What Are Enterprise AI SOC Solutions?
Enterprise-grade AI SOC (Security Operations Center) solutions use artificial intelligence to automate threat detection, analysis, and response. These solutions move beyond manual tasks to handle massive alert volumes, reduce false positives, and provide deeper insights, helping security teams scale, cut costs, and fight advanced threats faster. Notable providers include Radiant Security, Torq, and Dropzone.
Key capabilities and benefits include:
- Automated alert triage: AI analyzes and prioritizes alerts, focusing analysts on high-risk threats, reducing alert fatigue.
- Faster incident response: Automates investigation steps, correlating data from multiple tools for quicker context and remediation.
- Enhanced threat detection: Identifies complex threats missed by traditional methods, using machine learning for anomaly detection.
- Deeper insights: Provides forensic-level analysis and explainable AI (XAI) for transparent, auditable decisions.
- Scalability: Scales security operations without proportional headcount increases, handling more alerts efficiently.
- Cost optimization: Reduces reliance on large teams and expensive manual labor, offsetting tech costs.
This is part of a series of articles about SOC services.
Key Capabilities of AI SOC Solutions for the Enterprise
Automated Alert Triage
Automated alert triage is one of the most valuable features of AI SOC tools. Large enterprises often face millions of alerts daily, most of which are false positives or low-risk issues. AI SOC platforms use models to sift through these alerts in real-time, prioritizing the most critical incidents for analyst attention and eliminating noise. As a result, security teams spend less time reviewing benign activity and can focus efforts on genuine threats that require human expertise.
By applying context-aware analysis and correlating data from multiple sources, AI-driven triage increases the efficiency and accuracy of security operations. It helps reduce analyst fatigue, minimizes human error, and ensures that urgent threats are never overlooked due to alert overload.
Enhanced Threat Detection
AI SOC solutions excel at detecting both known and unknown threats using analytics, machine learning, and behavioral modeling. These tools can identify subtle anomalies that traditional, rule-based systems might miss, such as zero-day attacks or sophisticated lateral movement within networks. Continuous learning from historical data and evolving attack techniques ensures that threat detection methods stay ahead of adversaries.
The integration of threat intelligence feeds and heuristic analysis further strengthens the detection capability. AI SOC platforms can correlate vast streams of internal log data with external threat intelligence for a comprehensive view of the threat landscape. This multi-dimensional approach elevates detection accuracy and gives security teams early warnings before attacks escalate.
Deeper Security Insights
AI SOC platforms provide advanced visibility into security events by combining large-scale data analysis with explainable AI (XAI). These systems can analyze relationships across billions of logs, endpoints, and network flows to uncover hidden patterns, lateral movement, or persistent threats that evade traditional tools. Unlike legacy systems that rely heavily on predefined rules, AI models continuously adapt, identifying anomalies based on evolving context and behavior.
Explainable AI adds transparency to this process by showing why a certain alert was prioritized or why a threat was classified as high risk. This helps analysts trust and validate AI-driven decisions, supporting forensic investigations and compliance requirements. The result is deeper understanding, faster root cause analysis, and more confident threat resolution, even in complex or multi-vector attacks.
Orchestration and Workflow Automation
AI SOC tools often include built-in SOAR (security orchestration, automation, and response) capabilities or integrate with external SOAR platforms. These workflows automate repetitive tasks—like user lookups, IP enrichment, malware detonation, or ticket creation—reducing the manual effort required for each incident.
By orchestrating responses across firewalls, endpoint agents, identity systems, and ticketing platforms, AI SOCs accelerate threat containment. For example, once an alert is confirmed as malicious, the system can auto-isolate affected hosts or block offending IPs without waiting for human approval. This level of automation improves response consistency, minimizes delays, and frees up analysts for higher-value tasks like threat hunting or post-incident review.
Related content: Read our guide to AI SOC services
Enterprise Benefits of AI SOC Solutions
Here are some of the main advantages AI SOC technology can provide for large enterprises.
Faster Incident Response
AI SOC tools enable faster incident response by automating investigation processes and orchestrating remediation tasks. When a threat is detected, these platforms can automatically collect relevant data, execute containment actions, and even coordinate with other IT systems for immediate incident containment. This reduces the typical delay that occurs while waiting for human analysts to initiate response protocols.
Scalability Across Environments
AI SOC solutions are built to scale across hybrid and multi-cloud environments, making them suitable for enterprises with distributed infrastructure. Unlike traditional systems that struggle with large or fragmented data sources, AI SOC platforms can ingest and process data from on-premise systems, cloud workloads, SaaS applications, and edge devices in near real-time.
Cost Optimization and Analyst Efficiency
By automating manual processes and reducing alert volumes, AI SOCs significantly lower the operational costs of running a security team. Enterprises can shift from hiring large teams of L1/L2 analysts to supporting smaller, higher-skilled teams focused on strategic tasks. This efficiency translates to reduced overhead in analyst training, retention, and burnout management.
Notable AI SOC Solutions for Enterprises
1. Radiant Security
Radiant Security is an Agentic AI SOC platform that automates alert triage, investigation, and response across the security lifecycle. The platform is designed to reduce false positives by roughly 90%, enabling analysts to spend more time on verified threats rather than manual triage. Radiant also aims to shorten investigation and response times (MTTR) and lower operational costs, while helping teams avoid the fatigue that often comes with high alert volume.
Key capabilities include:
- Agentic AI triage and investigation for all alert types, including previously unseen or low-fidelity ones.
- Transparent reasoning that shows how and why the AI reached its conclusions, helping analysts validate decisions and build trust.
- Integrated response with one-click, executable action plans that can be carried out manually or automated when appropriate.
- Log management with unlimited retention, delivered at a cost significantly lower than traditional SIEM platforms.
- AI feedback loop that allows teams to influence and adjust triage behavior using environmental context, improving accuracy over time.
Radiant provides a unified environment for handling alerts, investigations, response actions, and log data, with an emphasis on efficiency, clarity, and analyst control.
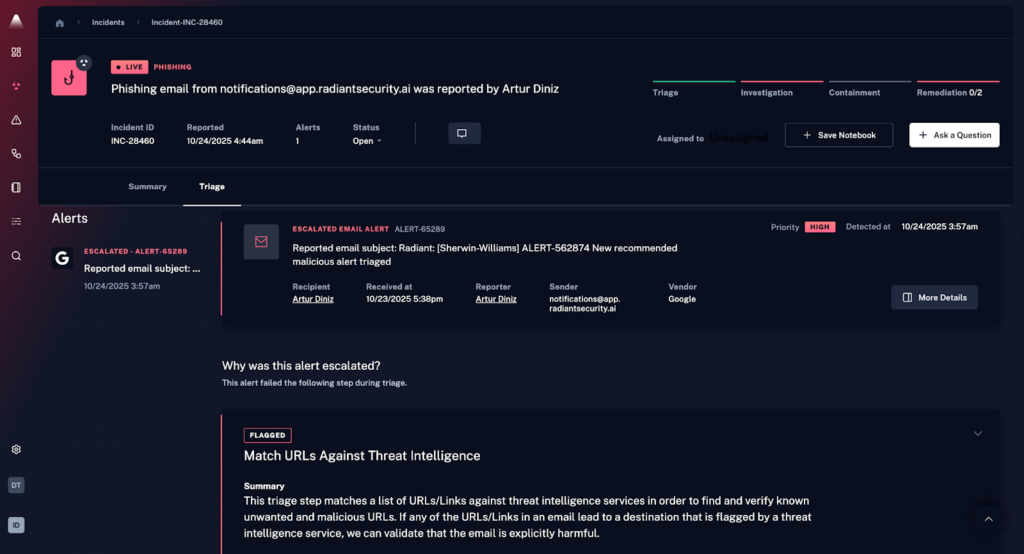
Source: Radiant Security
2. Torq HyperSOC
Torq HyperSOC is an autonomous, AI-powered SOC platform built to address critical limitations in traditional security operations, such as alert overload, talent shortages, and slow incident response. It combines a multi-agent system (MAS) with a hyperautomation engine to automate every phase of the SOC lifecycle, from triage to remediation.
General features include:
- Autonomous case management: Automatically creates and prioritizes enriched security cases with AI-generated summaries for rapid analyst context
- Agentic AI coordination: Uses specialized AI agents to manage triage, investigation, and remediation across thousands of alerts
- Hyperautomation workflows: Automates response actions using predefined runbooks and adaptive logic across integrated tools
- Real-time and historical context: Combines live telemetry with prior data to accelerate root cause analysis
Enterprise features include:
- Tier-1 alert offloading: Designed to autonomously handle high volumes of Tier-1 alerts at scale
- Customized triage strategies: Enables tailored workflows and response playbooks to match organizational processes
- Machine-speed response: Reduces time to resolution through automated actions across firewalls, identity tools, and endpoints
- Audit-ready case summaries: Provides traceable documentation for each incident to support compliance and review
Source: Torq HyperSOC
3. Dropzone AI
Dropzone AI delivers autonomous AI SOC analysts that replicate the behavior and investigative techniques of top-tier human analysts to manage and resolve every incoming alert. It automates Tier-1 alert triage and investigation, generating high-fidelity reports with supporting evidence. The platform integrates into existing SOC workflows to provide a scalable, always-on investigation layer that frees human analysts from routine work.
General features include:
- Autonomous Tier-1 alert handling: Investigates every alert upon ingestion, with no need for manual triage
- Evidence-based reporting: Produces detailed investigation summaries with linked context and decision paths
- Simple integration: Deploys in under a day, requiring minimal setup to begin processing alerts
- Human-in-the-loop design: Analysts can customize investigation logic, approve actions, and review findings
Enterprise features include:
- 24/7 coverage and scalability: Provides round-the-clock alert processing without increasing analyst headcount
- Reduced triage workload: Cuts alert queues by over 90%, enabling teams to focus on critical threats
- Faster investigations: Shrinks investigation time from hours to minutes through automated enrichment and correlation
- Adaptability to environment: Learns over time based on customer-specific feedback and environment context
Source: DropZone AI
4. Stellar Cyber
Stellar Cyber is an AI-driven SOC platform that delivers open extended detection and response (Open XDR) to unify and automate threat detection, investigation, and response across the IT environment. By integrating data from network, endpoint, cloud, and other sources, Stellar Cyber eliminates silos and applies machine learning to correlate events and reduce false positives.
General features include:
- Open XDR architecture: Integrates and correlates data from network, endpoint, cloud, and identity tools
- Interflow event modeling: Builds actionable records by linking related events across the cyber kill chain
- Automated triage and response: Uses AI to reduce false positives and accelerate containment workflows
- Multi-layer AI: Combines different AI models to identify threats, hunt anomalies, and guide investigations
Enterprise features include:
- Centralized visibility: Delivers a unified view of all security data via a single pane of glass
- Cross-environment support: Handles data from on-premises, cloud, and containerized environments
- Reduced analyst fatigue: Automates repetitive tasks and improves signal-to-noise ratio for alerts
- Fast training and adoption: GUI follows the cyber kill chain to help new analysts become effective quickly
5. Prophet Security
Prophet Security delivers an agentic AI SOC platform to improve the detection, investigation, and response lifecycle. Acting as a force multiplier for security teams, Prophet combines multiple AI-driven agents that replicate expert analyst behavior: triaging alerts, performing investigations, and providing actionable recommendations.
General features include:
- Agentic AI SOC analyst: Investigates alerts autonomously with contextual enrichment and prioritization logic
- AI-powered threat hunter: Supports natural language queries for fast, targeted threat hunts across environments
- Detection advisor: Recommends improvements to noisy or ineffective detection rules
- Explainable automation: Provides visibility into each AI decision with supporting data and justifications
Enterprise features include:
- End-to-end alert coverage: Scales to investigate 100% of alert volume, across all severities
- Significant throughput gains: Improves SOC efficiency by 5–10x, reducing backlog and response delays
- Triage time reduction: Speeds up investigations by enriching and resolving alerts in minutes
- SOC integration: Compatible with existing tools, including SIEM, SOAR, EDR, and cloud platforms
Enterprise Considerations for Choosing AI SOC Solutions
Selecting the right AI SOC platform requires more than just reviewing feature lists. It involves aligning the tool’s capabilities with organizational needs, infrastructure, and security maturity. Below are key considerations enterprises should weigh before adopting an AI SOC solution:
- Integration with existing tools and workflows: Ensure the platform can integrate with your existing security stack: SIEMs, EDRs, SOARs, firewalls, and cloud infrastructure. Poor integration can create data silos, reduce visibility, and increase manual effort.
- Support for enterprise-scale data volumes: AI SOC tools must handle high volumes of telemetry data across multiple environments without performance degradation. Evaluate the platform’s architecture for scalability and data ingestion limits.
- Transparency and explainability: Look for solutions that provide clear reasoning behind automated decisions, such as alert prioritization or response actions. Transparency is crucial for trust, auditability, and regulatory compliance.
- Customization and control: The ability to define triage policies, detection rules, and automation workflows tailored to your environment is essential. Rigid, one-size-fits-all systems may not adapt well to unique operational requirements.
- Human-in-the-loop support: While automation is key, platforms should allow human analysts to intervene, review, and override decisions when needed. This ensures operational flexibility and safety in sensitive environments.
- Deployment and maintenance requirements: Consider whether the solution is cloud-native, on-premises, or hybrid, and assess the complexity of deployment, updates, and ongoing management. Simpler setups can reduce time to value.
- Vendor maturity and support: Evaluate the vendor’s track record, customer support quality, and commitment to product updates. Mature vendors often provide better documentation, training, and support for enterprise environments.
- Security and compliance posture: The platform itself should adhere to strong security practices and support compliance requirements relevant to your industry (e.g., SOC 2, ISO 27001, GDPR).
- Cost and licensing model: Analyze total cost of ownership, including licensing, infrastructure, and staff time. Some platforms offer consumption-based pricing, which may be more cost-effective for dynamic environments.
AI SOC for the Enterprise with Radiant Security’s Agentic AI
Radiant Security is an Agentic AI SOC platform that automates alert triage, investigation, and response across the security lifecycle. The platform is designed to reduce false positives by roughly 90%, enabling analysts to spend more time on verified threats rather than manual triage. Radiant also aims to shorten investigation and response times (MTTR) and lower operational costs, while helping teams avoid the fatigue that often comes with high alert volume.
Key capabilities include:
- Agentic AI triage and investigation for all alert types, including previously unseen or low-fidelity ones.
- Transparent reasoning that shows how and why the AI reached its conclusions, helping analysts validate decisions and build trust.
- Integrated response with one-click, executable action plans that can be carried out manually or automated when appropriate.
- Log management with unlimited retention, delivered at a cost significantly lower than traditional SIEM platforms.
- AI feedback loop that allows teams to influence and adjust triage behavior using environmental context, improving accuracy over time.
Radiant provides a unified environment for handling alerts, investigations, response actions, and log data, with an emphasis on efficiency, clarity, and analyst control.

