The Radiant Security Platform
Sets up in minutes and works day one to boost analyst productivity, detect real incidents, and enable rapid response.
How it Works
Radiant’s AI-powered SOC co-pilot streamlines and automates tedious tasks in the SOC to boost analyst productivity, uncover real attacks through investigation, and enable analysts to respond more rapidly.
Turbocharge SOC Workflows With The Help of AI
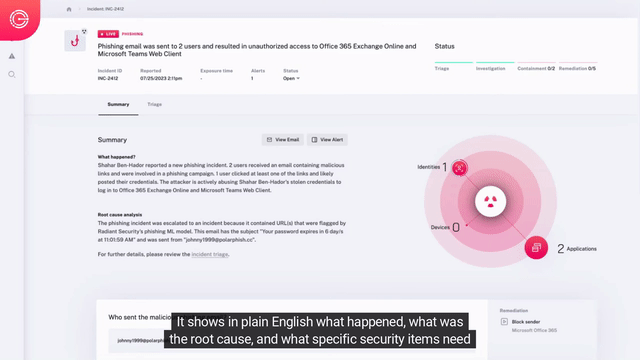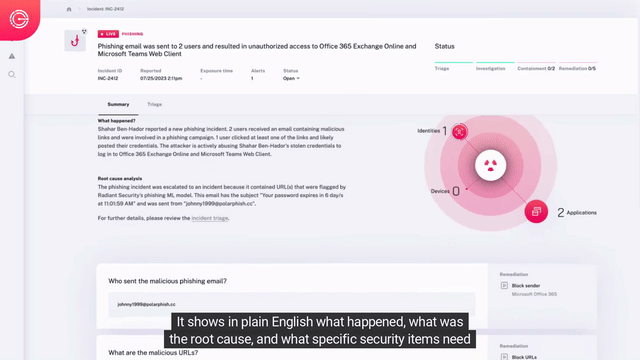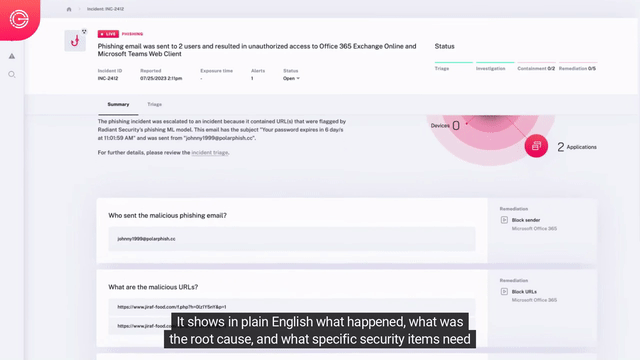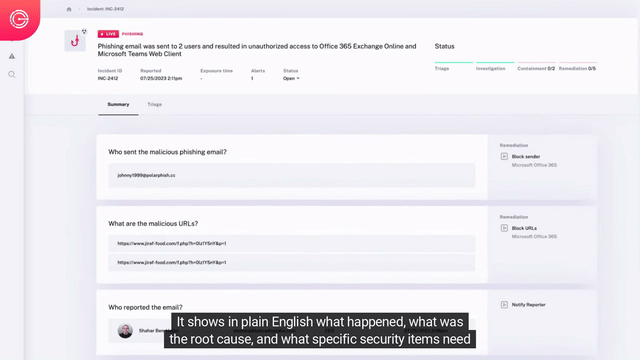
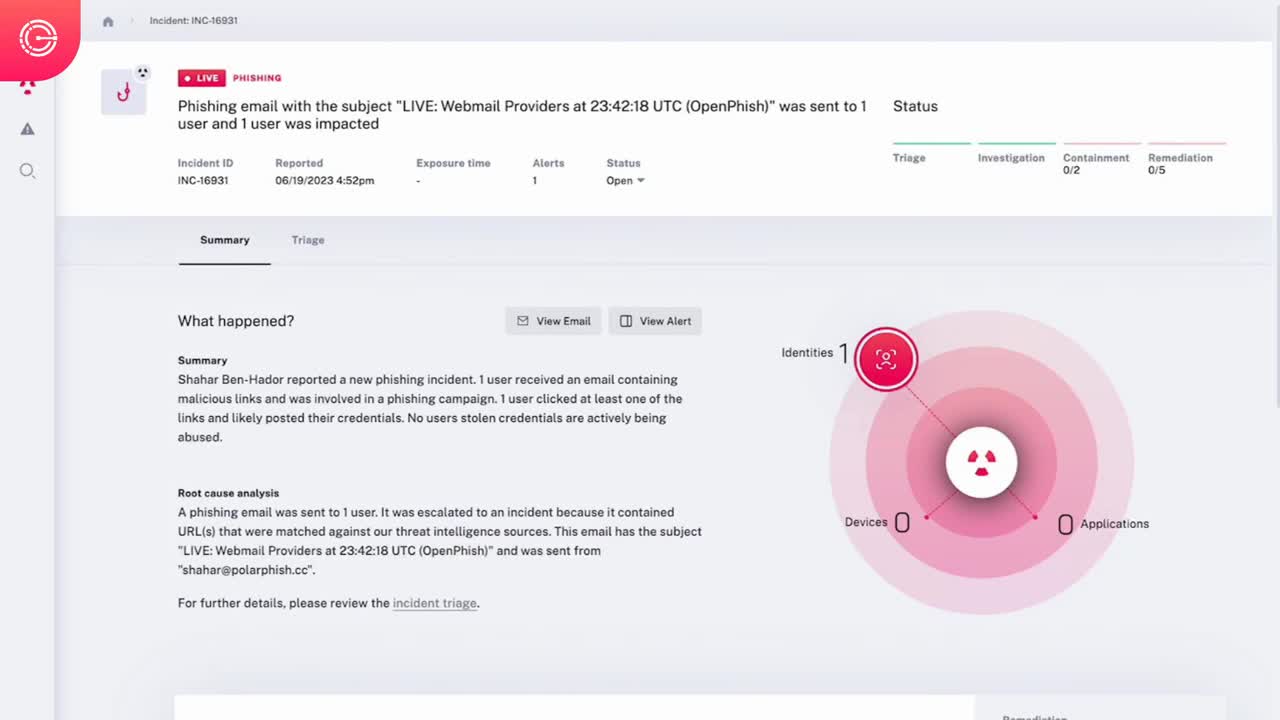
Automated Detection, Triage, & Investigation
- Automated Triage – Automatically inspect all elements of suspicious alerts using AI, then dynamically selects & performs dozens to hundreds of tests to determine if an alert is malicious.
- Impact Analysis – Analyze all malicious alerts to understand detected issues’ root cause and complete incident scope with all affected users, machines, applications, and more.
- Data Stitching – Stitch together data sources like email, endpoint, network, and identity to follow attacks wherever they go, so nothing gets missed.
Rapid Containment & Remediation
- Incident specific response – Radiant dynamically builds a response plan for analysts based on the specific containment and remediation needs of the security issues uncovered during incident impact analysis.
- Automated response – Analysts can automate or manually perform the corrective actions to correct each security issue for rapid, effective response.
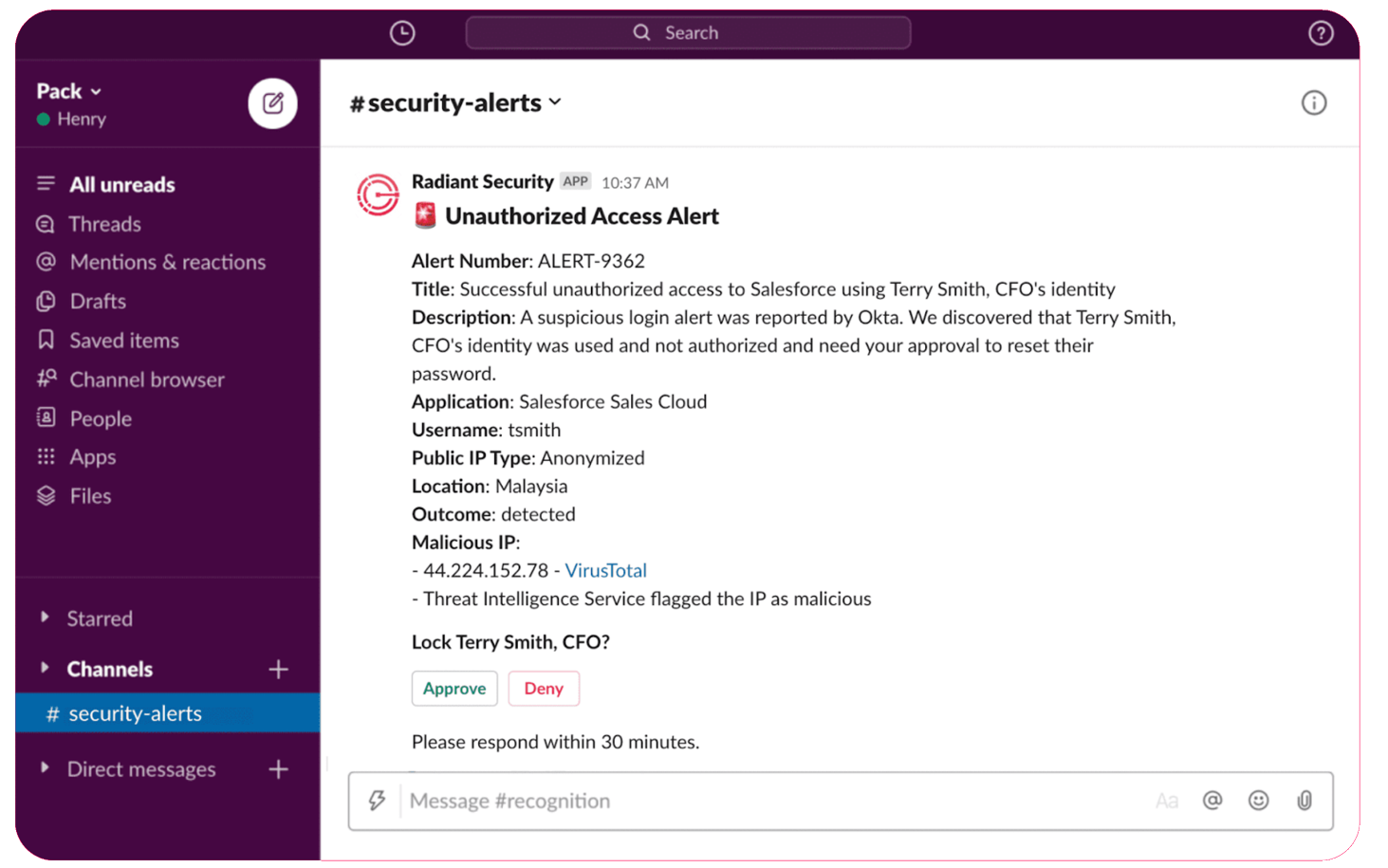
Escalations & Approvals
Taking corrective actions to address an incident often involves tasks which require approval, such as disabling an account or isolating a device from the corporate network. Radiant can automate your existing escalation chains and approval processes to efficiently obtain permission to perform corrective actions.
Communication Workflows
Automatically keep affected users, and stakeholders informed by leveraging your existing productivity tools (e.g., Slack, Teams, Email, etc.) for seamless communication. This ensures rapid response and uninterrupted workflows, to keep your team moving and your response times low.

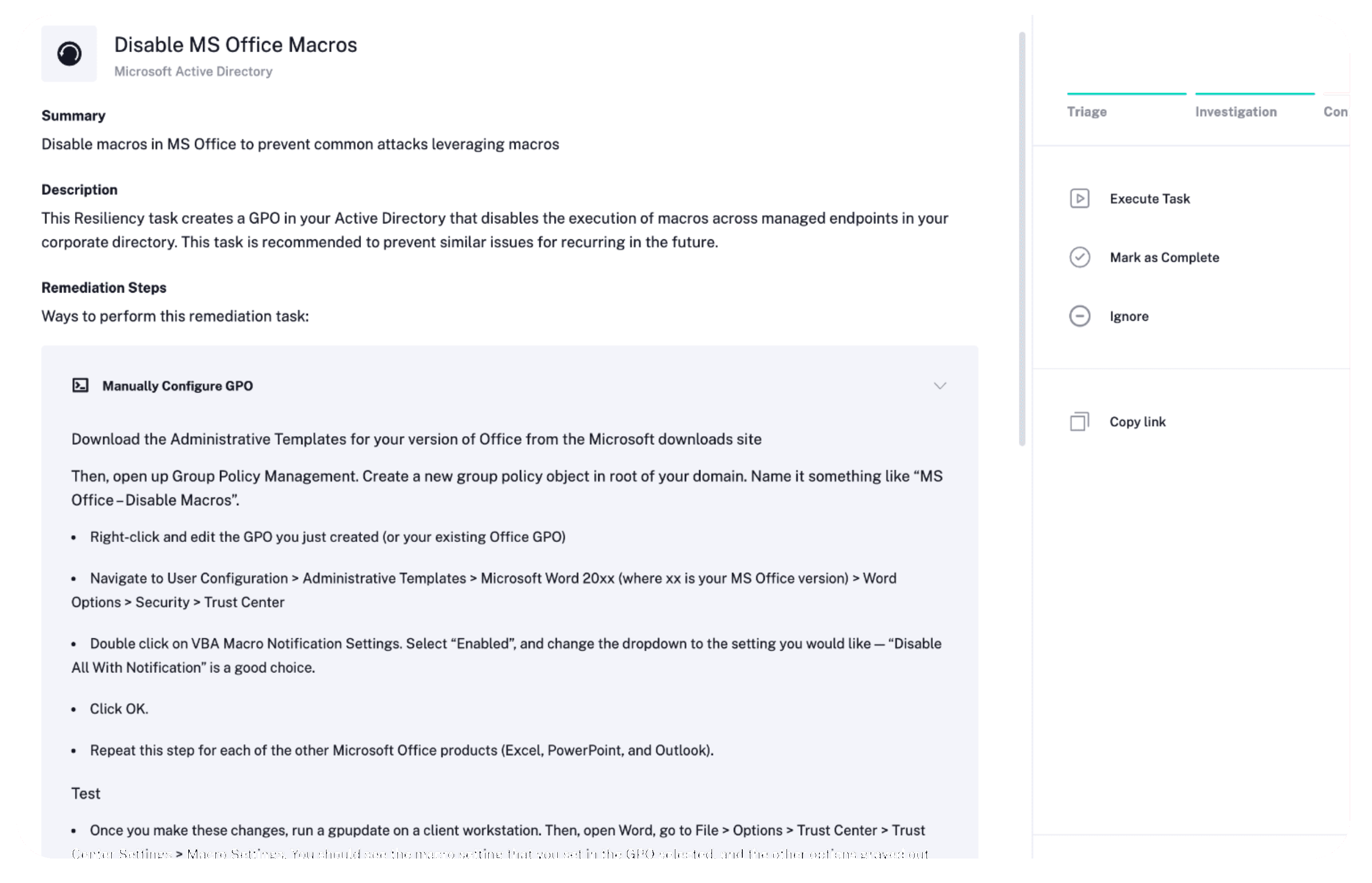
Resiliency Improvement
After an incident has been handled, it’s important to improve your security posture. As part of each incident’s custom response plan, Radiant automatically recommends actions that can be taken to enhance your environment’s resiliency against similar threats, reducing the likelihood of future incidents of the same nature.
What You Get
-
Quick time-to-value
Deployment takes minutes and then the system immediately begins yielding results similar to a seasoned analyst familiar with your environment.
-
Deep Security Expertise
Our system automatically adapts to evolving threats so that incidents are always handled with current best practices.
-
Reduced Workloads
Automating triage and investigation reduces analysts workloads by as much as 95%.
-
Peace of Mind
Every single alert is triaged until it’s found to be malicious or benign. Nothing is filtered out or slips through the cracks.
-
Higher Quality Results
Every incident is triaged and investigated consistently, in a data driven way, equal to the work of your best analyst.
-
Lower Costs
Taking an autonomous approach to security operations is typically less than 50% of the cost of an MDR.
Radiant Security vs. Common Security Operations Approaches
MDR
In-house SOC
Capacity
Unlimited
(Based on Software)
Varies
(Based on contract)
Varies
(Based on analyst capacity)
Quality
High
(Based on data)
Mixed
(based on vendor & analyst)
Mixed
(Depends on analyst)
Completeness
High
Triage & investigate every alert
Low
Filters results alerts to find riskiest, creates blindspots.
Best effort
Consistency
High
Low
Every analyst is different
Low
Every analyst is different
Scope
Full incident lifecycle
Triage only
Full incident lifecycle
Institutional Knowledge
High
Based on continuous learning of environment
Low
High
Depends on analyst
Price
