Automatically Investigate Suspicious Logins with AI
Harness the power of AI and automation to effectively triage and investigate & remediate abnormal access alerts.
Abnormal Identity Access Alerts Are a Pain to Triage
-
Behavioral Understanding is Mandatory
Without an understanding of normal activity for an environment, triaging & investigating identity based threats is near impossible.
-
Communication Intensive Workflows
Addressing identity-based threats involves a lot of communication with end users and stakeholders. This dynamic nature presents challenges for automation.
-
Time is of the Essence
True positives must be addressed as quickly as possible to minimize unauthorized access to systems by way of compromised accounts.
How Radiant Automates Identity Alert Workflows
Radiant automatically triages every suspicious login alert with an AI-based engine, then performs an in depth impact analysis to determine root cause and uncover the full incident scope. Finally, Radiant auto-remediates the incident and notifies affected users of the incident outcome and corrective steps.
Triage Suspicious Login Alerts Autonomously
Radiant utilizes an AI-powered triage engine to analyze each identity alert, alongside your organization’s learned operating patterns and data from other non-identify security sources to determine an alert’s maliciousness.
- Limitless Capacity – Autonomously triage every alert by understanding if the behavior is normal, how it might be connected to other activity in your environment, and automatically interact with potentially affected end users.
- Dynamic Analysis – Radiant’s AI autonomously examines security alerts, identity activity and behavioral data. Based on its findings it performs dozens to hundreds of additional inspections to accurately determine maliciousness of an alert.
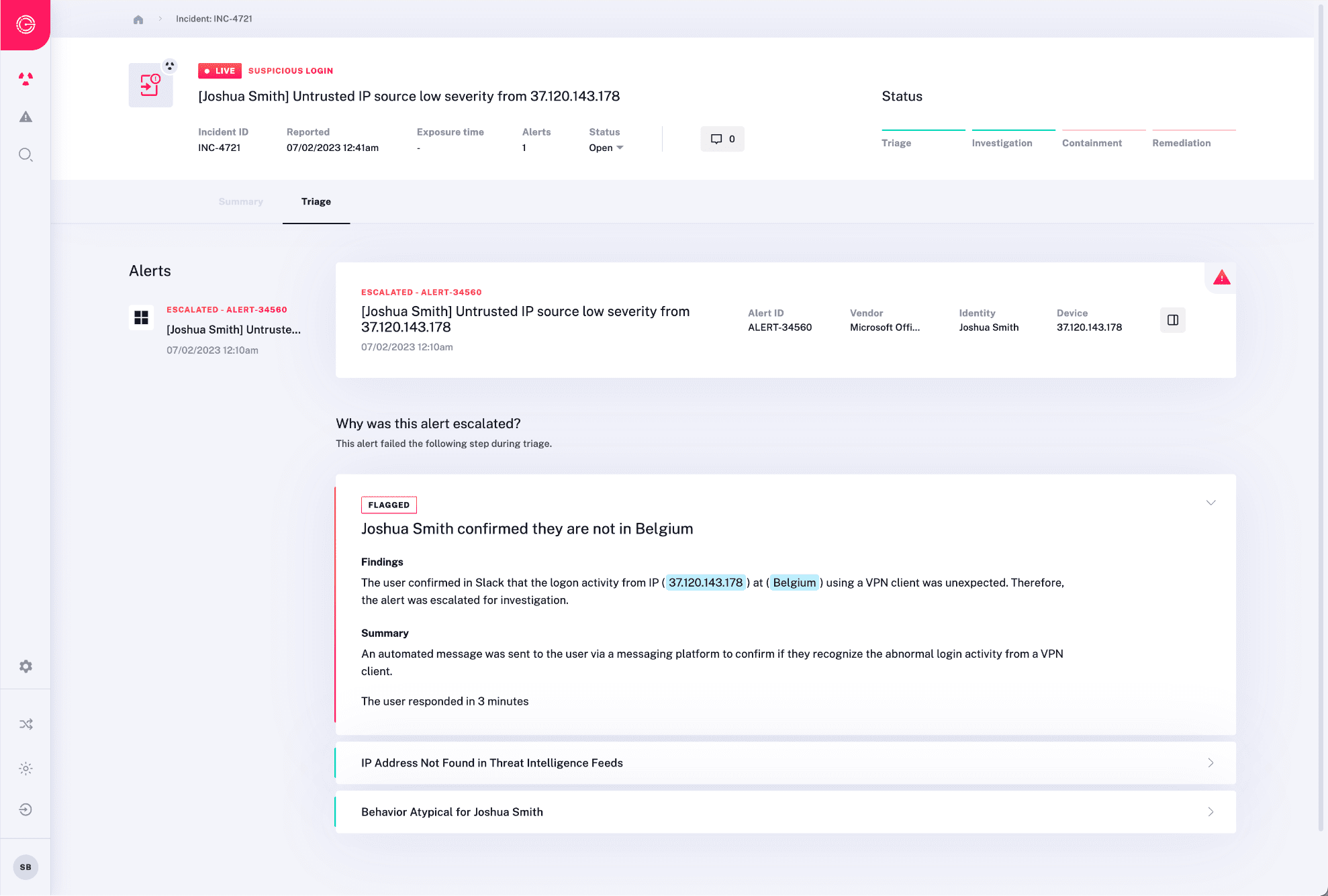
Uncover Complete Incident Scope
Identity threats like compromised credentials must be quickly and comprehensively identified in order to avoid further system compromise. Radiant automatically identifies the root cause and entire incident scope for all malicious alerts.
- See the Entire Attack – Radiant stitches together data from multiple sources (e.g. email, identity, endpoint, network, and more) to follow the thread of incidents across attack types and data sources. This ensures no parts of an attack are missed, and are left unaddressed.
- Understand Root Cause – Obtain a comprehensive impact and root cause analysis for each account take over including the incident’s complete scope, and any activity performed with the compromised credentials.
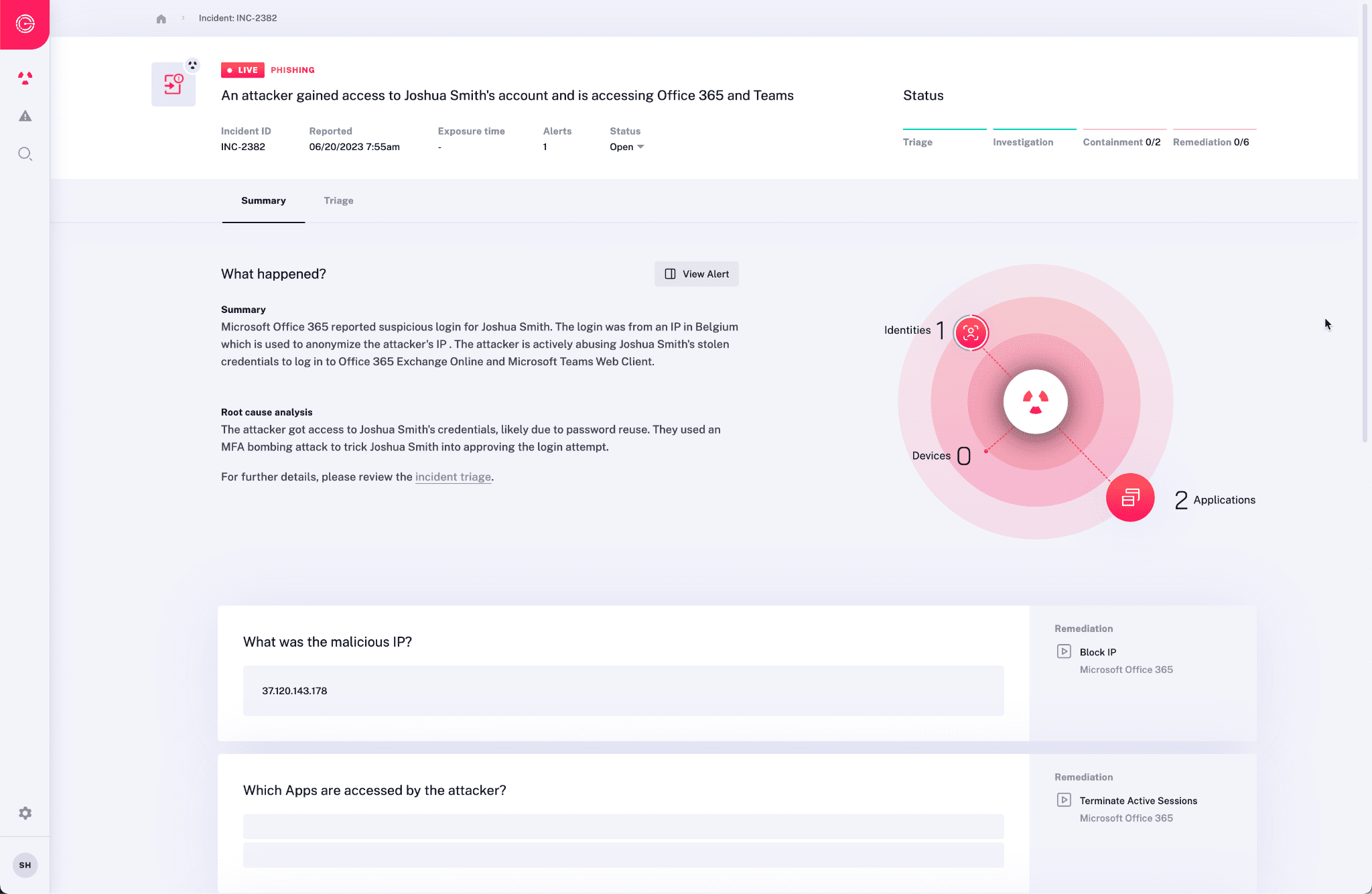
Intelligently Address Identity Issues
Radiant automates containment and remediation of uncovered threats to quickly stop the spread of attacks and restore system health. Radiant’s response actions are tailored to address the specific problems uncovered in impact analysis. For example, locking an impacted identity, terminating any active sessions, resetting its password.
- Dynamic Response Plans – Radiant sets itself apart from other SOC tools by eliminating static or predefined playbooks. Instead, its AI dynamically chooses and executes corrective actions based on the findings of impact analysis.
- Flexible Automation Options – Work within your preferred comfort level of automation. Radiant offers instructions for security analysts to take manual actions using your tools, one-click resolution of items from Radiant, or the choice of a fully-automated response.
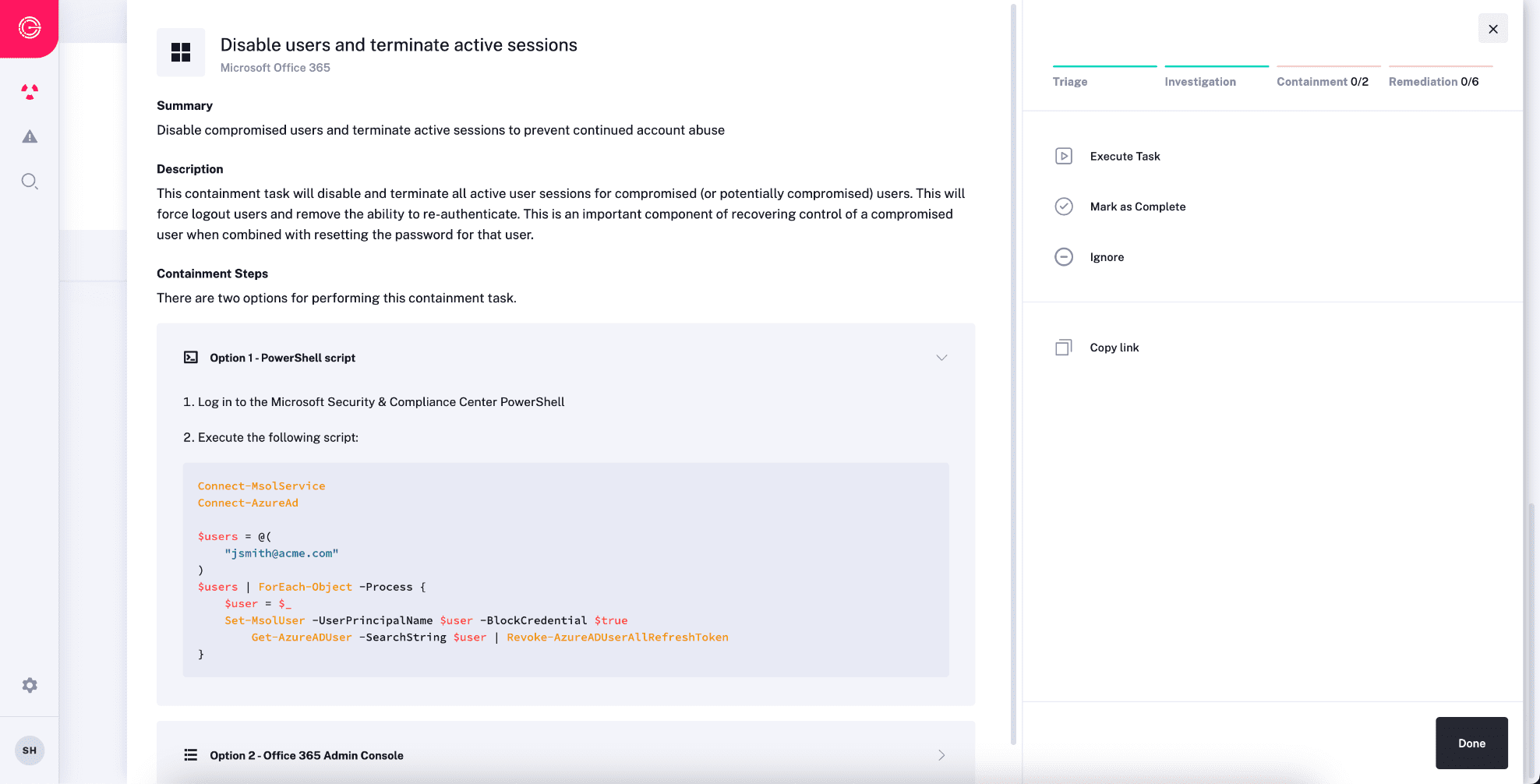
Expedite Escalation & Approval
- Addressing the complete scope of incidents often involves seeking approval from non-security business partners for necessary corrective tasks, such as locking an identity, terminating active sessions, and resetting passwords.
- Streamline Approvals – Secure permissions for corrective actions directly within Radiant’s response workflows, enabling your security team to promptly address potential threats with efficiency.
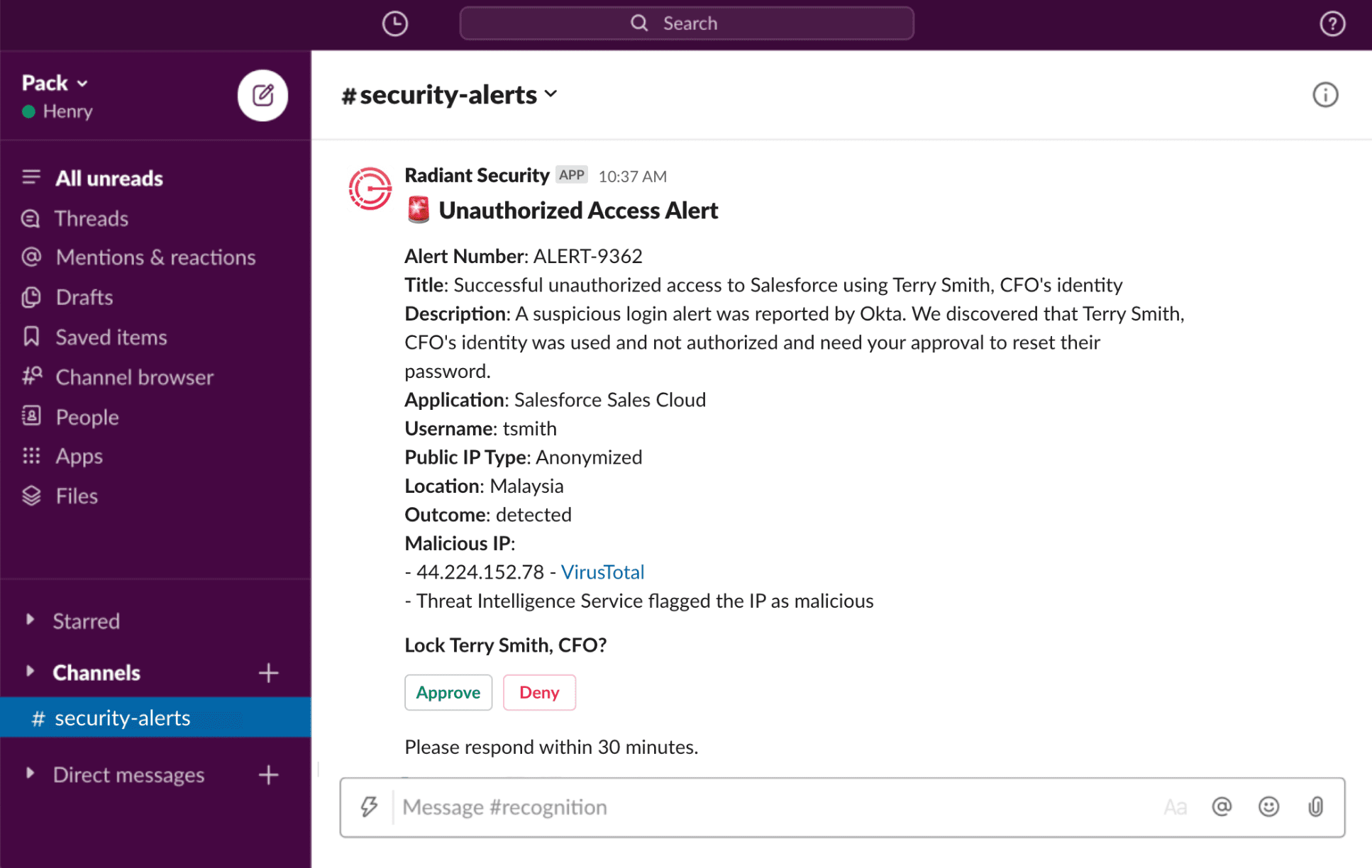
Automate Communication & Notification
Automated communication plays a vital role in the efficient investigation and response to identity threats. Radiant enables seamless and timely information exchange among stakeholders, enabling efficient collaboration and prompt decision-making to mitigate risks effectively.
- Custom Response Templates – Use customizable templates as part of granular response workflows, providing updates on submission status, outcomes, and corrective actions taken.
- Productivity tool integration – Interact with your teams using the tools they are accustomed to, including Slack, Teams, email, and more.
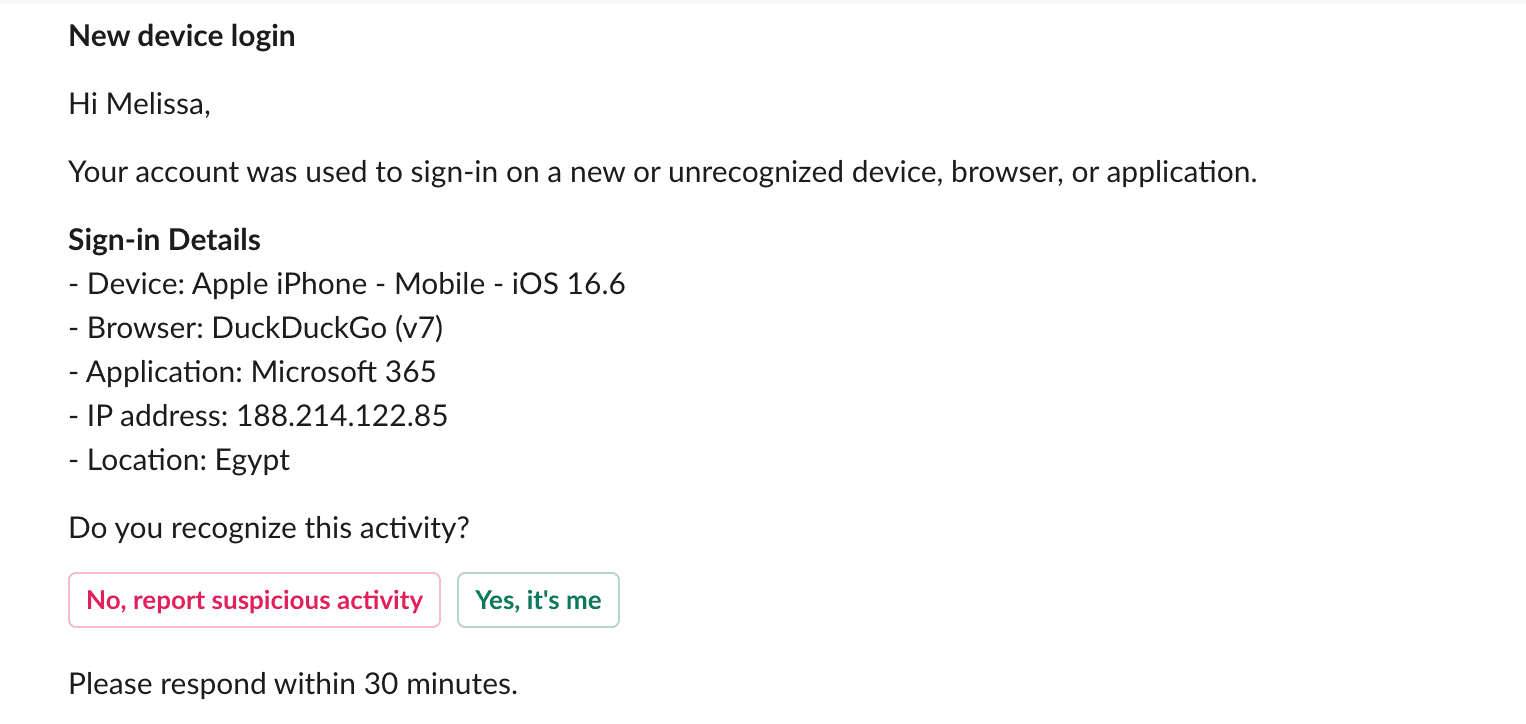
Improve Resiliency
Implementing safeguards within an organization is crucial to minimizing the chance of a future recurrence. After an incident has concluded, Radiant may suggest steps that can be taken to improve environmental resilience, such as blocking certain network providers, disabling text-based MFA, or enrolling users in MFA brute force security training.
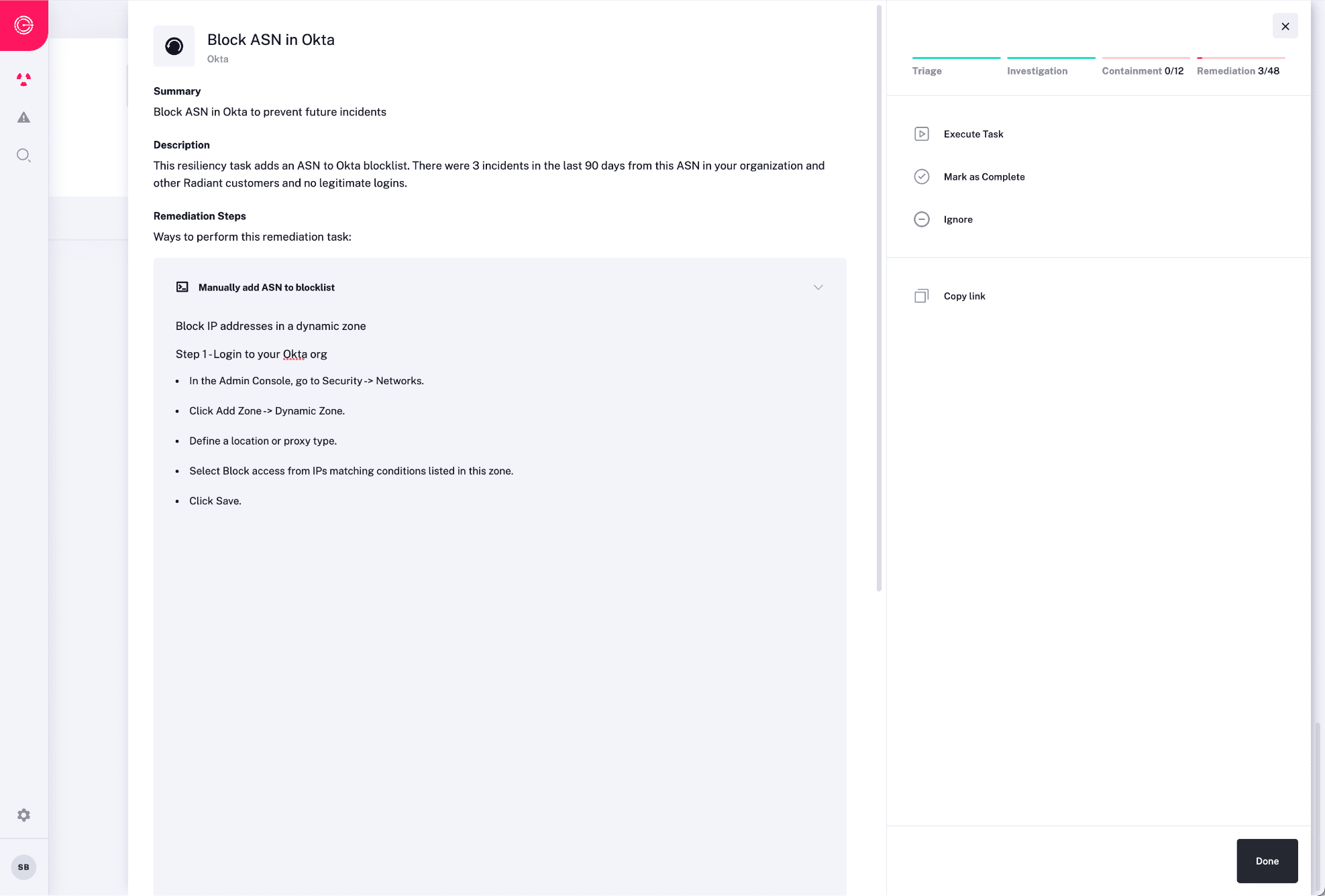
See it in action
Automatically triage, investigate, contain and respond to every alert in an automated manner using AI and machine learning.
Product tour