Company Profile
Spellman High Voltage Electronics Corporation is a global leader in high-voltage power supply technology, headquartered in Hauppauge, New York, with over 2,100 employees worldwide. They specialize in precision DC high-voltage power supplies, X-ray generators, and Monoblock® X-ray sources, serving critical applications in medical, industrial, and scientific industries.
The Challenges: False Positive Alerts Taking a Toll on The SOC Team
A company like Spellman High Voltage, operating in advanced manufacturing and high-tech industries, faces a unique set of cybersecurity challenges due to its involvement in critical technologies, global operations, and partnerships with sensitive sectors like medical, industrial, and scientific applications.
The information security team at Spellman High Voltage deals with various complex cybersecurity threats such as:
- IP (intellectual property) protection
- Supply chain security
- Industrial control systems (ICS) vulnerabilities
- Regulatory compliance
- Ransomware and cyber extortion
- Customer data and trust
- Advanced persistent threats (APTs)
Addressing these challenges and ensuring the organization remains safe kept the information security team quite busy.
The threat detection systems implemented to safeguard the expanding attack surface generated numerous false positive alerts, consuming a significant amount of the security engineers’ time and effort. The combination of limited resources and manual, time-consuming investigations led to slow response times, creating an unnecessary security risk that did not align with the high standards they were aiming to maintain.
Increasing the headcount of the Security Operations Center (SOC) to address their resource challenges was not viewed as a viable option.
- Talent shortage: Finding, training, and retaining experienced security professionals to staff the SOC is highly challenging.
- High costs: Expanding an in-house Security Operations Center (SOC) is expensive and not scalable.
- Inconsistent quality: Incident triage, investigation, and response quality is inconsistent and varies significantly based on the analyst handling the incident, as well as their skill, knowledge, and experience level.
Michael Butler, the Director of Security Operations at Spellman High Voltage, aimed to find a technological solution that would automate the triage and investigation of Tier-I SOC alerts, allowing for faster and more efficient resolution of alerts with the highest quality.
“The impact of the number of phishing and identity issues was significant for the team. We spent many extra hours and effort that could be spent elsewhere.”
Radiant’s Solution: AI SOC Analysts That Autonomously Triage, Investigate and Resolve Tier-I Security Alerts, at Any Scale
Following a successful POC, Michael chose Radiant Security to help Spellman High Voltage’s SOC team swiftly and automatically triage, investigate, and resolve their high number of Tier-I alerts without increasing headcount.
About Radiant Security
Radiant Security is an AI-powered platform that autonomously triages, investigates, and responds to security alerts, empowering security teams to address all received alerts. With complete impact and root cause analysis, Radiant provides effective, automated remediation that can be setup in minutes via APIs and reduces workloads by up to 95%.
The process of onboarding and integrating with existing systems was smooth, brief, and effortless.
Radiant Security’s AI SOC analysts immediately minimized the “noise” level by automating 15% of their workload, reducing the number of alerts the SOC team has to handle.
The platform’s triage and investigation capability helps Spellman High Voltage automatically resolve alerts at any scale, faster, with the quality of their best analyst.
“With Radiant Security’s Automation, we’re saving something between 200-300 hours a month on Tier-I SOC Analysis and Resolution.”
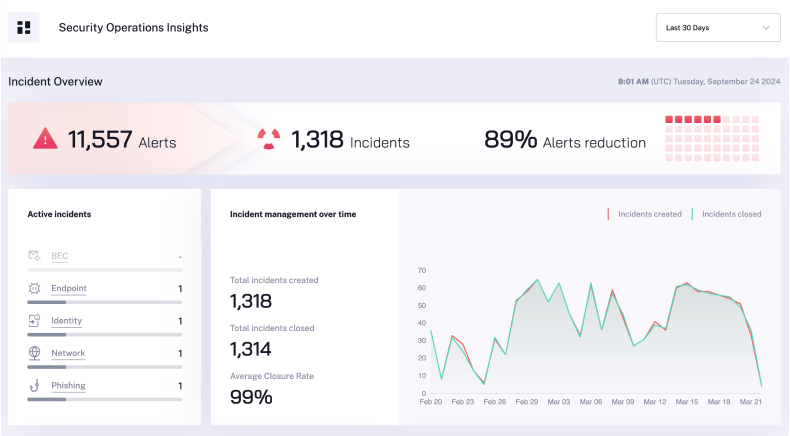
The Results: Improved Detection and Response, Freeing Engineers for Innovation and Special Projects
Radiant Security’s AI SOC Analysts removed the SOC resource bottleneck, freed up analysts, and enabled Spellman High Voltage to:
- Reduce MTTD to 10x better than the industry average
- Improve their threat detection by automatically finding true attacks in a sea of false positives
- Reduce MTTR to 2x better than the industry average
- Focus their time and resources on innovation
- Have peace of mind, knowing that every alert is always being handled correctly.
“The team is great to work with, and I can’t stress that enough. Having the CEO accessible, developers when needed, and customizing the platform based on our feedback is a big win for Spellman High Voltage.”

