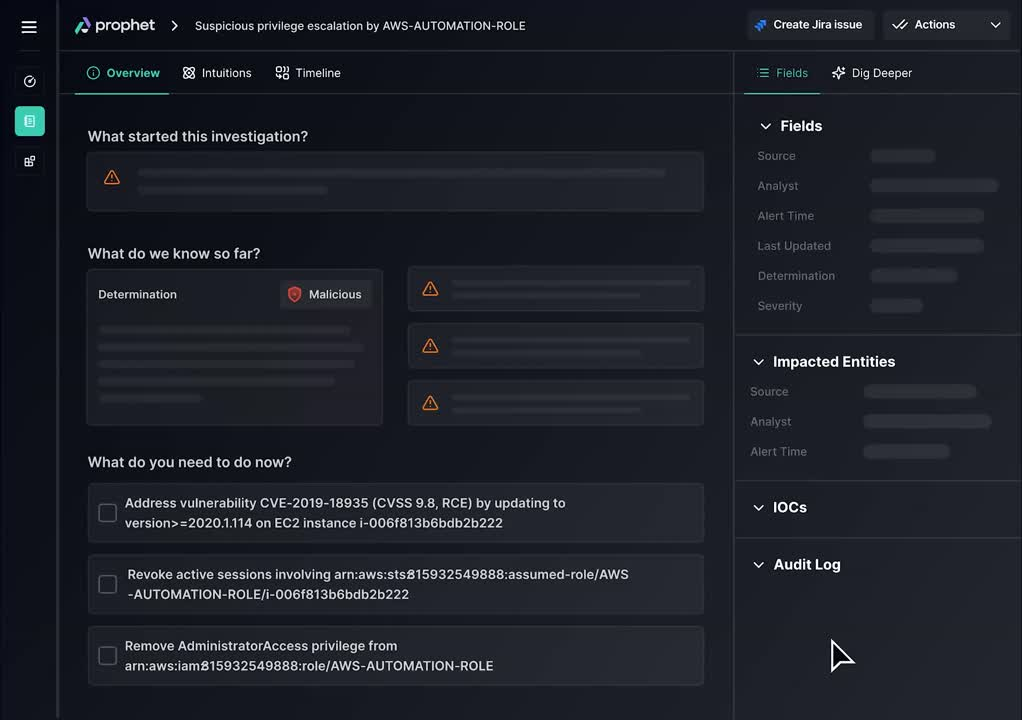
Prophet Security is an agentic AI SOC platform for triaging, investigating, and responding to alerts. It summarizes alerts, builds investigation plans, gathers and correlates evidence across sources, determines severity and remediation steps, and adapts based on analyst feedback with visibility into investigation evidence.
Key features include:
-
- Planning and summarization: Instantly summarizes incoming alerts and produces a dynamic investigation plan that guides subsequent evidence collection and analysis across relevant sources.
-
- Autonomous investigation: Emulates expert analysts to autonomously retrieve, correlate, and analyze data from integrated systems, reducing manual steps required to reach a defensible conclusion.
-
- Response and workflow integration: Determines severity and priority, proposes remediation steps, and integrates with existing security and collaboration workflows to drive consistent response actions.
-
- Learning and adaptation: Learns from analyst feedback and continuously adapts to the environment, refining plans and decisions to reflect organizational context and preferences.
-
- Transparency and data protection: Provides visibility into investigation plans and underlying evidence, is SOC 2 Type 2 compliant, and states customer data is not used to train models.
MDR Services
4. Rapid7 MDR
Rapid7 MDR is a fully managed detection and response solution that delivers continuous threat monitoring, incident response, and threat hunting across a customer’s environment. The platform combines Rapid7’s SIEM and XDR technologies with a global SOC that manages alert triage, investigation, and containment.
Key features include:
-
- 24×7 SOC coverage: Around-the-clock global monitoring, analysis, and response to security threats
-
- Dedicated cybersecurity advisor: Ongoing guidance and tuning aligned to the unique needs of the organization
-
- Integrated SIEM and XDR visibility: Full access to alert data and SOC activity for transparency and investigation
-
- Active threat containment: SOC analysts can immediately respond and contain active threats in real time
-
- Proactive threat hunting: Hypothesis-driven hunts for undetected threats using emerging attacker behaviors
5. CrowdStrike Falcon Complete
CrowdStrike Falcon Complete is a fully managed detection and response (MDR) service that combines expert operations with AI-driven capabilities to detect, investigate, and eliminate threats across the enterprise. Delivered through the Falcon platform, this MDR solution focuses on measurable outcomes, reducing mean-time-to-respond, stopping cross-domain attacks, and remediating threats without requiring internal team intervention.
Key features include:
-
- 24/7 expert-led operations: Around-the-clock monitoring, investigation, and remediation by a dedicated team of security professionals
-
- AI-powered detection and response: Uses Charlotte AI to accelerate detection and simplify decision-making with agentic workflows
-
- Full-cycle remediation: The Falcon Complete team takes direct action to isolate, contain, and remove threats across the environment
-
- Cross-domain protection: Detects and stops attacks across endpoints, identities, cloud workloads, and third-party integrations using next-gen SIEM
-
- Proactive threat hunting: Intelligence-led hunting via Falcon Adversary OverWatch delivers continuous, AI-enhanced threat detection
6. Qualys VMDR
Qualys VMDR (Vulnerability Management, Detection, and Response) is an integrated platform that helps organizations identify, prioritize, and remediate vulnerabilities across their entire attack surface. Unlike traditional scanning tools, VMDR leverages TruRisk™ scoring and real-time threat intelligence from multiple sources to quantify business risk and reduce exposure.
Key features include:
-
- Real-time threat intelligence: Uses TruRisk™ to prioritize vulnerabilities based on exploitability, impact, and business context
-
- Unified asset visibility: Continuously discovers known and unknown assets across on-prem, cloud, containers, and mobile
-
- Automated patch and mitigation: Speeds up remediation by up to 60% using native patching tools or automated ticket generation
-
- Risk-based prioritization: Focuses on actively exploited and ransomware-related CVEs using MITRE ATT&CK® alignment
-
- Integrated compliance checks: Includes configuration assessments, PCI 4.0 compliance, and CIS benchmark evaluations
7. Sophos MDR
Sophos Managed Detection and Response (MDR) is a security service that blends AI-driven threat detection with hands-on expertise from a global team of cybersecurity professionals. Designed to meet organizations wherever they are in their security maturity, Sophos MDR consolidates data across existing tools, correlates threat signals, and provides full-scale incident response without caps or surprise fees.
Key features include:
-
- 24/7 expert monitoring and response: Around-the-clock coverage by global cybersecurity professionals
-
- AI-native SOC platform: Aggregates and analyzes threat data from multiple tools using AI to reduce noise and surface real threats
-
- Proactive threat hunting: Identifies and eliminates stealthy adversaries before they escalate into incidents
-
- Full-scale incident response: Comprehensive containment and remediation with no additional fees or limitations
-
- Extensive technology integrations: Supports over 350 security products to extend protection across the existing tech stack
8. SentinelOne Vigilance MDR
SentinelOne Vigilance MDR is a managed detection and response service built to extend and accelerate security operations by combining machine-speed technology with 24/7 expert analysis. Operating on a global follow-the-sun model, Vigilance enables organizations to offload alert triage, threat investigation, and response to a team of in-house analysts who act as an extension of their security team.
Key features include:
-
- 24/7/365 global threat monitoring: Around-the-clock coverage across time zones with follow-the-sun analyst operations
-
- Fast response times: Achieves 30-minute mean time to respond (MTTR), among the fastest in the industry
-
- SOC team augmentation: Frees internal teams to focus on strategic priorities while Vigilance handles daily threat operations
-
- Storyline™ alert enrichment: Reduces alert fatigue by adding context and correlation to raw telemetry
-
- Human-centric analysis: Analysts tailor triage and prioritization based on the unique needs of each environment
9. Bitdefender MDR
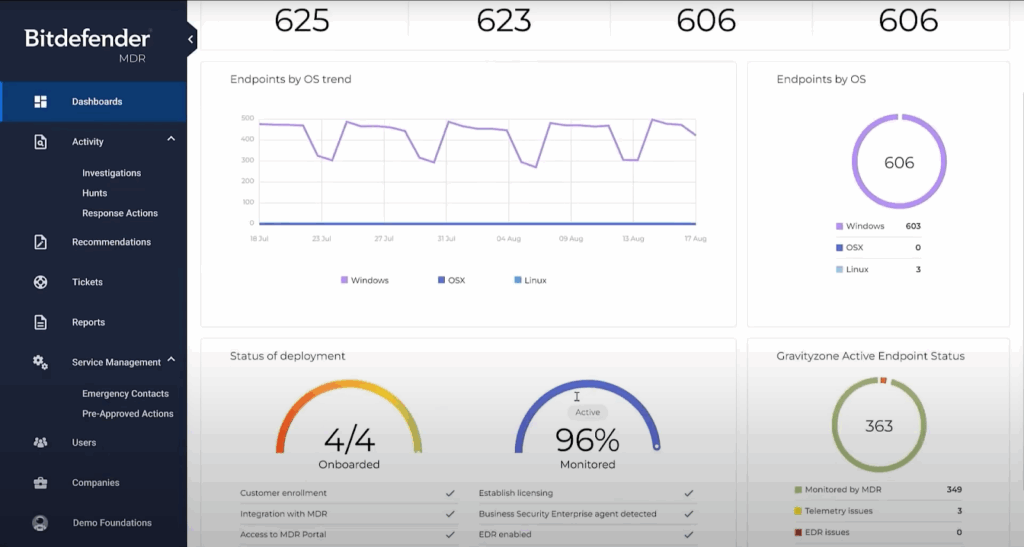
Bitdefender Managed Detection and Response (MDR) is a managed security service that combines global SOC coverage, threat expertise, and a security platform. Designed to relieve overburdened internal teams, Bitdefender MDR handles the full alert lifecycle, from detection through triage, response, and root cause analysis.
Key features include:
-
- 24/7 global SOC coverage: Round-the-clock protection from a team of over 285 in-house analysts and threat hunters
-
- Full alert lifecycle management: Analysts filter and respond to threats, reducing noise and ensuring only critical alerts reach the customer
-
- Pre-approved response actions (PAAs): Rapid threat containment and mitigation based on predefined rules to minimize response time
-
- Root cause and impact analysis: Deep investigation of incidents with detailed after-action reporting and 72-hour enhanced monitoring
-
- Dark web threat hunting: Proactive monitoring for leaked credentials, IP, and brand mentions across dark web and threat actor sources
10. Heimdal MXDR
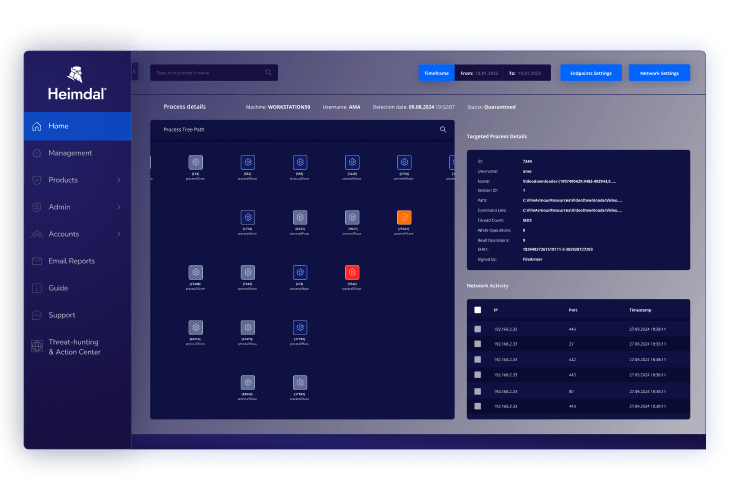
Heimdal Managed Extended Detection and Response (MXDR) is a fully managed security service to deliver threat detection, incident response, and full-spectrum protection without adding headcount or infrastructure. Delivered through Heimdal’s Unified Security Platform, this solution provides centralized visibility and real-time threat mitigation across endpoints, networks, cloud, and identity layers.
Key features include:
-
- 24/7 global SOC coverage: Around-the-clock monitoring, threat hunting, and incident response by dedicated Heimdal experts
-
- Unified security platform: Integration of detection and response tools across all layers of the IT environment
-
- Threat detection: AI/ML-driven analytics enable faster and more accurate identification of complex threats
-
- Automated response capabilities: Rapid, policy-driven containment actions reduce dwell time and manual intervention
-
- Incident handling: Full investigation, forensic analysis, and active mitigation for advanced attacks
Conclusion
Both SOC automation platforms and MDR solutions aim to strengthen security operations, but they serve different operational models. MDRs deliver expert-led, turnkey security with minimal internal effort, making them ideal for resource-constrained teams. SOC automation platforms empower internal teams with AI-driven speed and scalability, helping reduce manual workload and improve response times.

