What Is Arctic Wolf?
Arctic Wolf is a cybersecurity company specializing in managed detection and response (MDR) solutions designed to protect organizations from advanced cyber threats. Founded in 2012, the company delivers managed security monitoring, threat detection, and incident response using a cloud-native security operations platform.
Arctic Wolf acts as an extension of internal IT teams, offering access to dedicated security experts and proprietary technology to help businesses manage risk and respond quickly to incidents. The platform offers a combination of machine learning-driven analytics, log ingestion, and proactive threat hunting.
Arctic Wolf’s approach includes continuous monitoring, tailored response recommendations, and ongoing support, making it suitable for enterprises seeking to outsource some or all of their security operations center (SOC) functions.
Arctic Wolf’s Core Cybersecurity Platform
At the center of Arctic Wolf’s offering is the Aurora platform, a cloud-native, open XDR (extended detection and response) solution designed to deliver broad visibility, accurate threat detection, and efficient incident response. According to Arctic Wolf, Aurora collects over 9 trillion events weekly across endpoints, networks, cloud services, and identities.
The Aurora platform supports multiple core services (managed detection and response, managed risk, managed security awareness, and incident response) within a single architecture. Its operational process follows a three-phase approach:
- Collection: Aurora captures extensive telemetry from multiple sources, ensuring full visibility without data volume limits. Logs are retained on-demand for compliance and investigative purposes under a flat-fee model, allowing organizations to maintain long-term data access without incurring unpredictable costs.
- Enrichment: Arctic Wolf uses commercial and open-source threat intelligence to correlate events and quantify risk. This context includes vulnerabilities, system misconfigurations, and account takeover exposures, helping organizations understand and prioritize real threats. Events are analyzed from multiple perspectives, reducing blind spots.
- Analysis: In the analysis phase, Aurora applies cloud-native analytics and machine learning to detect advanced threats. Custom detection rules tailored to each environment help minimize false positives and identify threats missed by other tools. Alerts are aggregated into incidents, reducing noise and alert fatigue, a common pain point for modern security teams.
Key Arctic Wolf Solutions
Here are the main solutions Arctic Wolf provides on top of its Aurora platform.
1. Arctic Wolf MDR
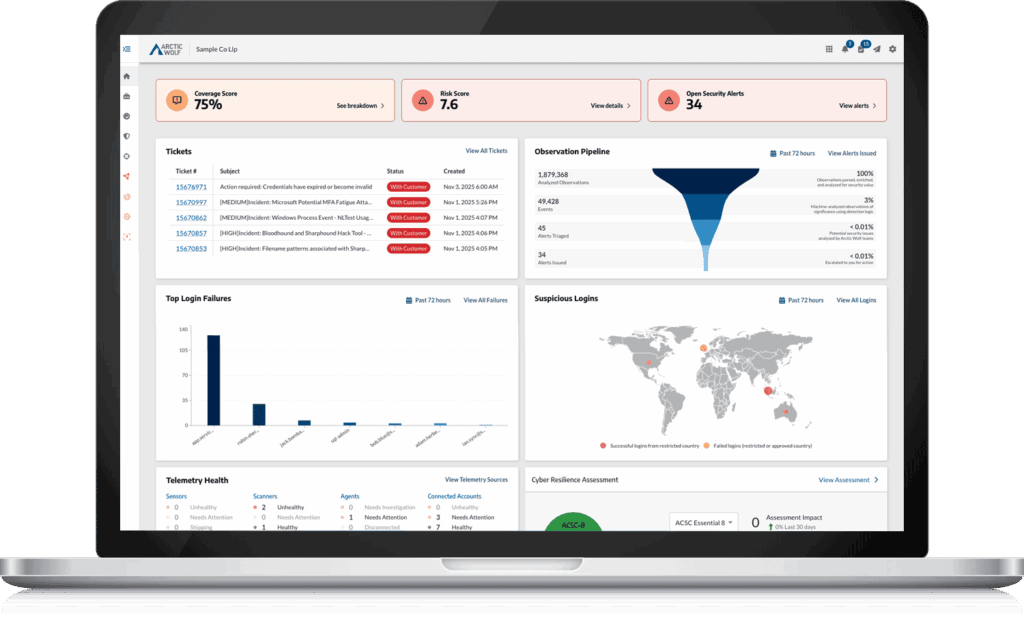
Arctic Wolf’s managed detection and response (MDR) service delivers 24×7 monitoring across endpoints, networks, and cloud environments to detect and neutralize cyber threats. Using broad telemetry and machine learning-powered analytics from the Aurora platform, MDR identifies suspicious activity that traditional tools often miss. The service integrates with existing systems to collect data, profile assets, and continuously monitor for advanced threats.
MDR includes managed investigations, where Arctic Wolf security experts handle alert triage and root cause analysis, reducing the operational burden on internal teams. Guided response workflows ensure threats are properly contained, while personalized engagements help organizations continually improve their security posture. With predictable pricing and log retention included, MDR provides scalable protection that aligns with business needs.
2. Arctic Wolf Incident Response
Arctic Wolf’s incident response (IR) service offers full-spectrum recovery support for cyber incidents, from threat containment to business restoration. Available as a stand-alone service or through the Incident360 Retainer, the IR team provides rapid response to ransomware, business email compromise, data breaches, and active threats.
The service includes threat actor removal, forensic analysis, ransom negotiation, and system recovery. A named incident director coordinates response activities, ensuring consistent communication and reporting across technical and executive teams. The Incident360 Retainer also includes proactive planning such as tabletop exercises and IR plan reviews, allowing customers to respond more effectively when an incident occurs.
On average, Arctic Wolf IR customers recover 15% faster than the industry benchmark and typically avoid paying ransom due to early containment and expert negotiation.
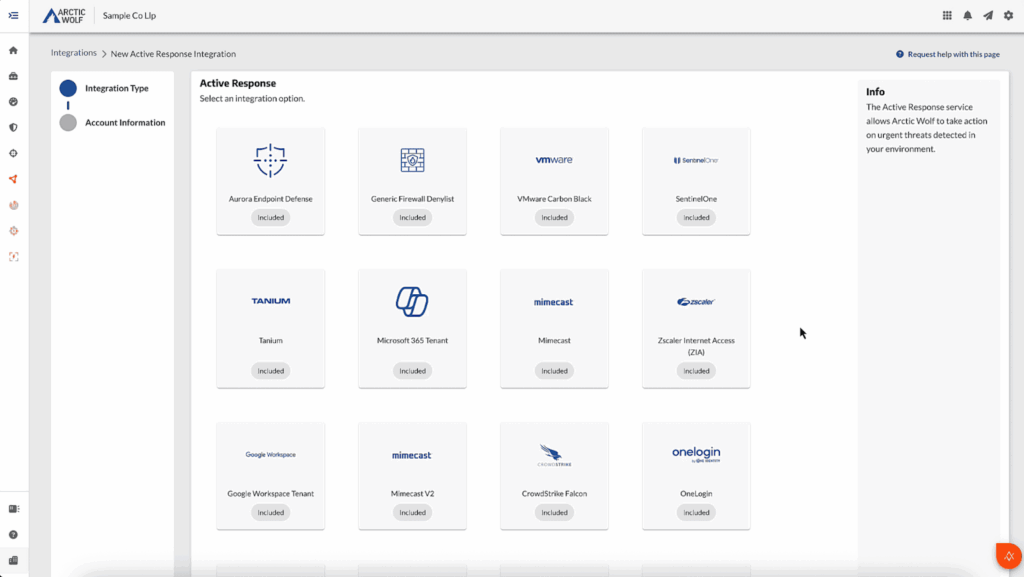
3. Aurora Endpoint Security
Aurora Endpoint Security delivers AI-driven protection, detection, and response to stop threats before they impact business operations. Built on Arctic Wolf’s Aurora platform, it offers a combination of next-generation antivirus, behavioral detection, threat hunting, and automated response playbooks.
The solution supports Windows, macOS, and Linux, and includes features like application and device control, MITRE ATT&CK mapping, and mobile coverage add-ons. Multiple service tiers are available, from standalone protection to fully managed 24×7 endpoint defense with tactical threat insights and guided remediation.
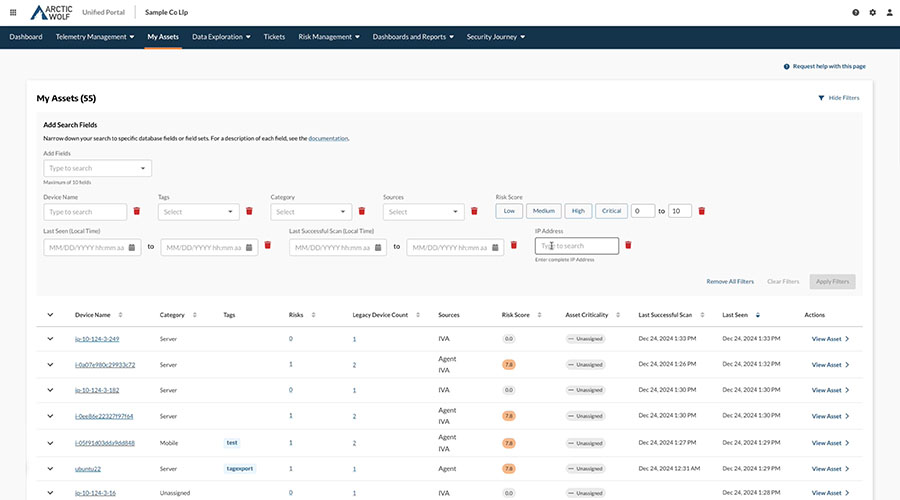
4. Arctic Wolf Agent
The Arctic Wolf Agent is a lightweight endpoint application that provides visibility into endpoint activity, vulnerabilities, and misconfigurations. It supports Arctic Wolf’s MDR and managed risk solutions by delivering real-time telemetry to security operations teams for continuous monitoring.
Designed for minimal performance impact, the agent installs easily via standard deployment tools and requires no ongoing maintenance. It collects detailed system and network data, including process activity, installed software, event logs, and wireless configurations. It also enables host-based vulnerability assessments, security control benchmarking, and managed containment.
Arctic Wolf Pricing Examples
Arctic Wolf solutions are available exclusively through partners like Amazon Web Services (AWS). For example, services can be purchased through the AWS Marketplace, allowing organizations to deploy managed detection and response services directly within their AWS environments.
Pricing on AWS is contract-based and reflects factors such as contract duration, user count, and service tier. Additional AWS infrastructure costs may apply, depending on the deployment model.
A standard 12-month MDR Basic contract, which includes monitoring for up to 100 users, is priced at $44,000 with a 6% cost savings compared to shorter-term agreements. Longer contracts, such as 24- or 36-month options, may offer additional discounts and are typically negotiated based on the organization’s size and requirements.
For large-scale deployments or custom service levels, Arctic Wolf offers custom pricing through private offers. These are tailored agreements that define terms and coverage, often reaching up to $1,000,000 or more depending on the scope. It’s important to note that additional infrastructure costs may apply if the solution is deployed on cloud platforms like AWS.
Note: The information above is accurate as of the time of this writing. Arctic Wolf pricing is subject to change, for up-to-date pricing refer to the official AWS Marketplace product page.
Learn more in our detailed guide to Arctic Wolf pricing
Arctic Wolf Limitations
While Arctic Wolf delivers robust MDR capabilities, users have identified several limitations that may affect usability, integration, and operational efficiency. These issues were reported by users on the G2 platform:
- Alert volume and noise: Users frequently experience a high volume of alerts, which can lead to alert fatigue. Important issues may be buried under less critical notifications, making it harder to prioritize response efforts. Although Arctic Wolf allows alert tuning and snoozing, some noise remains inherent to the process.
- Dashboard usability: The Risk Dashboard could benefit from more advanced filtering and sorting options. New users may also find the number of available screens and data overwhelming during onboarding.
- Portal navigation: Some users find the portal interface unintuitive, especially when trying to locate features or reports. This tends to improve over time but can hinder early usage.
- Ticketing system complexity: The built-in ticketing system is seen as functional but not user-friendly. Navigation can feel cumbersome, especially for teams managing multiple incidents.
- Reporting limitations: Built-in report customization options are limited. For tailored reporting, users must rely on SOC analysts, which can delay access to detailed or specific data views.
- SIEM data accessibility: Customers have limited direct access to the raw SIEM data collected by Arctic Wolf. While the SOC team utilizes this data effectively, the inability for customers to run direct queries can restrict deep-dive analysis.
- Integration gaps: Some users report missing native integrations with tools like Varonis, SonicWall NSM, and Auvik. Workarounds exist, but they may require extra configuration effort.
- Mac agent deployment: Deploying the Arctic Wolf agent to macOS devices currently requires manual installation, unlike Windows systems which support centralized deployment via tools like Intune.
- Long setup timeline: Achieving a meaningful security posture with Arctic Wolf is not immediate. Full implementation can take several months, especially across complex environments, due to the layered nature of security coverage.
- Pricing and team consistency: Some users note higher initial costs, though many find pricing negotiable. Additionally, changes in concierge security team members over time can affect continuity, although the quality of support remains strong.
Notable Arctic Wolf Competitors
In light of the above limitation, some organizations are evaluating competitors and alternatives to Arctic Wolf. Let’s review a few popular options.
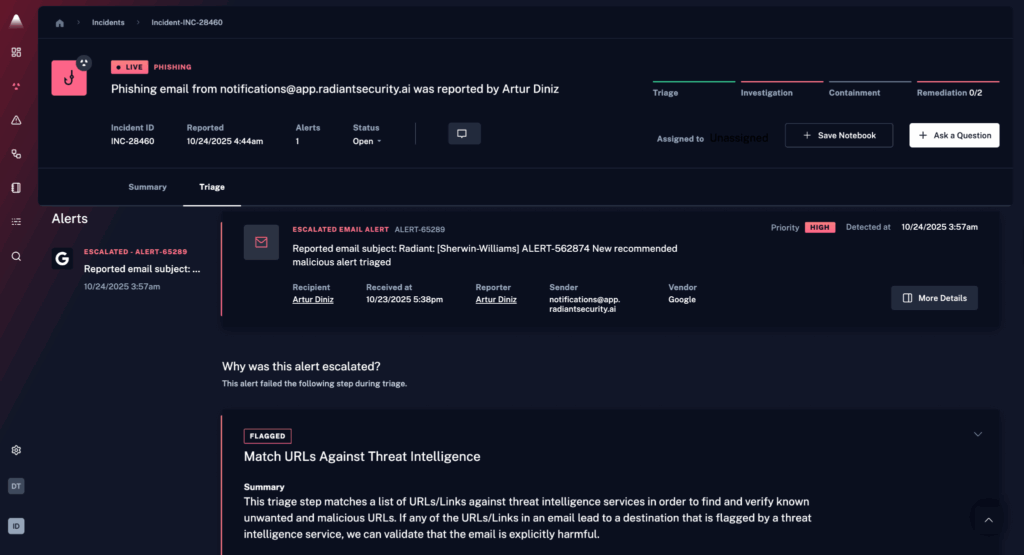
1. Radiant Security
Radiant Security is an Agentic AI SOC platform that automates alert triage, investigation, and response across the security lifecycle. The platform is designed to reduce false positives by roughly 90%, enabling analysts to spend more time on verified threats rather than manual triage. Radiant also aims to shorten investigation and response times (MTTR) and lower operational costs, while helping teams avoid the fatigue that often comes with high alert volume.
Key capabilities include:
- Agentic AI triage and investigation for all alert types, including previously unseen or low-fidelity ones.
- Transparent reasoning that shows how and why the AI reached its conclusions, helping analysts validate decisions and build trust.
- Integrated response with one-click, executable action plans that can be carried out manually or automated when appropriate.
- Log management with unlimited retention, delivered at a cost significantly lower than traditional SIEM platforms.
- AI feedback loop that allows teams to influence and adjust triage behavior using environmental context, improving accuracy over time.
Radiant provides a unified environment for handling alerts, investigations, response actions, and log data, with an emphasis on efficiency, clarity, and analyst control.
2. CrowdStrike Falcon
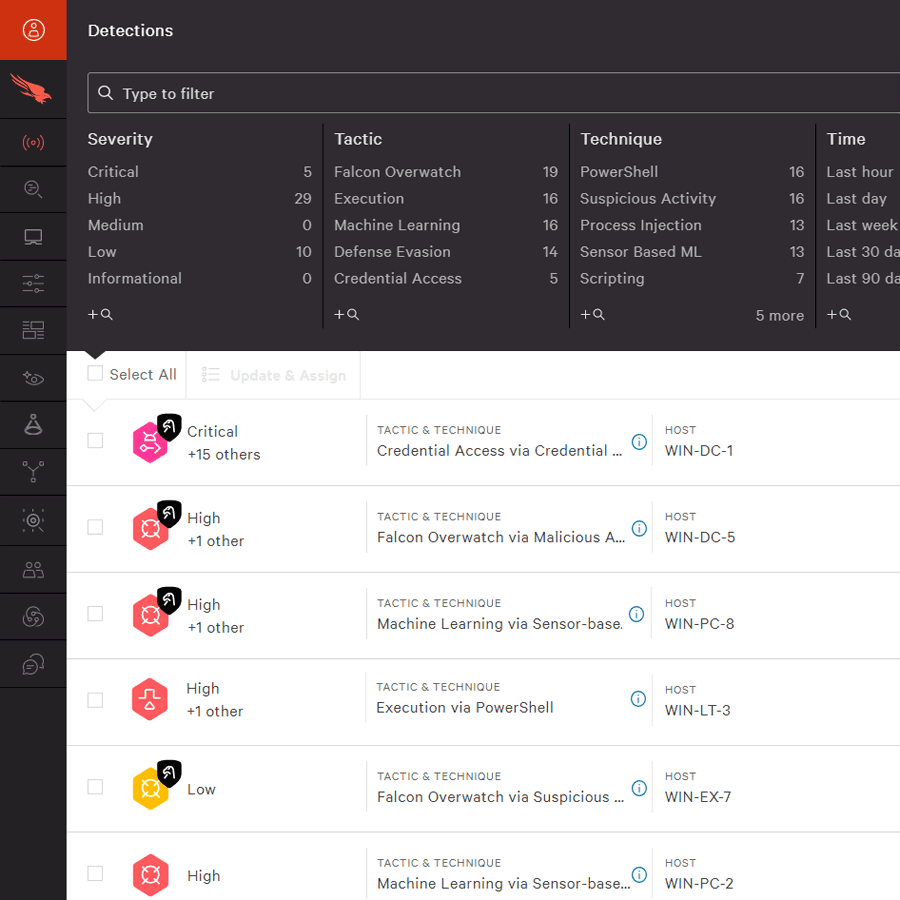
CrowdStrike competes with Arctic Wolf by offering an integrated, AI-driven security platform built around automation and data correlation. Its Falcon platform is centered on the Enterprise Graph, a unified data layer that consolidates telemetry across the enterprise, providing rich context for detection and response. Instead of relying heavily on human analysts, CrowdStrike uses agentic security workflows, automated agents that handle triage and routine tasks.
Key features include:
- Enterprise graph: An AI-ready data layer that unifies telemetry and enables complex queries across endpoints, identities, and workloads
- Agentic security agents: Automated software agents that manage detection triage, response actions, and routine tasks
- Charlotte AI AgentWorks: No-code platform for building, deploying, and managing security agents using natural language prompts
- Dynamic user interface: Role-specific dashboards with support for natural language querying to simplify investigations
- SOC integration: Agent Collaboration Framework connects data, systems, and agents for coordinated, contextual incident response
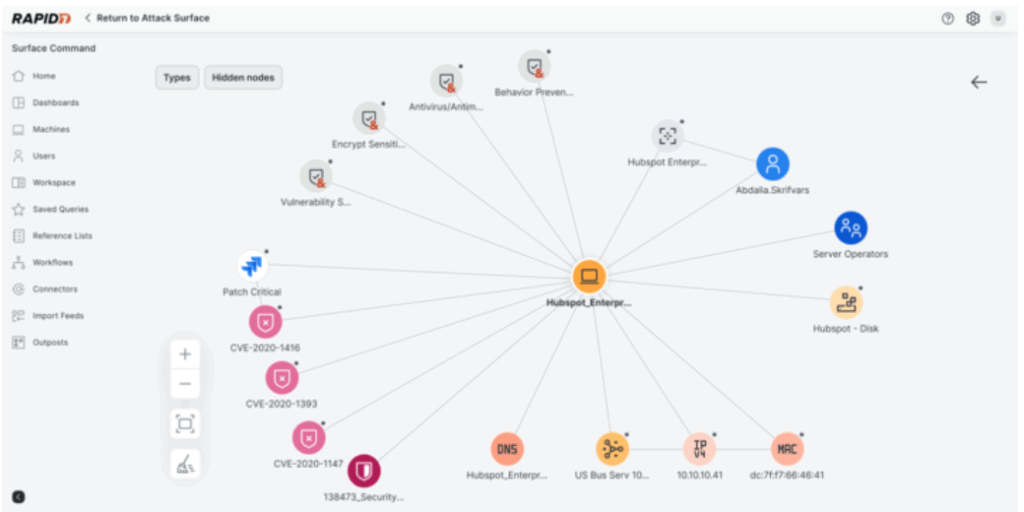
3. Rapid7 Command Platform
Rapid7 competes with Arctic Wolf through its Command Platform, an integrated cybersecurity solution designed to give security teams control over their attack surface. The platform combines AI-driven threat detection, real-time visibility, and automated response to accelerate decision-making and reduce manual workloads.
Key features include:
- Surface command: Provides continuous 360° visibility across the entire attack surface, enabling rapid detection and prioritization of security issues from endpoints to the cloud
- Exposure command: Delivers threat-aware exposure management and remediation prioritization, reducing risk by identifying and mitigating high-impact vulnerabilities
- AI-powered threat detection: Built on 20 years of curated data, Rapid7’s AI engine identifies threats and validates malicious activity to reduce false positives
- Integrated MDR services: Offers always-on managed detection and response with unlimited incident response support and extended detection across the kill chain
- Automation and integration: Simplifies workflows by integrating data sources and automating routine tasks, accelerating response and reducing operational drag
4. BlueVoyant Cyber Defense Platform
BlueVoyant positions itself as a competitor to Arctic Wolf by offering a Cyber Defense Platform (CDP) that unifies managed detection and response (MDR), third-party risk management (TPRM), and digital risk protection (DRP) into a single, integrated solution. Built to provide end-to-end visibility and threat mitigation, the platform combines proprietary threat intelligence, automation, and strategic advisory services to protect internal and external digital ecosystems.
Key features include:
- Unified SecOps platform: Integrates MDR, TPRM, and DRP into a single interface for cohesive security operations and simplified management
- Managed detection & response: Offers MDR across major ecosystems including Microsoft, Splunk, and Cisco XDR, with AI and automation for fast threat detection and neutralization
- Third-party risk management (TPRM): Enables continuous monitoring of vendors, risk assessments, and remediation workflows to reduce supply chain risk
- Digital risk protection (DRP): Includes brand protection, dark web monitoring, and executive threat coverage to secure external-facing digital assets
- Integrated threat intelligence: Consolidates threat data to improve detection accuracy and response speed across all security domains
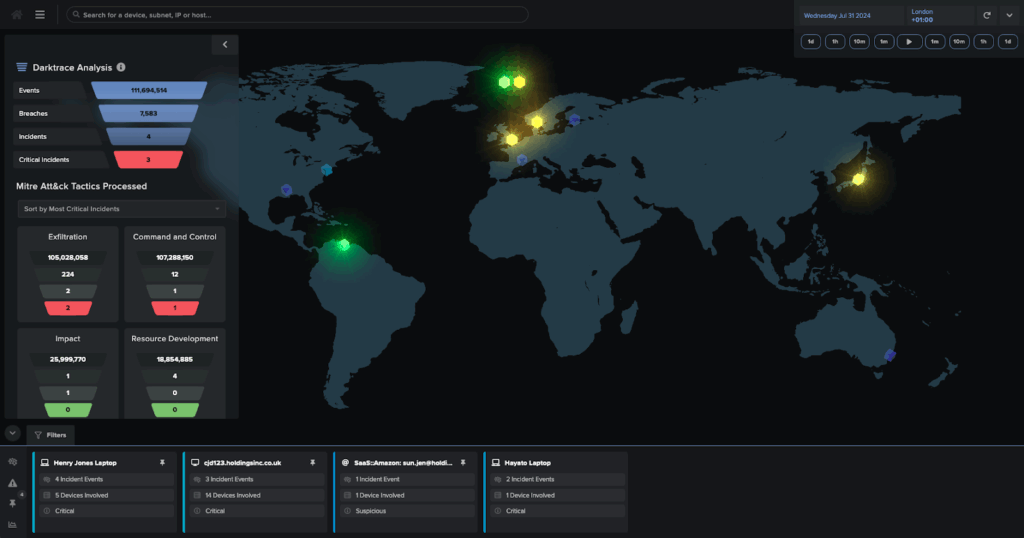
5. Darktrace ActiveAI Security Platform
Darktrace offers a fully integrated, AI-driven cybersecurity platform that focuses on proactive cyber resilience. The Darktrace ActiveAI Security Platform uses self-learning AI to understand an organization’s normal behavior and autonomously detect and respond to known and unknown threats.
Key features include:
- Self-learning AI: Continuously learns the unique behaviors of users, devices, and systems to detect emerging threats
- Autonomous response: Automatically responds to threats across environments, reducing time-to-containment and limiting damage without waiting for human intervention
- Proactive exposure management: Identifies security gaps and potential attack paths across infrastructure to reduce risk before exploitation occurs
- Attack surface management: Offers visibility into digital assets, including shadow IT, helping teams understand and control their external exposure
- Integrated product coverage: Protects across key domains including email, endpoint, network, cloud, identity, and OT environments
Conclusion
While Arctic Wolf offers a broad and well-integrated suite of managed cybersecurity services, its platform presents notable limitations that may impact security team efficiency and agility. Alert volume, interface complexity, limited data access, and slower deployment timelines are recurring concerns. Additionally, some users report high costs and gaps in integration with common tools. Given these trade-offs, organizations seeking faster implementation, greater customization, or stronger automation capabilities should consider alternative providers

