AI-Based SOAR Alternative
Automate triage, incident analysis and response using AI—without the hassle, playbooks, and maintenance overhead that has plagued previous generations of security automation tools.
SOAR Failed to Deliver the Results That Security Teams Need
-
Humans Are Still Required
The premise of security automation is to free analysts from tedious tasks but SOAR still requires analysts to be involved in every alert.
-
Poor ROI due to Overhead
The productivity gains afforded by SOAR are usually eclipsed by the effort needed to deploy and maintain them leading to low ROI.
-
A Partial Scope of Work
SOAR tools often help with enrichment or simple response actions but leave the heaviest work, incident investigation and analysis, to analysts.
Moving Beyond Playbooks with AI
While SOAR tools rely on static, preprogrammed playbooks to replicate existing SOC processes, Radiant sets itself apart by utilizing AI to autonomously inspect security alerts and incidents.
- Dynamic Triage – Based on information included in the security alert or uncovered during triage, Radiant’s AI automatically selects and performs dozens to hundreds of additional tests in order to determine an alert’s maliciousness.
- Automated Impact Analysis – A timely and accurate understanding of what transpired in an incident is crucial to proper response. Radiant autonomously determines root cause analysis and uncovers all affected users, devices, and applications, for every incident.
- Robust Error Handling – Part of the reason playbooks fail is that unexpected responses pop up all the time. Something as simple as a captcha can break an entire automation flow. Radiant’s AI engine gracefully navigates past these challenges, solving captchas and adjusting the type of interrogations it performs based on what it encounters.
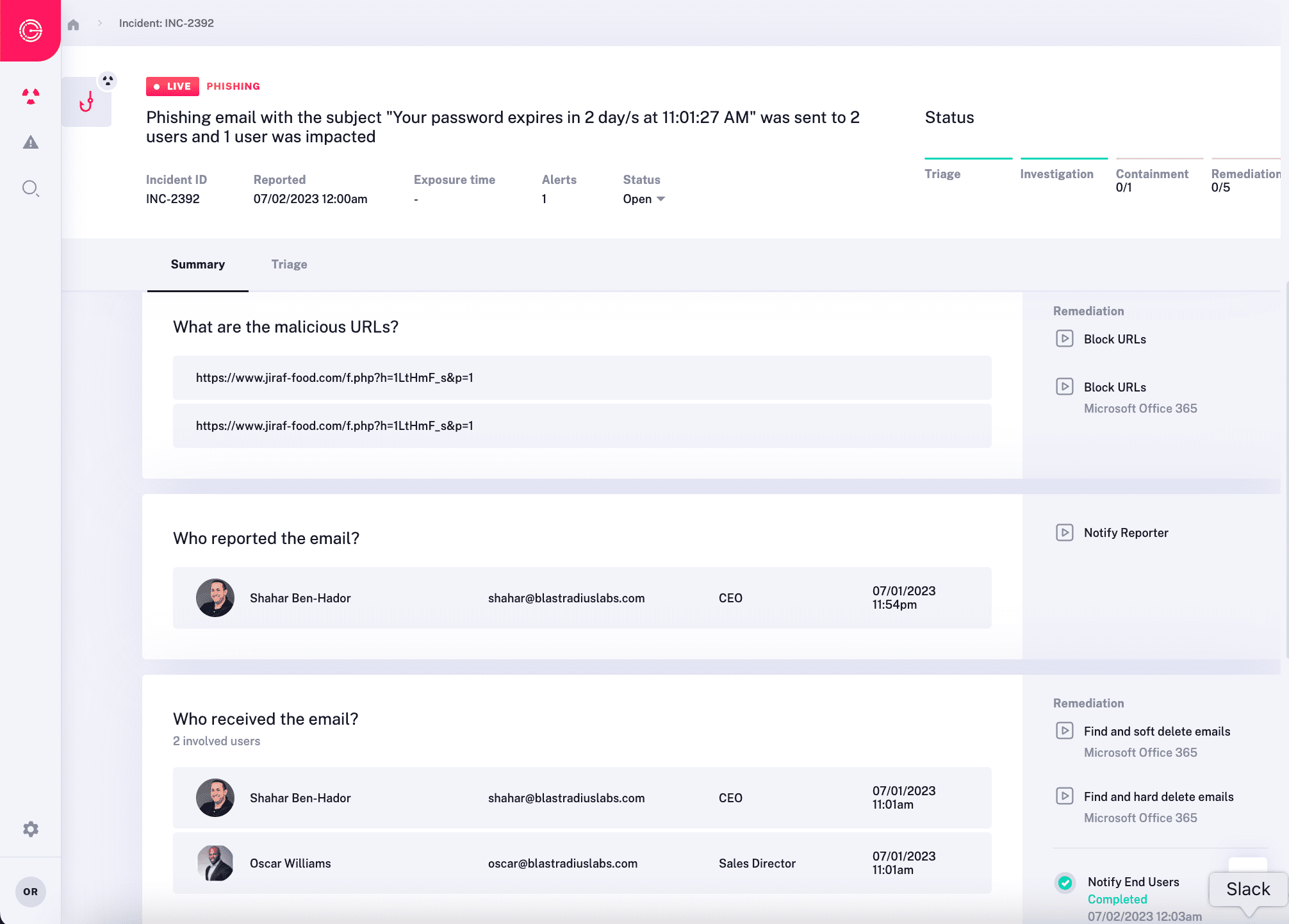
Eliminating Maintenance Overhead
SOAR tools often require complex setup and significant maintenance effort. Even modern alternatives, while easier to implement, still demand mature processes and substantial time investment from security teams to codify them into playbooks, and to keep them running.
- Turnkey Automation – Radiant‘s does not require customization to inspect security alerts and perform triage, investigation, and remediation autonomously from day one. Radiant is up and running within minutes via API integration, sparing you from the high implementation effort typically associated with SOAR tools.
- Maintenance Free Operation – Radiant is constantly adjusting to changes in the attack landscape, your organizational activity, security best practices, vendor APIs, and more. This approach eliminates maintenance by automatically managing and updating the system without your team needing to get involved.
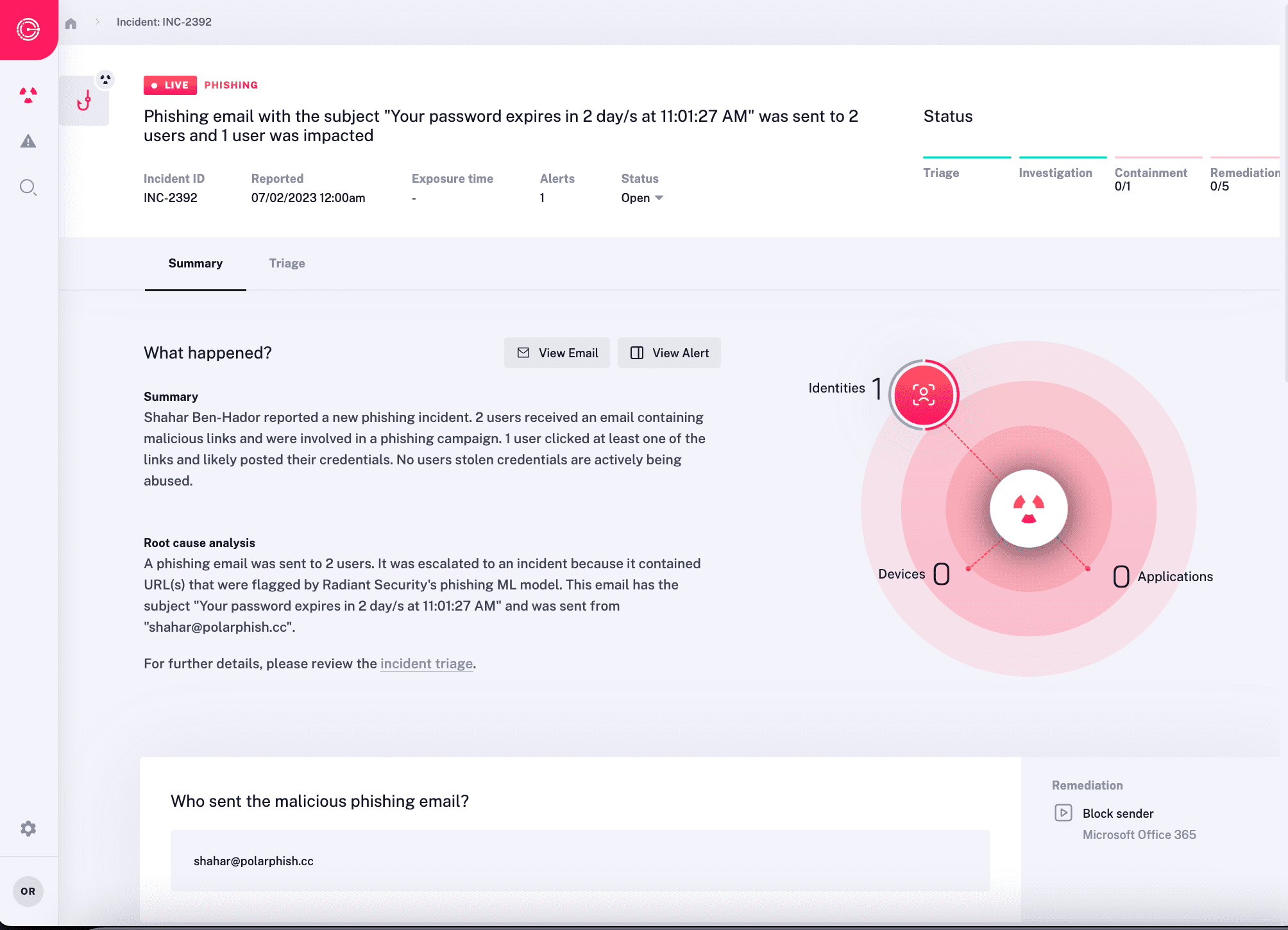
Expanding the Scope of Automation
SOAR systems lack inherent security understanding as they are preprogrammed. Without this understanding of security and your organization’s normal operations, they cannot relieve analysts from intricate responsibilities like result interpretation, root cause analysis, or incident scope determination.
- Automate Root Cause Analysis – Radiant performs a full, in-depth investigation of every malicious incident. It generates a root cause analysis and a full incident scope to make it easy for security analysts to understand what happened.
- Intelligently Respond – When an incident is deemed to be malicious, Radiant develops a customized response plan that will contain, remediate, and improve resiliency to the specific security issues uncovered by the impact analysis. This ensures that the full attack chain is effectively addressed, even if it involves multiple attack types, users, or devices.
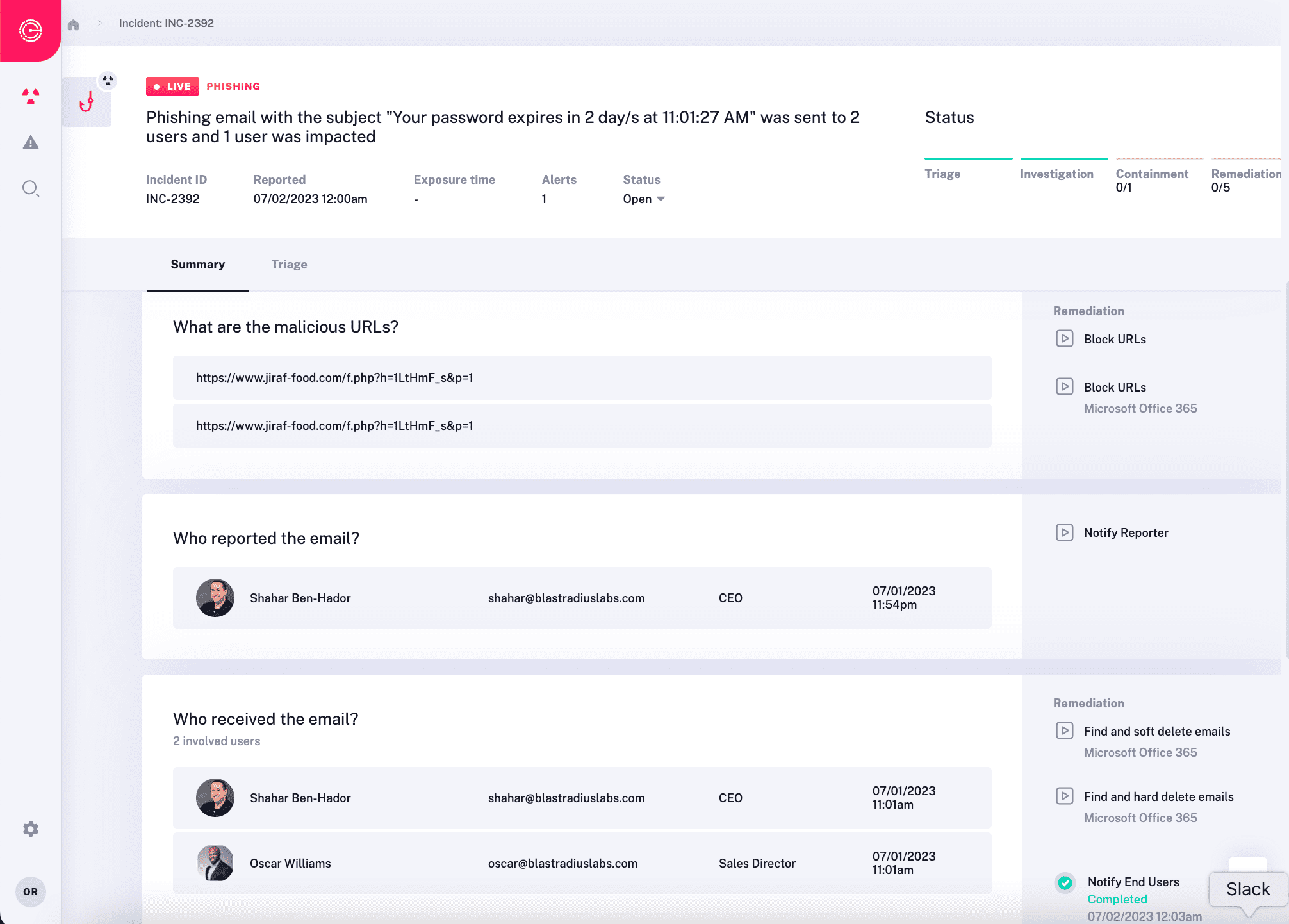
Continuous Learning & Decision Making
SOARs don’t learn. They may gather, distribute, or enrich cases with information from other sources, but they aren’t learning what’s normal for an environment or how the threat landscape is evolving.
- Behavioral Modelling – Radiant constantly learns normal activity for an environment (e.g. behavior, OSs, Browsers, locations, etc.) so that it can evaluate alerts within the context of an organization’s normal operating parameters. This greatly reduces false positives and provides additional context for making triage, investigation, and response decisions.
See it in action
Autonomously triage, investigate, contain and respond to every alert in an automated manner using AI and machine learning.
Request a demo